- Apr 21, 2016
- 4,377
The coronavirus pandemic has dealt a major blow to the global economy. Restrictive measures have forced many companies to suspend operations, and workers to take time off at their own expense. Attempting to mitigate the effects of the pandemic, governments worldwide are taking steps to support businesses and citizens through tax breaks, compensation schemes, stimulus checks, and the like.
In other words, money almost literally falling from the sky doesn’t necessarily sound like fantasy this year. However, if you receive an e-mail stating that you can claim a tidy sum as some sort of pandemic-related relief, don’t rush to celebrate. Governments are not the only ones promising financial aid. So too are fraudsters, but as you can guess, their promises lead to the opposite. Here are some examples of “support” that you definitely don’t want.
Free malware for everyone
A lot of spam these days uses pandemic-related payouts as bait to distribute malware. You might be asked to open an attachment or click on a link in the message to get at the promised funds.
For example, scammers targeting users in Brazil claim that the government has abolished electricity payments because of the pandemic. You can’t simply stop paying, though; first, you must register online using the link conveniently provided in the message.
Although the link seems to point to a government website, the e-mail sender’s address looks anything but official. If the recipient fails to smell the rat and clicks through, then Trojan loader Sneaky (our products identify it as Trojan-Downloader.OLE2.Sneaky.gen) is installed on the computer, and it then downloads and runs another Trojan.

The victim is invited to follow the link to stop paying for electricity. The sender’s address provides the first hint that the e-mail might not be legitimate
In another e-mail, cybercriminals preying on users in South Africa promise to pay compensation all summer — provided they fill out the attached form. The “form” turns out to be the SelfDel backdoor (Trojan.Win32.SelfDel.hoxq), which gives the attackers remote control over the victim’s computer.

To receive the promised compensation, users are asked to open the attached archive, which in fact contains malware
Scammers are also adept at imitating banks. Clients of one financial institution, for example, are prompted not only to open an attached archive supposedly with confirmation of the payout, but to log in to their account to check the transaction details. The real reason is so that the Noon Trojan (Trojan-Spy.MSIL.Noon.gen), concealed in the archive, can steal the username and password when the user rushes to log in to their bank account.

Instead of payout confirmation, the attached archive contains a banking Trojan
Good old phishing
Passwords and other data are sometimes easy to coax out of users without the help of malware. For example, we were struck by a “government” e-mail offering compensation to those aged 70 and up. This social group tends to be more susceptible to fraud than young people because many aren’t as well-versed in modern technology.
In addition, COVID-19 poses a greater health risk to older people, which is why in many countries they actually receive more subsidies than other age groups. The regrettable result is an almost perfect target. In this scam, the addressee is asked to fill out a form by clicking a link.

Scammers offering compensation to senior citizens
If the user is interested enough to click the link, they do indeed see a form asking for their first and last names, as well as social security number (SSN) and current address. Curiously, the form is seemingly aimed at US residents (other countries don’t use SSNs), but the Submit button (“Отправить”) is in Russian.
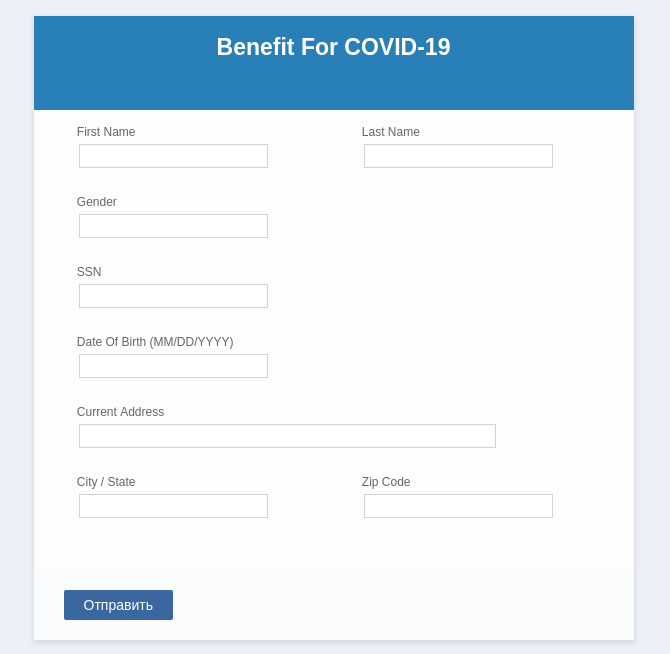
English-language scam with Submit button in Russian
Clicking the button forwards the information entered in the form to the scammers, who get an up-to-date database of elderly people with real addresses and SSNs.
After submitting the form, the user is taken to the official page of the genuine, WHO-backed COVID-19 Solidarity Response Fund, and invited to make a donation. This is an attempt by the attackers to add credibility to their scheme, as well as distract the victim from the original message. After all, no compensation from the government will be arriving.
Seeking corporate mailboxes
Scammers on the hunt for corporate mailboxes didn’t ignore the topic of anti-crisis measures, either. E-mails aimed at Spanish companies mention new tax breaks for businesses. Naturally, to find out if they can make a claim, recipients need to open a file by clicking a link — and not just read the document, but sign and return it. The victim is given one week to act.

A favorite trick is telling victims that time is short
Clicking the link redirects the user to a page asking for their e-mail username and password. If they try to log in to view the document, their credentials fall into the hands of the cybercriminals.
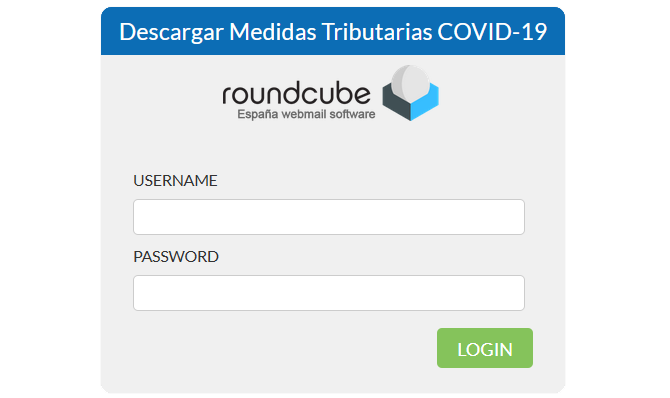
Cybercriminals want your e-mail credentials
Compensation from the WHO and China
You might also receive offers of assistance from international organizations and even other countries. Those foreign philanthropists sure seem to be generous. For example, a certain Kristalina Georgieva of the International Monetary Fund (IMF) is apparently handing out almost a million euros. The program to compensate those who must say at home during the pandemic is supposedly a joint initiative with the Chinese government.
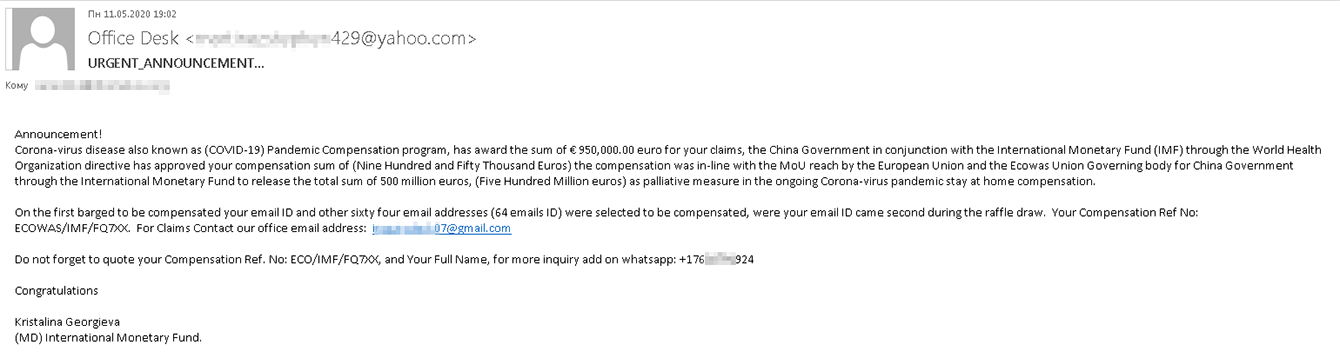
Scammers promise their victim €950,000 in compensation
To receive the money, they say, the victim has to contact the office using the Gmail address in the e-mail. Those who respond are likely to be kindly asked to pay some sort of processing fee, without which the transfer supposedly cannot go ahead.
In another e-mail, seemingly from the World Health Organization, the attached file is said to contain all the details needed to receive the compensation.

Scammers offer compensation on behalf of the World Health Organization
The document looks quite official, with a stamp, signatures, and the WHO emblem, although the authors clearly overdid the exclamation points in the header. The scammers promise the victim a whopping $150,000. They don’t explicitly say how to receive the money, but they mention they’ll require certain information and advise the recipient not to tell anyone about the e-mail “for reasons of security.” If you write to ask for more details, again, you will probably be badgered for money under one pretext or another.

“Official” notification of compensation from the WHO
How not to get burned trying to get the compensation
At this time of crisis, many people are in need of financial support. To avoid mistaking a scam for a real offer of assistance, always keep your wits about you.
Source
In other words, money almost literally falling from the sky doesn’t necessarily sound like fantasy this year. However, if you receive an e-mail stating that you can claim a tidy sum as some sort of pandemic-related relief, don’t rush to celebrate. Governments are not the only ones promising financial aid. So too are fraudsters, but as you can guess, their promises lead to the opposite. Here are some examples of “support” that you definitely don’t want.
Free malware for everyone
A lot of spam these days uses pandemic-related payouts as bait to distribute malware. You might be asked to open an attachment or click on a link in the message to get at the promised funds.
For example, scammers targeting users in Brazil claim that the government has abolished electricity payments because of the pandemic. You can’t simply stop paying, though; first, you must register online using the link conveniently provided in the message.
Although the link seems to point to a government website, the e-mail sender’s address looks anything but official. If the recipient fails to smell the rat and clicks through, then Trojan loader Sneaky (our products identify it as Trojan-Downloader.OLE2.Sneaky.gen) is installed on the computer, and it then downloads and runs another Trojan.

The victim is invited to follow the link to stop paying for electricity. The sender’s address provides the first hint that the e-mail might not be legitimate
In another e-mail, cybercriminals preying on users in South Africa promise to pay compensation all summer — provided they fill out the attached form. The “form” turns out to be the SelfDel backdoor (Trojan.Win32.SelfDel.hoxq), which gives the attackers remote control over the victim’s computer.

To receive the promised compensation, users are asked to open the attached archive, which in fact contains malware
Scammers are also adept at imitating banks. Clients of one financial institution, for example, are prompted not only to open an attached archive supposedly with confirmation of the payout, but to log in to their account to check the transaction details. The real reason is so that the Noon Trojan (Trojan-Spy.MSIL.Noon.gen), concealed in the archive, can steal the username and password when the user rushes to log in to their bank account.

Instead of payout confirmation, the attached archive contains a banking Trojan
Good old phishing
Passwords and other data are sometimes easy to coax out of users without the help of malware. For example, we were struck by a “government” e-mail offering compensation to those aged 70 and up. This social group tends to be more susceptible to fraud than young people because many aren’t as well-versed in modern technology.
In addition, COVID-19 poses a greater health risk to older people, which is why in many countries they actually receive more subsidies than other age groups. The regrettable result is an almost perfect target. In this scam, the addressee is asked to fill out a form by clicking a link.

Scammers offering compensation to senior citizens
If the user is interested enough to click the link, they do indeed see a form asking for their first and last names, as well as social security number (SSN) and current address. Curiously, the form is seemingly aimed at US residents (other countries don’t use SSNs), but the Submit button (“Отправить”) is in Russian.

English-language scam with Submit button in Russian
Clicking the button forwards the information entered in the form to the scammers, who get an up-to-date database of elderly people with real addresses and SSNs.
After submitting the form, the user is taken to the official page of the genuine, WHO-backed COVID-19 Solidarity Response Fund, and invited to make a donation. This is an attempt by the attackers to add credibility to their scheme, as well as distract the victim from the original message. After all, no compensation from the government will be arriving.
Seeking corporate mailboxes
Scammers on the hunt for corporate mailboxes didn’t ignore the topic of anti-crisis measures, either. E-mails aimed at Spanish companies mention new tax breaks for businesses. Naturally, to find out if they can make a claim, recipients need to open a file by clicking a link — and not just read the document, but sign and return it. The victim is given one week to act.

A favorite trick is telling victims that time is short
Clicking the link redirects the user to a page asking for their e-mail username and password. If they try to log in to view the document, their credentials fall into the hands of the cybercriminals.

Cybercriminals want your e-mail credentials
Compensation from the WHO and China
You might also receive offers of assistance from international organizations and even other countries. Those foreign philanthropists sure seem to be generous. For example, a certain Kristalina Georgieva of the International Monetary Fund (IMF) is apparently handing out almost a million euros. The program to compensate those who must say at home during the pandemic is supposedly a joint initiative with the Chinese government.

Scammers promise their victim €950,000 in compensation
To receive the money, they say, the victim has to contact the office using the Gmail address in the e-mail. Those who respond are likely to be kindly asked to pay some sort of processing fee, without which the transfer supposedly cannot go ahead.
In another e-mail, seemingly from the World Health Organization, the attached file is said to contain all the details needed to receive the compensation.

Scammers offer compensation on behalf of the World Health Organization
The document looks quite official, with a stamp, signatures, and the WHO emblem, although the authors clearly overdid the exclamation points in the header. The scammers promise the victim a whopping $150,000. They don’t explicitly say how to receive the money, but they mention they’ll require certain information and advise the recipient not to tell anyone about the e-mail “for reasons of security.” If you write to ask for more details, again, you will probably be badgered for money under one pretext or another.

“Official” notification of compensation from the WHO
How not to get burned trying to get the compensation
At this time of crisis, many people are in need of financial support. To avoid mistaking a scam for a real offer of assistance, always keep your wits about you.
- Apply for government support only on official websites. Do not follow links in e-mails, and do not open attachments. Instead, type the URL of the relevant agency into the browser, and check there if you’re entitled to compensation.
- Check the information in the e-mail: If you do a search and the organization promising the payment doesn’t show up, it most likely doesn’t exist.
- Pay attention to the sender’s address: If it looks like gibberish or the domain belongs to a free webmail service, it is hardly likely to be from a government body.
- Pay attention to how the message is written and how the website looks. Civil servants usually do not send out messages full of typos and strings of exclamation points. Also be wary if the e-mail mentions long lines of applicants or tight deadlines.
- A demand to pay an up-front fee to get the process started (or for any other reason) is another sure sign of fraud. Bona fide government departments and banks do not require this. If there really is a commission to pay, a real organization will simply deduct it from the amount that you are due.
- Use a reliable security solution that can spot and block both malicious e-mails and phishing pages.
Source
