- Apr 5, 2014
- 6,008
Doctor Web specialists are revealing new details about their investigation into BackDoor.Dande’s attack on drugstores and pharmaceutical companies. The company’s security researchers have determined that the backdoor not only loaded itself onto targeted workstations as an ePrica application component but also was embedded into one of that program’s early installer versions.
Doctor Web first reported BackDoor.Dande’s attack on drugstores and pharmaceutical companies in 2011. This backdoor was stealing medication procurement information from users of online drug ordering systems. Such programs are used in the pharmaceutical industry so the malicious application’s spread was of a highly specialized nature. During the past several years, our specialists have researched this backdoor and its methods of infecting computers.
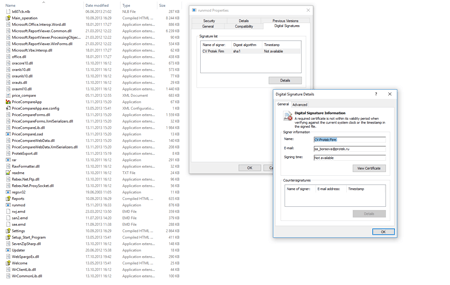
Recent research results have shown that an ePrica component was downloading and launching the Trojan onto targeted systems. Drugstore managers use this software component to analyze drug prices and choose the best suppliers. This module downloaded the BackDoor.Dande installer from a server belonging to “Spargo Tekhnologii”, and this installer then launched the backdoor on attacked computers. In addition, the indicated module had the digital signature “Spargo”.
A further analysis of the application showed that BackDoor.Dande components were embedded directly into one of the earlier versions of the ePrica installer, which could indicate that the developer’s security system has been seriously undermined. The ePrica application has NLB and EMD plugins that are dynamic DLL libraries encrypted with a private key. Among them are the backdoor installer and modules used to collect medication procurement information. These modules obtain the needed data from the databases of drugstore programs. One of the modules was used to copy pharmaceutical product procurement information from 1C databases.
The module runmod.exe executes the launch of these plugins. It takes action when the server commands it to decrypt and launch them into the memory. After that they copy database information which is then sent to a remote server. The indicated application component is signed with the certificate “Protek”—a group of companies that includes “Spargo Tekhnologii”, ePrica’s developer.
It is important to note that even after ePrica is removed, the backdoor stays in the system and continues to spy on users. It is possible that BackDoor.Dande is still present on the computers of users who have removed ePrica.
Its installer version 4.0.14.6, in which the Trojan modules were found, was released on November 18, 2013, while some of the backdoor’s files date back to 2010. Thus, the copying of drugstore and pharmaceutical company procurement information could have started at least a year before the backdoor was first detected.
More detailed information on the ePrica installer containing BackDoor.Dande is available in our virus library.
Doctor Web first reported BackDoor.Dande’s attack on drugstores and pharmaceutical companies in 2011. This backdoor was stealing medication procurement information from users of online drug ordering systems. Such programs are used in the pharmaceutical industry so the malicious application’s spread was of a highly specialized nature. During the past several years, our specialists have researched this backdoor and its methods of infecting computers.
Recent research results have shown that an ePrica component was downloading and launching the Trojan onto targeted systems. Drugstore managers use this software component to analyze drug prices and choose the best suppliers. This module downloaded the BackDoor.Dande installer from a server belonging to “Spargo Tekhnologii”, and this installer then launched the backdoor on attacked computers. In addition, the indicated module had the digital signature “Spargo”.
A further analysis of the application showed that BackDoor.Dande components were embedded directly into one of the earlier versions of the ePrica installer, which could indicate that the developer’s security system has been seriously undermined. The ePrica application has NLB and EMD plugins that are dynamic DLL libraries encrypted with a private key. Among them are the backdoor installer and modules used to collect medication procurement information. These modules obtain the needed data from the databases of drugstore programs. One of the modules was used to copy pharmaceutical product procurement information from 1C databases.
The module runmod.exe executes the launch of these plugins. It takes action when the server commands it to decrypt and launch them into the memory. After that they copy database information which is then sent to a remote server. The indicated application component is signed with the certificate “Protek”—a group of companies that includes “Spargo Tekhnologii”, ePrica’s developer.
It is important to note that even after ePrica is removed, the backdoor stays in the system and continues to spy on users. It is possible that BackDoor.Dande is still present on the computers of users who have removed ePrica.
Its installer version 4.0.14.6, in which the Trojan modules were found, was released on November 18, 2013, while some of the backdoor’s files date back to 2010. Thus, the copying of drugstore and pharmaceutical company procurement information could have started at least a year before the backdoor was first detected.
More detailed information on the ePrica installer containing BackDoor.Dande is available in our virus library.