- Apr 5, 2014
- 6,008
Doctor Web analysts have detected, within the Android.Xiny family, new species of Trojans designed to download and delete various programs. These Trojans can now infect the processes of system applications and download malicious plug-ins into the programs they have attacked.
Anti-virus specialists have been acquainted with the Android.Xiny Trojans since March 2015. As Doctor Web announced earlier, virus makers actively distribute them through popular websites offering downloadable software and even through official application stores like Google Play.
Once saved to smartphones and tablets, Android.Xiny Trojans attempt to acquire root privileges so that they can silently download and install various software programs. Moreover, they can display annoying advertisements. One key feature of these malicious programs is that they employ an innovative mechanism that protects them from being deleted. The mechanism is based on the fact that the Trojan’s apk files are made to be immutable. However, cybercriminals kept improving Android.Xiny Trojans and gave them the ability to inject themselves into system applications in order to launch various malicious plug-ins from them.
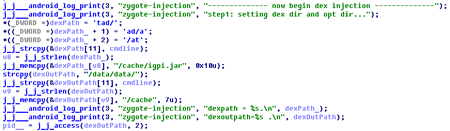
One of these upgraded Trojans examined by Doctor Web security researchers was named Android.Xiny.60. It gets installed in a system directory by other programs belonging to the Android.Xiny family. Once launched, Android.Xiny.60 extracts several malicious components from its resource folder and copies them to system directories.
Once the zygote process is infected, Android.Xiny.62 starts tracking the launch of any new applications. As a result, if the Trojan detects a newly launched process, it injects the igpi.jar malicious module (Android.Xiny.60) into it. This very same module is also injected after system processes of Google Play and Google Play Services applications have been infected.
The igpi.jar module’s main job is to download cybercriminal-specified plug-ins and launch them in the infected environment. The module monitors a mobile device’s status and, when certain system events occur (e.g. home screen activity, change in network connection, charger usage, etc.), it connects to the command and control server and sends it the following information about the infected device:
Anti-virus specialists have been acquainted with the Android.Xiny Trojans since March 2015. As Doctor Web announced earlier, virus makers actively distribute them through popular websites offering downloadable software and even through official application stores like Google Play.
Once saved to smartphones and tablets, Android.Xiny Trojans attempt to acquire root privileges so that they can silently download and install various software programs. Moreover, they can display annoying advertisements. One key feature of these malicious programs is that they employ an innovative mechanism that protects them from being deleted. The mechanism is based on the fact that the Trojan’s apk files are made to be immutable. However, cybercriminals kept improving Android.Xiny Trojans and gave them the ability to inject themselves into system applications in order to launch various malicious plug-ins from them.
One of these upgraded Trojans examined by Doctor Web security researchers was named Android.Xiny.60. It gets installed in a system directory by other programs belonging to the Android.Xiny family. Once launched, Android.Xiny.60 extracts several malicious components from its resource folder and copies them to system directories.
- /system/xbin/igpi;
- /system/lib/igpld.so;
- /system/lib/igpfix.so;
- /system/framework/igpi.jar.
Once the zygote process is infected, Android.Xiny.62 starts tracking the launch of any new applications. As a result, if the Trojan detects a newly launched process, it injects the igpi.jar malicious module (Android.Xiny.60) into it. This very same module is also injected after system processes of Google Play and Google Play Services applications have been infected.
The igpi.jar module’s main job is to download cybercriminal-specified plug-ins and launch them in the infected environment. The module monitors a mobile device’s status and, when certain system events occur (e.g. home screen activity, change in network connection, charger usage, etc.), it connects to the command and control server and sends it the following information about the infected device:
- IMEI
- IMSI
- MAC address of the network adapter
- OS version
- Mobile device model;
- Current system language
- Application package name
- If Android.Xiny.60 infects a Google Play process, it will download into it the software-installation module.
- If Android.Xiny.60 infects a messenger, it will be able to intercept and send messages.
- If Android.Xiny.60 infects a banking program’s process, it will launch the required plug-in and will then be able to steal confidential information, such as logins, passwords, credit card numbers, etc., and even covertly transfer money to cybercriminal-owned bank accounts.