L
LabZero
Thread author
Hello.
This is a simple malware analysis performed in dynamic mode using Sandboxie and SysAnalyzer.
Honestly, as the title, the malware that I have chosen is not "random" because first to analyze it, I tested in Sandboxie at least a dozen of samples.
The problem is that these samples using anti-virtualization and anti-sandboxing routines.
In this case, the malware recognises the sandbox and start Itself for 1 second and then it terminates the processes, remaining dormant.
This technique is widely used to prevent or make difficult the analysis and the purpose of the malicious code is infecting the real/physical machine.
The purpose of this thread is to show that to analyze a malware is not always necessary to have advanced knowledge or sophisticated tools.
As always, I remind everyone to use a virtual environment for malware testing.
In this case, I run Sandboxie, which offers a good security level, although to perform specific and complex analysis, I use a VM.
File Details
File Name: 02bb3774d0fa83d86239ab5d10f7bcd0.exe
File Size: 163840 bytes
File Type: PE32 executable (GUI) Intel 80386, for MS Windows
MD5: 02bb3774d0fa83d86239ab5d10f7bcd0
Online analysis: Malwr - Malware Analysis by Cuckoo Sandbox
Containment: Sandboxie 5.0.10 x64
OS: Windows 7 Pro x64 SP1
Tools: SysAnalyzer
Description from source: SysAnalyzer - aldeid
SysAnalyzer is an automated mal-code run time analysis application that monitors various aspects of system and process states and It was designed to enable analysts to quickly build a comprehensive report as to the actions a binary takes on a system.
SysAnalyzer can automatically monitor and compare:
- Running Processes
- Open Ports
- Loaded The Drivers
- Injected Libraries
- Key Registry Changes
- APIs called by a target process
- File Modifications
- HTTP, IRC, and DNS traffic
SysAnalyzer also comes with a ProcessAnalyzer tool which can perform the following tasks:
- Create a memory dump of target process
- Parse memory dump for strings
- Parse strings output for exe, reg, and url references
- Scan memory dump for known exploit signatures
Full GPL source for SysAnalyzer is included in the installation package.
Starting SysAnalyzer, it is necessary to indicate the location of the sample and press START.
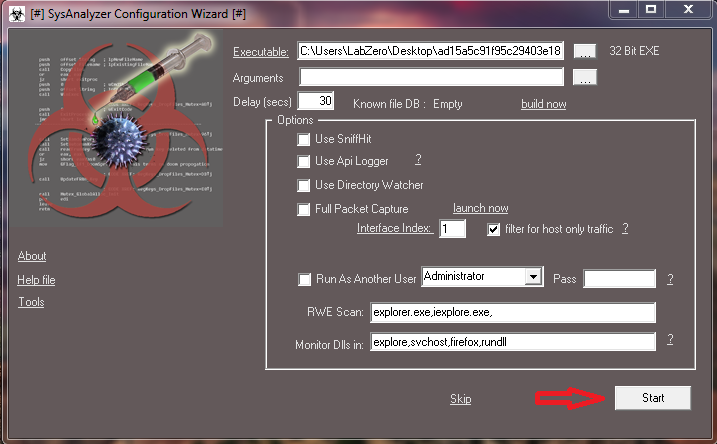
Be careful, the malware is executed after a countdown of 30 seconds
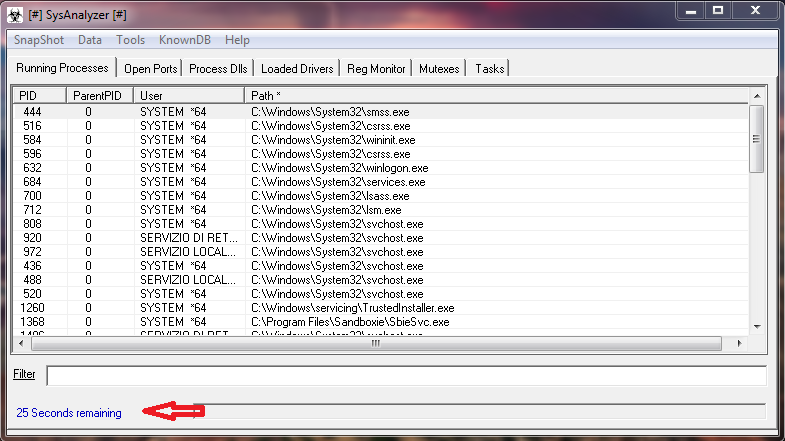
In the main interface, we see "debug log" that indicates all the operations performed by the tool: enumerating processes, open ports, drivers, reg keys and running the malware, the subsequent operations.
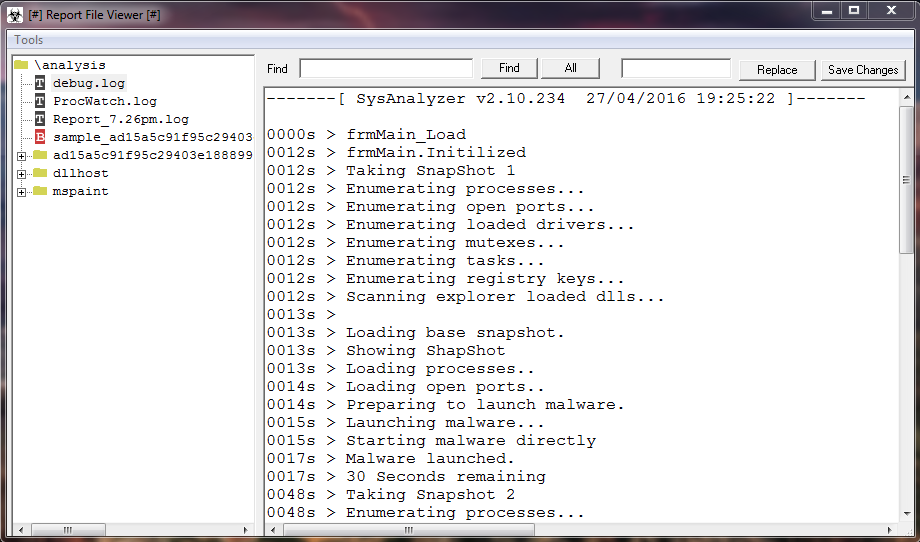
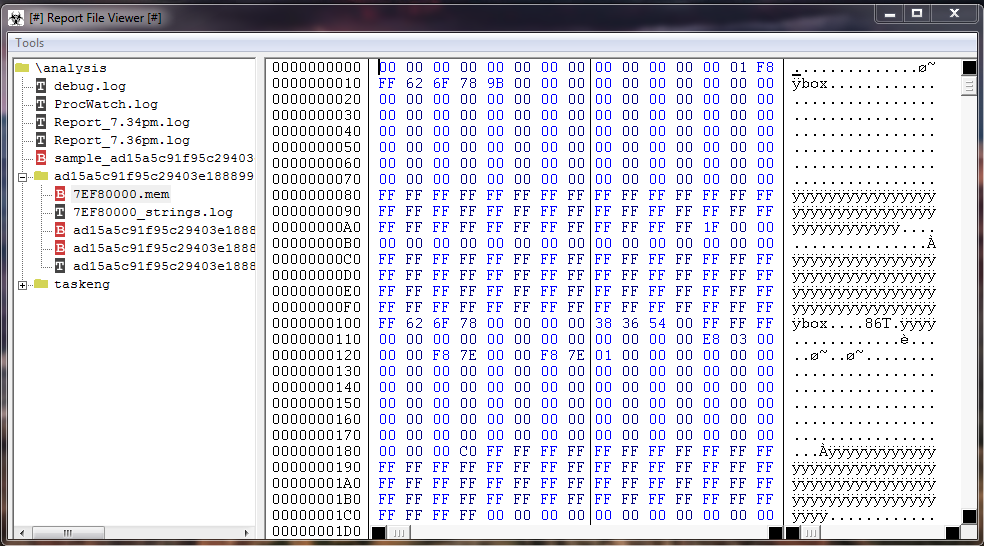
It is interesting to note: the "memory dump of target process".
Any file is stored on disk in the form of a sequence of bytes, so in the form of binary values of 8 bit, for this reason, the files that are stored on the disk are defined generically, a binary file.
High level's programming languages, however, distinguish between binary files and text files, but this distinction is formal.
This particular type of view of the binary information present on any storage media (hard disk, RAM, etc), is also called memory dump.
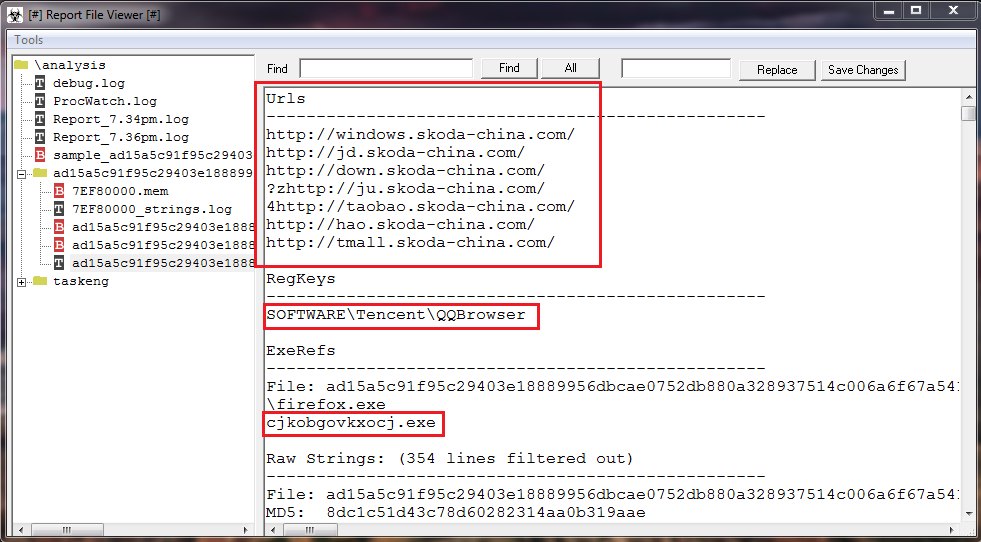
Without doubt the most interesting information: "contacted URLs", "registry keys" that refer to QQBrowser and "exe references" that show probably a dropped file.
The latter information is important because we can try to really understand what actions the malware performs on the system.
In this case, by analyzing the network communication, we can note that they are different from those analyzed by Malwr.
Probably the reason is that SysAnalyzer has analyzed only the main sample as a "container" that contact the URLs in our analysis.
Considering that this container drops another executable, the Malwr analysis may detect other connections generated by this last.
Moreover, the behavior of a malware can change on different OS about routines, algorithms.
In short, according to my analysis this samples is a classic trojan that seems to run the adware that opens ads pages, but it drops one or more malicious .exe that might steal personal information or other.
Of course this is a very simple analysis, understandable to everyone, but it is useful to try to understand how a malware works.
This is a simple malware analysis performed in dynamic mode using Sandboxie and SysAnalyzer.
Honestly, as the title, the malware that I have chosen is not "random" because first to analyze it, I tested in Sandboxie at least a dozen of samples.
The problem is that these samples using anti-virtualization and anti-sandboxing routines.
In this case, the malware recognises the sandbox and start Itself for 1 second and then it terminates the processes, remaining dormant.
This technique is widely used to prevent or make difficult the analysis and the purpose of the malicious code is infecting the real/physical machine.
The purpose of this thread is to show that to analyze a malware is not always necessary to have advanced knowledge or sophisticated tools.
As always, I remind everyone to use a virtual environment for malware testing.
In this case, I run Sandboxie, which offers a good security level, although to perform specific and complex analysis, I use a VM.
File Details
File Name: 02bb3774d0fa83d86239ab5d10f7bcd0.exe
File Size: 163840 bytes
File Type: PE32 executable (GUI) Intel 80386, for MS Windows
MD5: 02bb3774d0fa83d86239ab5d10f7bcd0
Online analysis: Malwr - Malware Analysis by Cuckoo Sandbox
Containment: Sandboxie 5.0.10 x64
OS: Windows 7 Pro x64 SP1
Tools: SysAnalyzer
Description from source: SysAnalyzer - aldeid
SysAnalyzer is an automated mal-code run time analysis application that monitors various aspects of system and process states and It was designed to enable analysts to quickly build a comprehensive report as to the actions a binary takes on a system.
SysAnalyzer can automatically monitor and compare:
- Running Processes
- Open Ports
- Loaded The Drivers
- Injected Libraries
- Key Registry Changes
- APIs called by a target process
- File Modifications
- HTTP, IRC, and DNS traffic
SysAnalyzer also comes with a ProcessAnalyzer tool which can perform the following tasks:
- Create a memory dump of target process
- Parse memory dump for strings
- Parse strings output for exe, reg, and url references
- Scan memory dump for known exploit signatures
Full GPL source for SysAnalyzer is included in the installation package.
Starting SysAnalyzer, it is necessary to indicate the location of the sample and press START.
Be careful, the malware is executed after a countdown of 30 seconds
In the main interface, we see "debug log" that indicates all the operations performed by the tool: enumerating processes, open ports, drivers, reg keys and running the malware, the subsequent operations.
It is interesting to note: the "memory dump of target process".
Any file is stored on disk in the form of a sequence of bytes, so in the form of binary values of 8 bit, for this reason, the files that are stored on the disk are defined generically, a binary file.
High level's programming languages, however, distinguish between binary files and text files, but this distinction is formal.
This particular type of view of the binary information present on any storage media (hard disk, RAM, etc), is also called memory dump.
Without doubt the most interesting information: "contacted URLs", "registry keys" that refer to QQBrowser and "exe references" that show probably a dropped file.
The latter information is important because we can try to really understand what actions the malware performs on the system.
In this case, by analyzing the network communication, we can note that they are different from those analyzed by Malwr.
Probably the reason is that SysAnalyzer has analyzed only the main sample as a "container" that contact the URLs in our analysis.
Considering that this container drops another executable, the Malwr analysis may detect other connections generated by this last.
Moreover, the behavior of a malware can change on different OS about routines, algorithms.
In short, according to my analysis this samples is a classic trojan that seems to run the adware that opens ads pages, but it drops one or more malicious .exe that might steal personal information or other.
Of course this is a very simple analysis, understandable to everyone, but it is useful to try to understand how a malware works.