- Sep 3, 2017
- 825
- Content source
- https://news.drweb.com/show/?lng=en&i=12590&c=9
May 14, 2018
In late March Doctor Web reported the spreading of a Trojan that stole files and other confidential information from infected devices. Our virus analysts researched several new modifications of this malicious program and identified its developer.
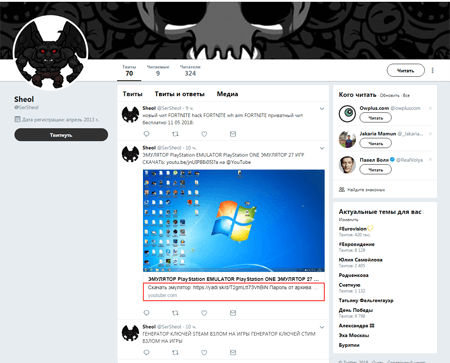
Doctor Web specialists researched several new modifications of Trojan.PWS.Stealer.23012 distributed via links in the comments section of YouTube videos. These videos focused on using special programs that made playing computer games easier. Such programs are called cheats and trainers. The cybercriminals disguised the Trojan as these applications and distributed it by leaving comments to videos with a link to Yandex.Disk from fake accounts. These malicious links were also extensively advertised on Twitter.
All researched modifications of the spyware were written in Python and transformed into an executable file using py2exe. One of new versions of the malicious program, which was dubbed Trojan.PWS.Stealer.23370, scans the discs of the infected device, searching for saved passwords and cookies files of Chromium-based browsers. In addition, this Trojan steals information from Telegram, FileZilla FTP client, and also copies images and office documents according to a preliminary specified list. The Trojan packs the obtained data into an archive and saves it to Yandex.Disk.
Another modification of this spying Trojan was named Trojan.PWS.Stealer.23700. This malicious program steals passwords and cookies files from Google Chrome, Opera, Yandex.Browser, Vivaldi, Kometa, Orbitum, Comodo, Amigo and Torch. It also copies the SSFN files from the config subfolder of Steam and other data required for accessing the Telegram account. In addition, the spyware creates copies of images and documents stored on the Windows Desktop. All stolen information is packed into an archive and loaded onto the cloud storage pCloud.
The third spyware modification was named Trojan.PWS.Stealer.23732. This Trojan’s dropper is written in Autoit. It saves several applications on a disc and launches them. These applications are the malicious program’s components. All researched modifications of the spyware were written in Python and transformed into an executable file. It steals confidential information from infected devices. All the other Trojan components are written in Go. One of them scans discs searching for folders where browsers are installed, and another one packs stolen data into archives and loads them onto the pCloud storage.
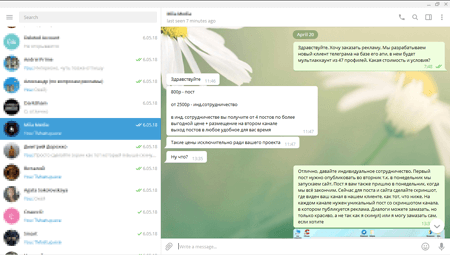
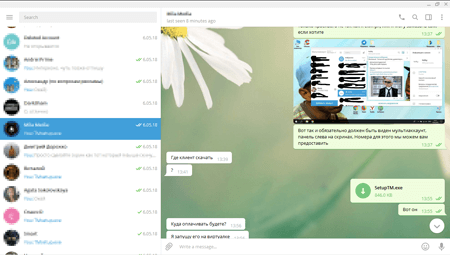
To distribute this stealer’s modification, cybercriminals who bought it from the virus writer came up with one more creative method. Cybercriminals got in touch with the administrators of themed Telegram channels and invited them to write a post on a new program allegedly developed by them and suggested testing it. According to the cybercriminals, this program allowed them to simultaneously connect to several Telegram accounts on one computer. When in reality a potential victim was invited to download the spying Trojan disguised as a useful application.
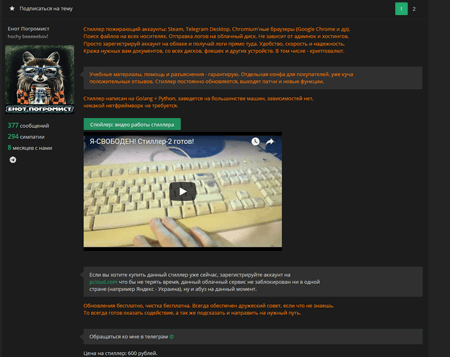
In the code of these spying Trojans, virus analysts found information that allowed them to identify the author of the malicious programs. The virus writer is disguised under the name of “Yenot Pogromist”. He not only develops Trojans, but also sells them on a popular website.
The creator of spyware also has a YouTube channel dedicated to developing malicious software and has his own GitHub page where he posts the source code of his malicious programs.
Doctor Web specialists analyzed the data of open sources and identified several of the Trojan developer’s e-mails and mobile number connected to the Telegram channel used for illegal actions. In addition, they were able to find a batch of domains used by the virus writer to spread malicious programs and to identify his city of residence. The scheme below shows a portion of the identified connection of “Yenot Pogromist” with the technical sources he uses.
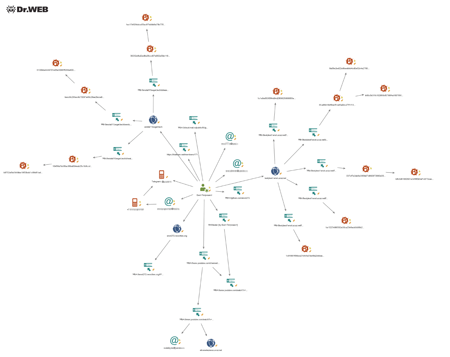
The login credentials of cloud storages, where archives with stolen files go, are wired into the Trojans’ bodies. It allows them to easily identify all clients of “Yenot Pogromist” who bought malicious software from him. They are primarily citizens of Russia and Ukraine. Some of them used e-mail addresses that allow them to easily discover their pages on social networks and their true identities. For example, Doctor Web specialists detected that many clients of “Yenot Pogromist” also use other spyware sold on underground forums. It is also worth mentioning that some buyers turned out to be so clever that they launched the spyware on their own computers, perhaps they did it in attempts to assess its operation. As a result, their personal files were loaded onto the cloud storages. Any Trojan researcher can easily retrieve their access data from the Trojan’s body.
Doctor Web specialists would like to remind its clients that using and distributing malicious programs is a crime punishable under Criminal Code 273 of the Russian Federation with possible imprisonment up to four years. Buyers and users of the spying Trojans are subject to Criminal Code 272 of the Russian Federation “Illegal access to computer information”.
In late March Doctor Web reported the spreading of a Trojan that stole files and other confidential information from infected devices. Our virus analysts researched several new modifications of this malicious program and identified its developer.
Doctor Web specialists researched several new modifications of Trojan.PWS.Stealer.23012 distributed via links in the comments section of YouTube videos. These videos focused on using special programs that made playing computer games easier. Such programs are called cheats and trainers. The cybercriminals disguised the Trojan as these applications and distributed it by leaving comments to videos with a link to Yandex.Disk from fake accounts. These malicious links were also extensively advertised on Twitter.

All researched modifications of the spyware were written in Python and transformed into an executable file using py2exe. One of new versions of the malicious program, which was dubbed Trojan.PWS.Stealer.23370, scans the discs of the infected device, searching for saved passwords and cookies files of Chromium-based browsers. In addition, this Trojan steals information from Telegram, FileZilla FTP client, and also copies images and office documents according to a preliminary specified list. The Trojan packs the obtained data into an archive and saves it to Yandex.Disk.
Another modification of this spying Trojan was named Trojan.PWS.Stealer.23700. This malicious program steals passwords and cookies files from Google Chrome, Opera, Yandex.Browser, Vivaldi, Kometa, Orbitum, Comodo, Amigo and Torch. It also copies the SSFN files from the config subfolder of Steam and other data required for accessing the Telegram account. In addition, the spyware creates copies of images and documents stored on the Windows Desktop. All stolen information is packed into an archive and loaded onto the cloud storage pCloud.
The third spyware modification was named Trojan.PWS.Stealer.23732. This Trojan’s dropper is written in Autoit. It saves several applications on a disc and launches them. These applications are the malicious program’s components. All researched modifications of the spyware were written in Python and transformed into an executable file. It steals confidential information from infected devices. All the other Trojan components are written in Go. One of them scans discs searching for folders where browsers are installed, and another one packs stolen data into archives and loads them onto the pCloud storage.
To distribute this stealer’s modification, cybercriminals who bought it from the virus writer came up with one more creative method. Cybercriminals got in touch with the administrators of themed Telegram channels and invited them to write a post on a new program allegedly developed by them and suggested testing it. According to the cybercriminals, this program allowed them to simultaneously connect to several Telegram accounts on one computer. When in reality a potential victim was invited to download the spying Trojan disguised as a useful application.


In the code of these spying Trojans, virus analysts found information that allowed them to identify the author of the malicious programs. The virus writer is disguised under the name of “Yenot Pogromist”. He not only develops Trojans, but also sells them on a popular website.

The creator of spyware also has a YouTube channel dedicated to developing malicious software and has his own GitHub page where he posts the source code of his malicious programs.
Doctor Web specialists analyzed the data of open sources and identified several of the Trojan developer’s e-mails and mobile number connected to the Telegram channel used for illegal actions. In addition, they were able to find a batch of domains used by the virus writer to spread malicious programs and to identify his city of residence. The scheme below shows a portion of the identified connection of “Yenot Pogromist” with the technical sources he uses.

The login credentials of cloud storages, where archives with stolen files go, are wired into the Trojans’ bodies. It allows them to easily identify all clients of “Yenot Pogromist” who bought malicious software from him. They are primarily citizens of Russia and Ukraine. Some of them used e-mail addresses that allow them to easily discover their pages on social networks and their true identities. For example, Doctor Web specialists detected that many clients of “Yenot Pogromist” also use other spyware sold on underground forums. It is also worth mentioning that some buyers turned out to be so clever that they launched the spyware on their own computers, perhaps they did it in attempts to assess its operation. As a result, their personal files were loaded onto the cloud storages. Any Trojan researcher can easily retrieve their access data from the Trojan’s body.
Doctor Web specialists would like to remind its clients that using and distributing malicious programs is a crime punishable under Criminal Code 273 of the Russian Federation with possible imprisonment up to four years. Buyers and users of the spying Trojans are subject to Criminal Code 272 of the Russian Federation “Illegal access to computer information”.

