There has been quite a discussion regarding Google’s recent introduction of .zip, .mov, .phd (and other variations) as top-level domains (TLDs). The opinions in the cybersecurity community can be distilled into two camps. A fair number of experts assume that this move from Google will likely cause even more confusion for non-tech savvy users navigating the internet. The second camp thinks otherwise. That it basically is a difficult realm to navigate in already and that users rarely pay attention to the URL and its components. When digging into this topic and our data, we identified that cybercriminals have already started abusing .zip domains to mislead users into thinking they are downloadable files, instead of URLs. Our research shows that out of the top 30 .zip domains blocked by our threat detection engines, one third abuses names of leading tech companies such as Microsoft, Google, Amazon and Paypal, to trick people into thinking that they are files of trusted companies.
In the early days of the internet, TLDs were introduced to streamline the process of browsing and sorting through online content. The main reason for using domain names and TLDs was to make navigation around the web more user friendly. Also, at the time geographical location was also important. The well.sf.ca.us, originally
pointed out by Ars Technica, is a great example of using the TLD to denote its geographical location, in this case San Francisco, California, in the United States of America. It also helps us distinguish the basic nature of the server we are visiting. .com, associated with the commercial nature of a website, and .org, associated with nonprofits, are probably the most common TLDs used to denote the characteristics of a domain.
According to Statista, .org and .com account for 50% of all TLDs worldwide.
The purpose of TLDs has become much more blurred recently (past several years). They can also serve as part of branding efforts now, such as the .lidl or .edeka TLD or other exotic TLDs that come to my mind. For example, .beer, .motorcycles, .plumbing, .soccer, .taxi, and so on. There’s little that isn’t achievable. When the Internet Corporation for Assigned Names and Numbers (ICANN), the non-profit which oversees and manages unique Internet identifiers, like IP addresses and domains, last expanded the scope of TLDs,
they set the evaluation fee at $185,000, limiting applicants to only established entities, whether public or private. It’s undeniably a high-priced venture.
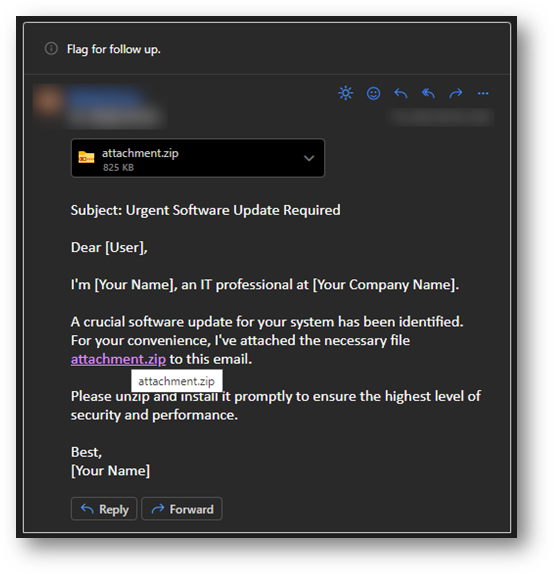
So, what issues could arise with a .zip TLD? Personally, I see a significant concern in the potential for file confusion and the consequent difficulty distinguishing between local and remote sources, which could pose a security threat. For educational purposes I crafted a prototype email that leverages the fact that the attachment and the link can point to completely different locations.
Email that the attacker might have crafted for use
It appears that using a .zip domain to deceive users can be remarkably easy. Moreover, the link preview can be manipulated to hide the protocol used, such as HTTP(S). This definitely helps the attacker to lure the user where they want.
It seems that we have reached a point where the original purpose of making URLs understandable to the public is gradually deteriorating over time. Which address seems more suspicious to you: https://52.144.44[.]169 or latestupdate[.]zip (which resolves to that IP)? I have my doubts as well. I do not imply that most of the .zip domains are or will be inherently malicious. However, I foresee a certain number of domains that, if not registered by entities closely related to their respective products, are very unlikely to be used for legitimate purposes. Looking at the top blocked domains by Avast with a .zip TLD we see that there are many mimicking legitimate companies. Also, there is a second group that tries to imitate files.

The most interesting domains are those that are closely related to large service providers, which are well known to the public. These include microsoft-office[.]zip, microsoft[.]zip, csgo[.]zip, google-drive[.]zip, microsoftonedrive[.]zip, googlechrome[.]zip, and amazons3[.]zip. Other perfect examples that I would describe as well designed are those with a pdf keyword combined with a subdomain. Namely 226x227.pdf[.]zip, 2023-05.pdf[.].zip, cv3.pdf[.]zip, temp1_rsbu_12m2021.pdf[.]zip. Checking on who.is yields expected results.
Whois record for attachment.zip
Most of the time, when a registrant’s information is redacted from the WHOIS database..........................................