- Apr 5, 2014
- 6,008
On Friday, May 12, a myriad of computers all over the world were infected with a dangerous worm known as WannaCry. Doctor Web specialists are still examining this malware but are ready to share some of the results of their research.
The malware, known as WannaCry, is a network worm that infects computers running Microsoft Windows without any user involvement. Dr.Web Anti-virus detects all the worm’s components as Trojan.Encoder.11432. It started being spread around 10 a.m. on May 12, 2017. The worm attacks all the computers in a local network and remote Internet servers with random IP addresses, attempting to establish a connection with port 445. After infecting a computer, the worm tries to independently infect other available machines—this explains the massive scale of the outbreak. The malicious program itself has several components; the encryption Trojan is only one of them.
Network worm
Once launched, the worm attempts to send a request to the remote server whose domain is stored inside the Trojan. If a response to this request is received, the worm shuts itself down. Some media sources have reported that the WannaCry outbreak was stopped once this domain was registered: up to the moment the Trojan started being spread, the domain was available due to a mistake made by the cybercriminals. In reality, the analysis of the Trojan shows that it will operate and infect computers that are connected to a local network but have no Internet connection. Thus, it is too early to talk about the epidemic being over.
After being launched, the Trojan registers itself as a system service named mssecsvc2.0. In addition, the worm is sensitive to command line parameters: if an argument is indicated, it attempts to enable an automatic restart of the service in case an error occurs. Within 24 hours after it is launched as a system service, the worm automatically shuts itself down.
After successfully starting up on an infected machine, the worm starts checking for servers that it can access in the infected machine’s local network and for computers on the Internet that have random IP addresses. It tries to connect to port 445. If the connection is successfully established, the worm attempts to infect these computers using a vulnerability in the SMB protocol.
Dropper
A dropper is a component designed to install a malicious executable file into an operating system. WannaCry’s dropper contains a massive password-protected ZIP archive, which contains an encrypted file with a Trojan encoder, Windows Desktop wallpaper containing the cybercriminals’ demands, a file containing the addresses of onion servers and the name of a wallet for Bitcoin transactions, and also an archive containing programs for operating in the Tor network. The dropper is launched from the worm’s body, installs itself in the system, and then attempts to launch its copy as a randomly named system service. If this attempt is unsuccessful, it is executed as an ordinary program. The dropper’s main task is to save the contents of the archive on the disk and launch the encryptor.
A ransomware Trojan
Trojan.Encoder.11432 encrypts files with a random key. The file stores data on the length of the encrypted key, the encrypted key itself, information about the type of encryption, and the size of the source file. During the course of encryption, a file named f.wnry is created—it stores the list of files for the Trojan to decrypt in test mode.
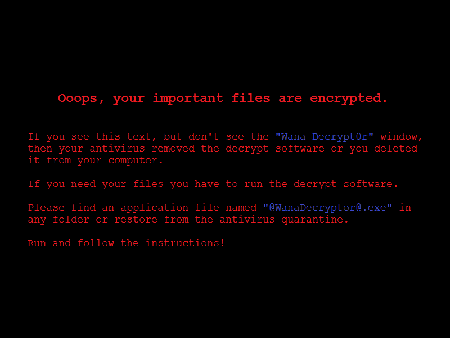
The Trojan contains the author’s decoder, which deletes shadow copies on the infected computer and disables the system restore function. It changes the Windows Desktop wallpaper to a graphic file that reads as follows:
Then it unpacks the applications it uses to operate with the Tor network (or downloads them from the Web) and connects to onion servers, the addresses of which are indicated in the Trojan’s configuration. From there it receives the name of the wallet accepting Bitcoin electronic currency and writes it into the configuration. To exchange data with the onion servers, Trojan.Encoder.11432 uses its own protocol.
The decoder permits the decryption of several test files, the list of which is stored in the file f.wnry. The private key needed to decrypt them is stored in one of the malicious program’s components. So it is possible to decrypt them even without using the Trojan. However, the test files and all the other files are decrypted with different keys. Therefore, there is no guarantee that the data corrupted by the encoder can be restored successfully, even if a ransom is paid.
Unfortunately, at present it is impossible to decrypt files encoded by Trojan.Encoder.11432.
Signs of infection
The hallmark signs of a WannaCry infection are:
The malware, known as WannaCry, is a network worm that infects computers running Microsoft Windows without any user involvement. Dr.Web Anti-virus detects all the worm’s components as Trojan.Encoder.11432. It started being spread around 10 a.m. on May 12, 2017. The worm attacks all the computers in a local network and remote Internet servers with random IP addresses, attempting to establish a connection with port 445. After infecting a computer, the worm tries to independently infect other available machines—this explains the massive scale of the outbreak. The malicious program itself has several components; the encryption Trojan is only one of them.
Network worm
Once launched, the worm attempts to send a request to the remote server whose domain is stored inside the Trojan. If a response to this request is received, the worm shuts itself down. Some media sources have reported that the WannaCry outbreak was stopped once this domain was registered: up to the moment the Trojan started being spread, the domain was available due to a mistake made by the cybercriminals. In reality, the analysis of the Trojan shows that it will operate and infect computers that are connected to a local network but have no Internet connection. Thus, it is too early to talk about the epidemic being over.
After being launched, the Trojan registers itself as a system service named mssecsvc2.0. In addition, the worm is sensitive to command line parameters: if an argument is indicated, it attempts to enable an automatic restart of the service in case an error occurs. Within 24 hours after it is launched as a system service, the worm automatically shuts itself down.
After successfully starting up on an infected machine, the worm starts checking for servers that it can access in the infected machine’s local network and for computers on the Internet that have random IP addresses. It tries to connect to port 445. If the connection is successfully established, the worm attempts to infect these computers using a vulnerability in the SMB protocol.
Dropper
A dropper is a component designed to install a malicious executable file into an operating system. WannaCry’s dropper contains a massive password-protected ZIP archive, which contains an encrypted file with a Trojan encoder, Windows Desktop wallpaper containing the cybercriminals’ demands, a file containing the addresses of onion servers and the name of a wallet for Bitcoin transactions, and also an archive containing programs for operating in the Tor network. The dropper is launched from the worm’s body, installs itself in the system, and then attempts to launch its copy as a randomly named system service. If this attempt is unsuccessful, it is executed as an ordinary program. The dropper’s main task is to save the contents of the archive on the disk and launch the encryptor.
A ransomware Trojan
Trojan.Encoder.11432 encrypts files with a random key. The file stores data on the length of the encrypted key, the encrypted key itself, information about the type of encryption, and the size of the source file. During the course of encryption, a file named f.wnry is created—it stores the list of files for the Trojan to decrypt in test mode.
The Trojan contains the author’s decoder, which deletes shadow copies on the infected computer and disables the system restore function. It changes the Windows Desktop wallpaper to a graphic file that reads as follows:
Then it unpacks the applications it uses to operate with the Tor network (or downloads them from the Web) and connects to onion servers, the addresses of which are indicated in the Trojan’s configuration. From there it receives the name of the wallet accepting Bitcoin electronic currency and writes it into the configuration. To exchange data with the onion servers, Trojan.Encoder.11432 uses its own protocol.
The decoder permits the decryption of several test files, the list of which is stored in the file f.wnry. The private key needed to decrypt them is stored in one of the malicious program’s components. So it is possible to decrypt them even without using the Trojan. However, the test files and all the other files are decrypted with different keys. Therefore, there is no guarantee that the data corrupted by the encoder can be restored successfully, even if a ransom is paid.
Unfortunately, at present it is impossible to decrypt files encoded by Trojan.Encoder.11432.
Signs of infection
The hallmark signs of a WannaCry infection are:
- The presence of the mssecsvc2.0 system service (visible name—”Microsoft Security Center (2.0) Service”);
- The presence of the Trojan encoder file C:\WINDOWS\tasksche.exe; the previous sample of the malicious program is stored in the file C:\WINDOWS\qeriuwjhrf.
- To prevent the further spread of infection, isolate infected machines and PCs containing valuable data from computer networks;
- Save a backup copy of the information on separate storages that must thereafter remain disconnected from any computers.