This post is reprinted from my own post in January 2023 on Kafan, I did not keep the original screenshots, so some of the screenshots were added to the Kafan watermark, herewith.
Elasticsearch B.V. is an Internet company registered in Mountain View, California, and their flagship product is ElasticSearch, an "open source software" with enterprise search as its main function. analysis and big data purposes.
In June 2019, they acquired another security startup, Endgame, for $234 million (they had attended AVC prior to the acquisition, and you can see the face of their product through AVC's Enterprise Annual Report at the time), officially entering the security industry, and in early 2021 they incorporated Endgame's product into their ElasticSearch framework, and launched ElasticAgent for rapid deployment, and then the name Endgame was as "End" as it gets.
Currently, there are basically only two options for security software "open source" solutions, one is ClamAV launched by Cisco, which only provides a pure command-line invocation of the engine, and the other is Elastic Defend, which provides a complete security solution (including NGAV and EDR).
One thing to note though, ClamAV is released using the GPLv2 open source agreement, so as an open source software it is used in various places without any objection. Elastic's product line, on the other hand, is released using the Elastic License 2 (which once also used the same SSPL protocol as MongoDB), and there is some disagreement as to whether this can be called an open source protocol.
The difference between Elastic License 2 and other mainstream open source protocols is that EL2 allows you to modify and redistribute its source code, both commercial and non-commercial, and does not require you to open source your modified code, but explicitly states that you cannot remove other copyright information such as Elastic's logo and cannot provide hosting services.
This can not provide hosting services, a simple understanding is that you can help other companies as MSP vendors to install and deploy Elastic software, but the other company must use ElasticSearch directly, not you directly provide a service for them to access and not at all to direct access the ElasticSearch product.
Many people in the industry believe that such an agreement does not count as "open source software" because it is "open source" but not "free".
Here I do not want to discuss too much about whether he is open source software, I care more about his current as a free security program is sufficient or not.
I've been following Elastic's development because their ElasticSearch and Kibana consoles are inherently well-suited for EDR use, something that no other security-focused company can offer. But unfortunately, as a commercial company and not an open source foundation, they are always looking for ways to make a profit rather than just doing "public good", so in 2022 they will start to include many new features in the paid version of the exclusive, no longer open source version = full version (previously there were also paid features like XPACK but there is no difference for security).
Currently, you need to purchase the Platinum version to use behavioral anti-ransom as well as memory threat detection (I'm not sure if the English version is called Platinum, the package name comes from their Simplified Chinese website).
I decided to use the paid version because I wanted to experience the full version and see how it works in my current environment.
Then I decided to use the paid version because it is difficult to purchase the paid version, and considering that my knowledge of ES is only that I can use it, and I am worried about the effect caused by the deployment error, I directly used the cloud pre-deployment EFK (Elastic+Fleet+Kibana, as a security use without Logstash) provided by AWS (Amazon Cloud) to conduct the evaluation.
The configuration used is as follows:
EC2.c6gd / 2 cores guaranteed, 8 cores burst (ARM) / 6GB RAM / 35GB SSD + 840GB cold storage
ElasticSearch Platinum Edition
In this configuration, the cost incurred without considering outgoing traffic is $33.408 / month, which I consider an acceptable level considering the current price of enterprise-class security software (as a comparison CrowdStrike full version is $200 / appliance / year). After all, it only charges according to the level of resources used, and as long as your configuration is high enough, you can theoretically deploy an unlimited number of endpoints.
First, go to the Elastic backend (or Kibana) and from the menu go to Integrations, then find Elastic Defend.
Click on the Add Elastic Defend button to add it to your Fleet.
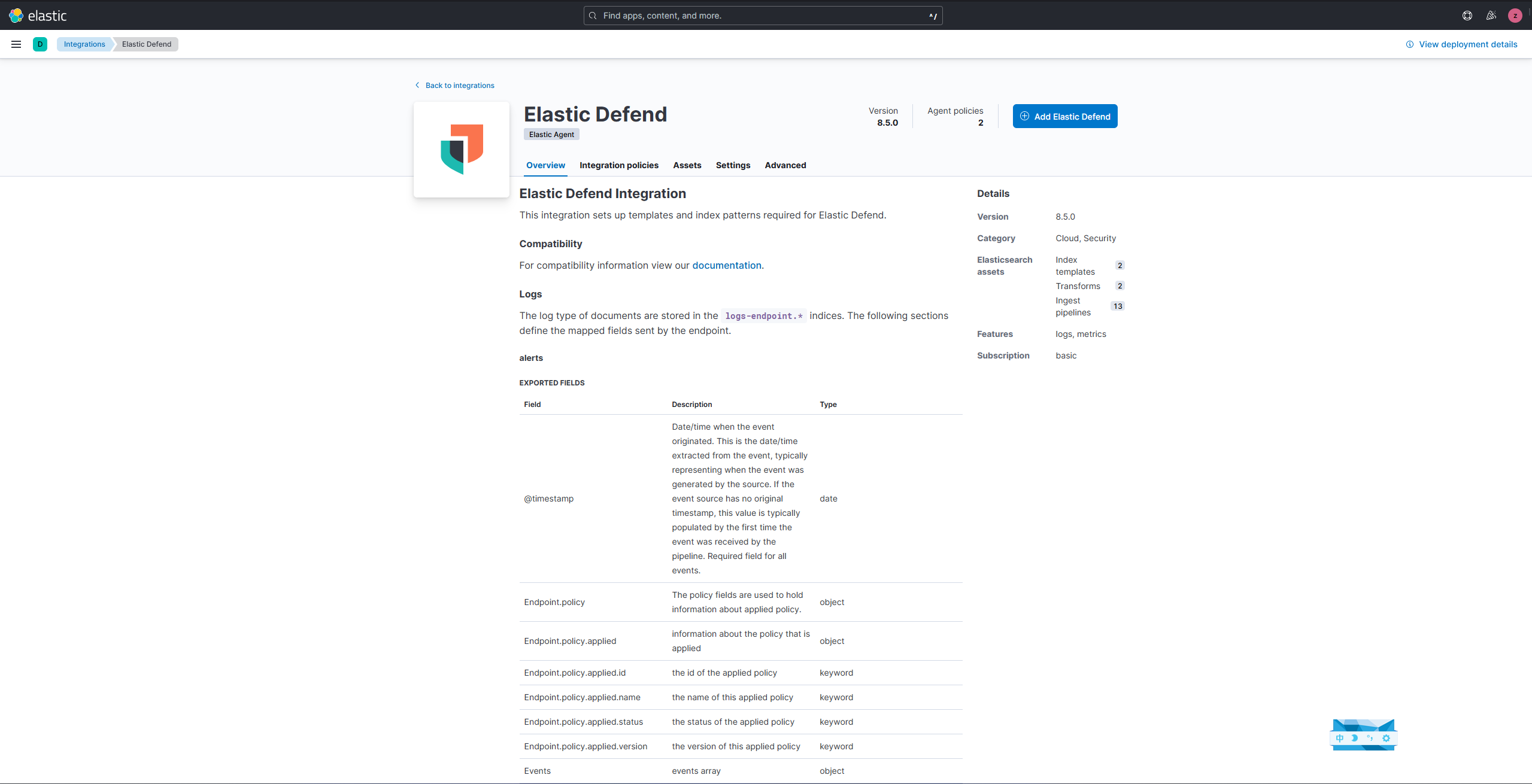
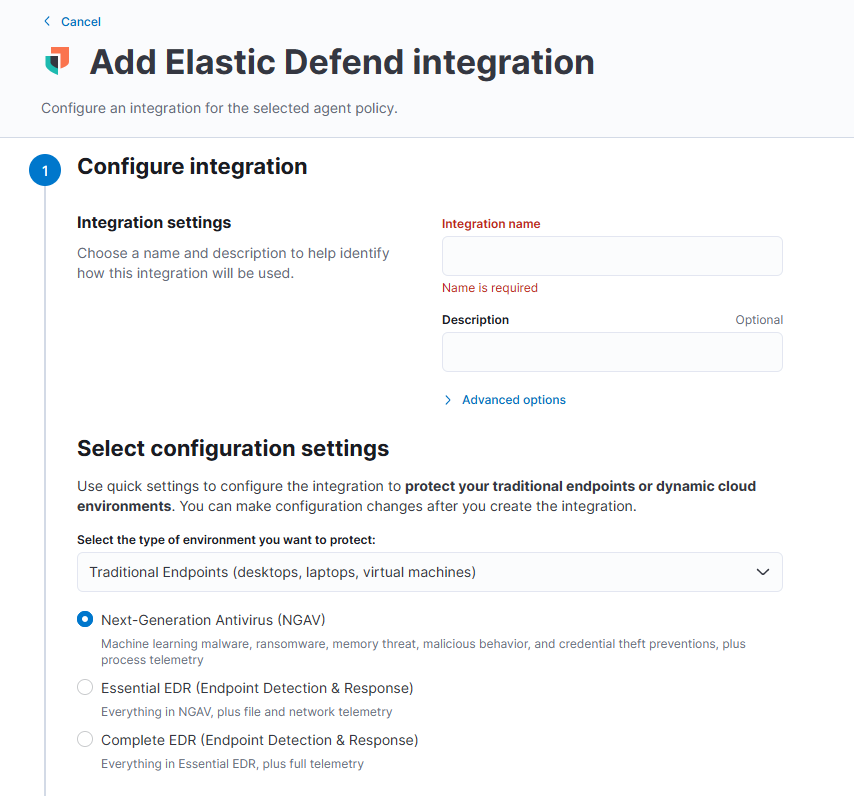
After adding it, besides giving it a name, you also need to choose which type of feature you need.
Here we take into account that the cloud server only has 35GB SSD, choose Essential EDR (Endpoint Detection & Response).
If you only need him as a basic antivirus, choose NGAV, which consumes negligible disk resources at this point.
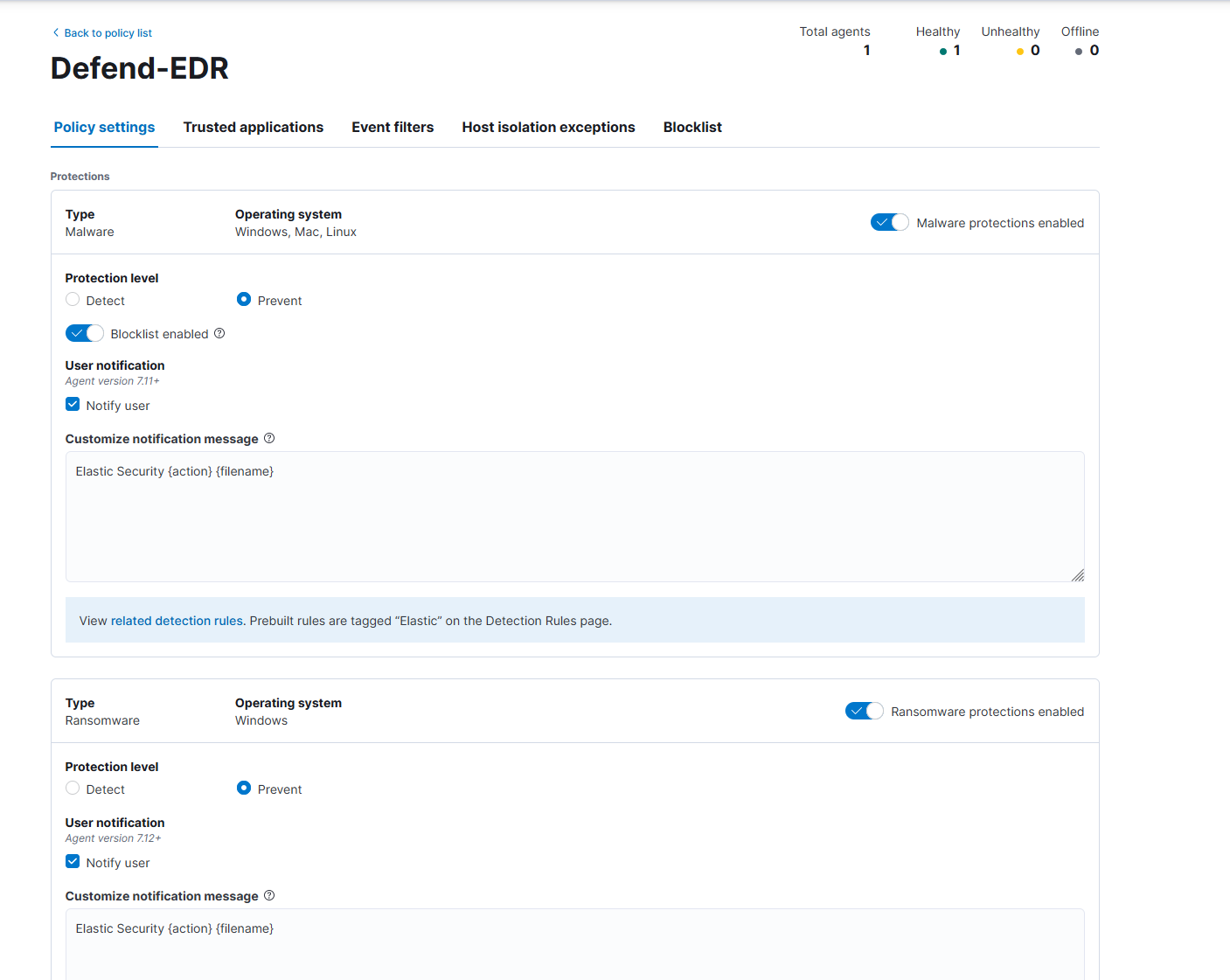
Once added, we can go back to Policy and see the Integrations (which I named Defend-EDR) we just added.
Here you can change some settings, such as anti-virus, anti-ransom, memory threat protection switch and trigger behavior.
If you set it to Detect, it will only detect and log but not intercept, if you set it to Prevent, it will automatically block the process when detected.
The Notify user at the bottom, if turned on, will display a message on the client to alert the user when triggered.
There is an important feature at the bottom, Elastic Defend will be registered as security software and Windows Defender will be turned off when it is turned on.
We turned it on during the review so that WD would not interfere with our later tests.
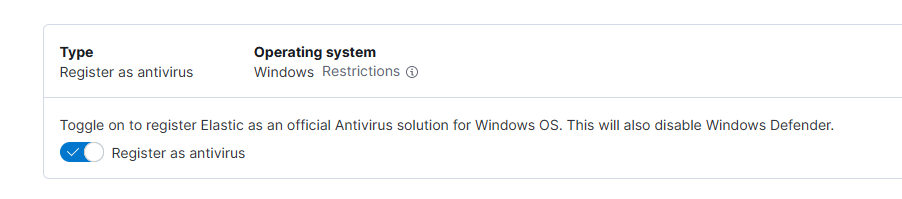
After completing all the settings, we are now ready to add the terminal.
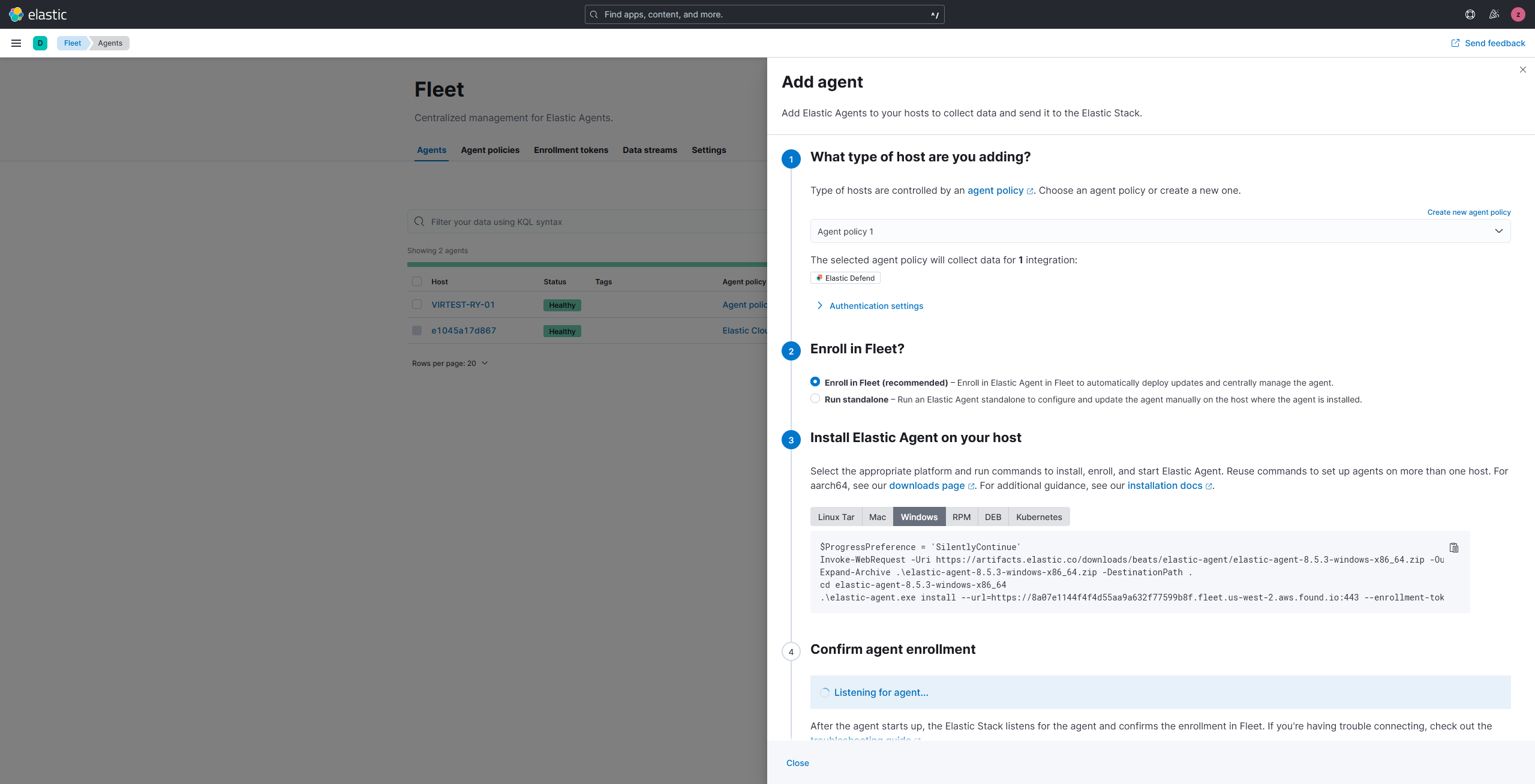
Download ElasticAgent from Elastic's website and transfer it to your device, then open Fleet and click Add Agent.
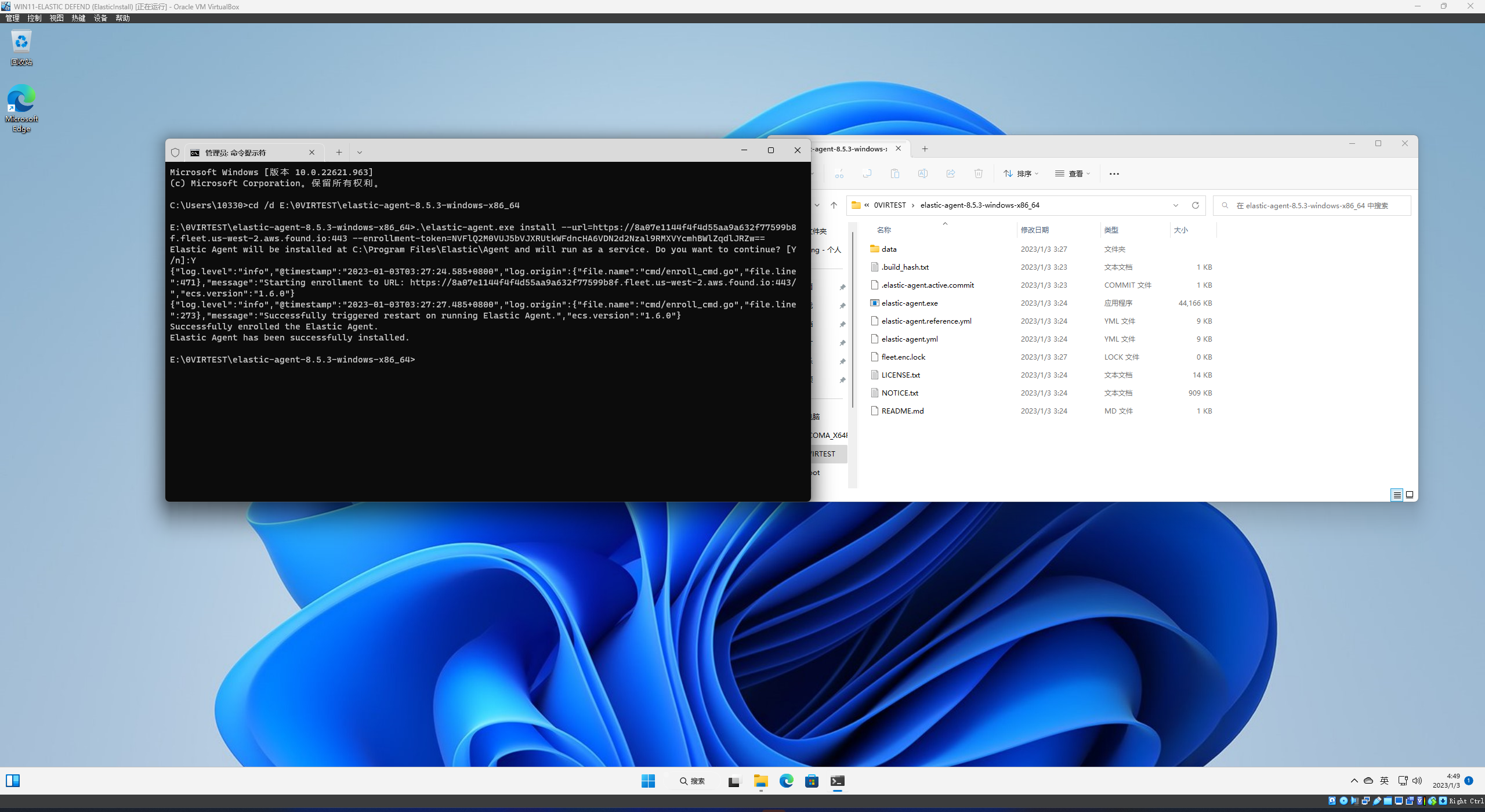
You can see that Elastic automatically generates the commands that you need to execute, just cd to the Agent directory and enter the corresponding commands.
Once executed, wait a few minutes for it to synchronize its rules, and you will see that Elastic has replaced Windows Defender in your security center.
Yes, just like Crowdstrike which @Shadowra tested before, it has no UI.
 At this point, the client deployment is complete. Although the setup is a bit tedious, it is the easiest for client deployment in the enterprise, and because it is command line execution, it is ideal for bulk deployment of a large number of devices.
At this point, the client deployment is complete. Although the setup is a bit tedious, it is the easiest for client deployment in the enterprise, and because it is command line execution, it is ideal for bulk deployment of a large number of devices.
For the first test we got a security lab to borrow a fake Telegram that hadn't been widely distributed yet.
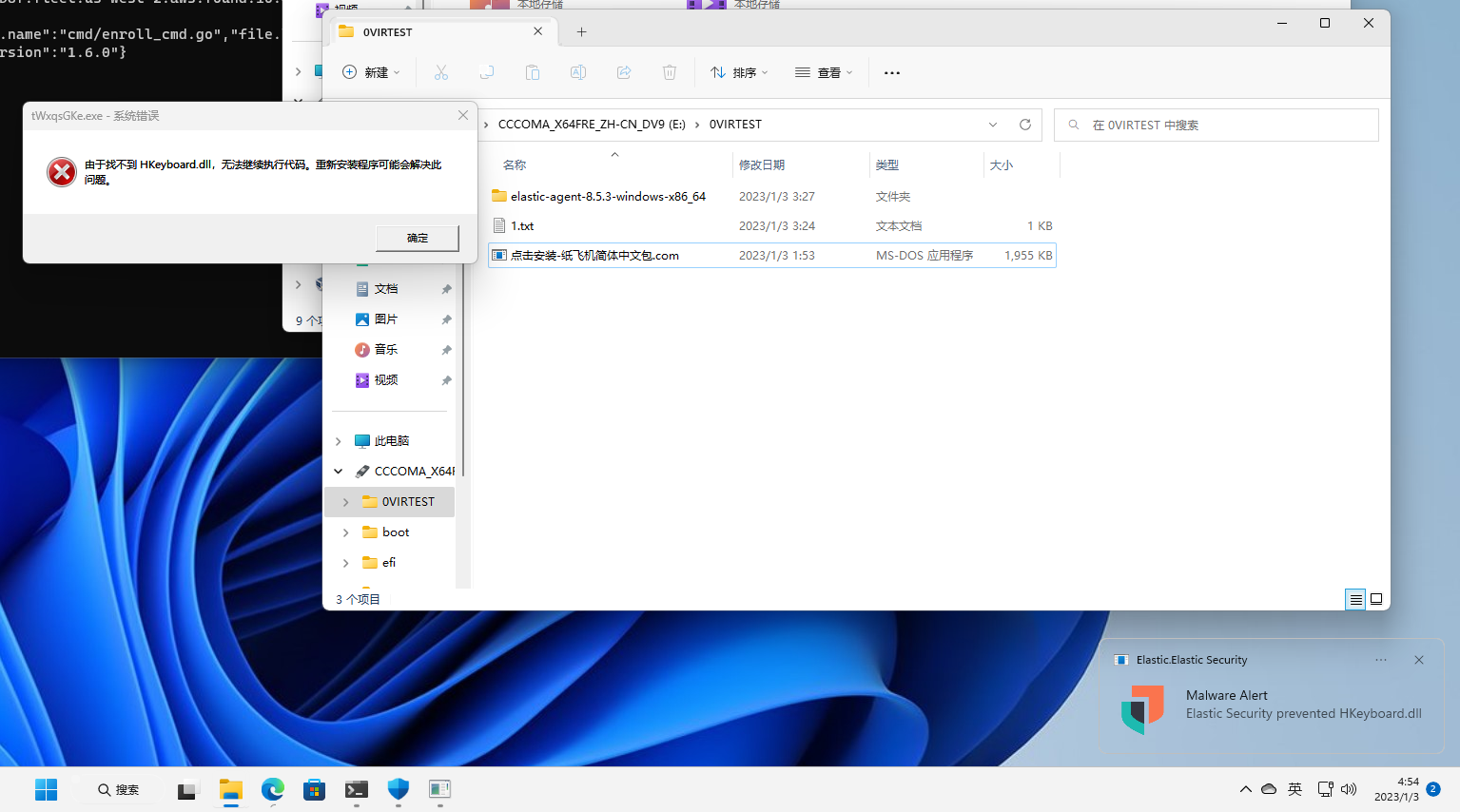
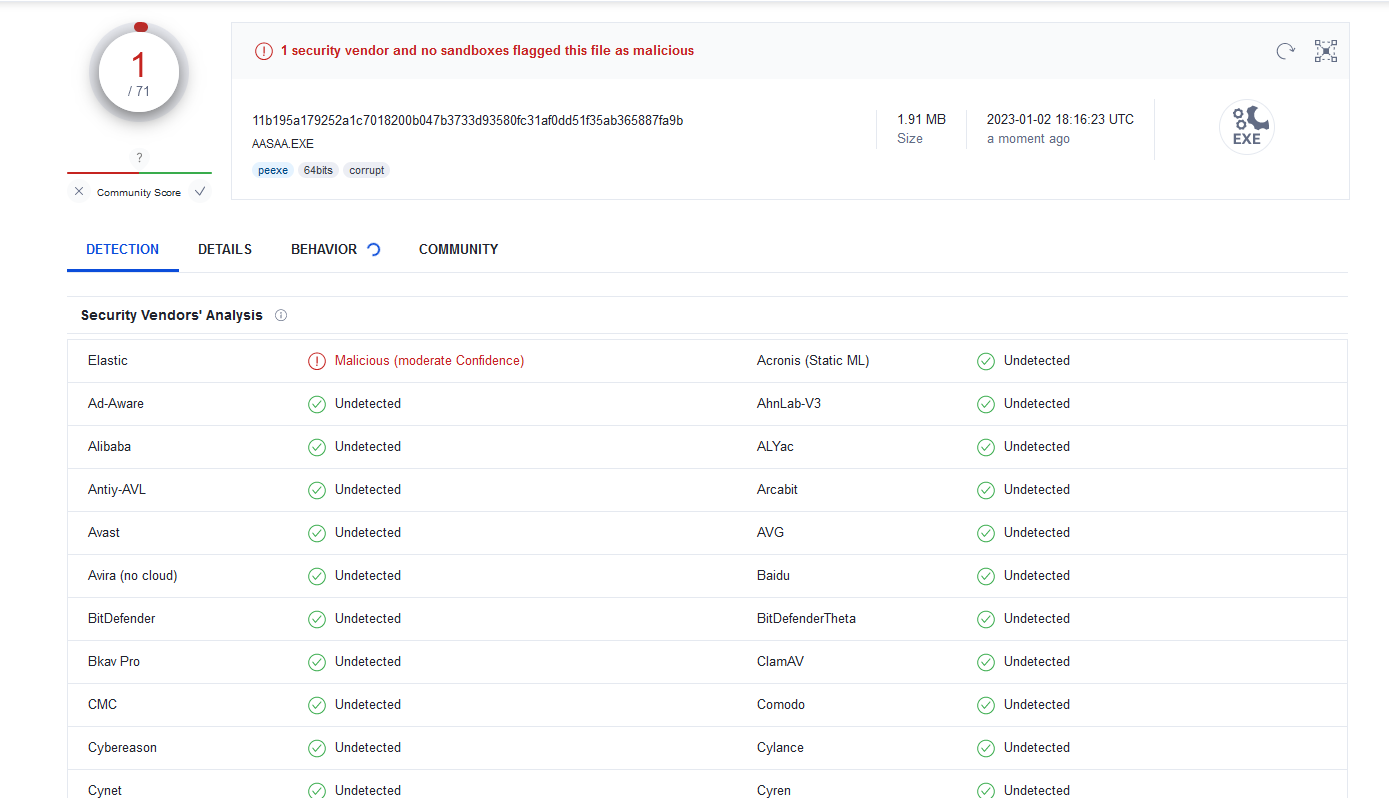
Elastic intercepted the dll released by the sample and then the sample exited with an error.
Also, Elastic is the only security software that detected this sample as of my testing on VT.
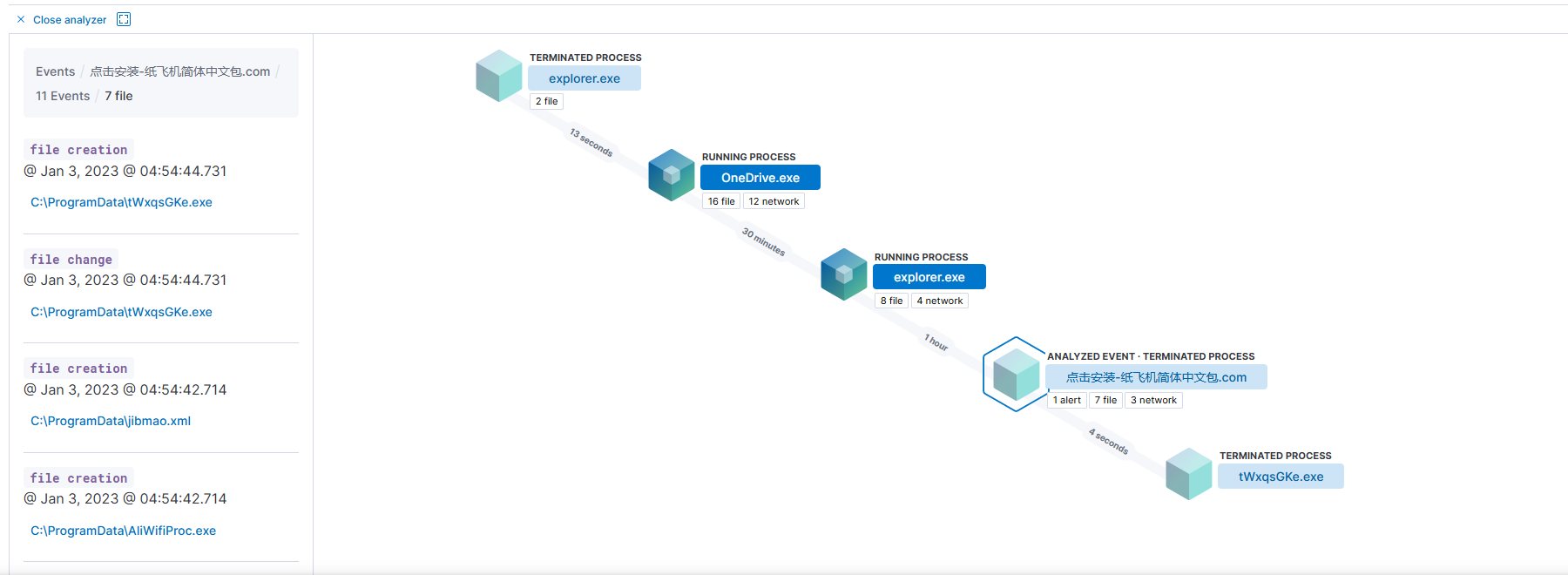
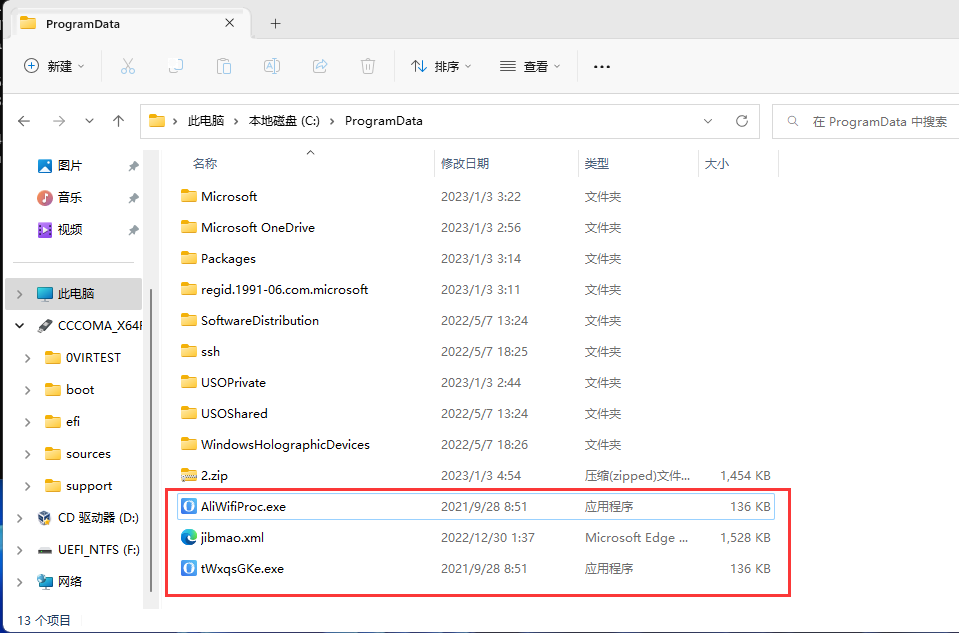
From the timeline we can see all the things the sample did, including the files released. Although Elastic only killed the derivative DLL to block the sample, it can still clean the rest of the derivatives through this timeline, which is an ability that many "specialized" security software does not have.
Following the timeline we easily found the rest of the derivatives and were able to clean them up along the way.
Then we tested samples from the
of AVG white exe + black dll remote control.
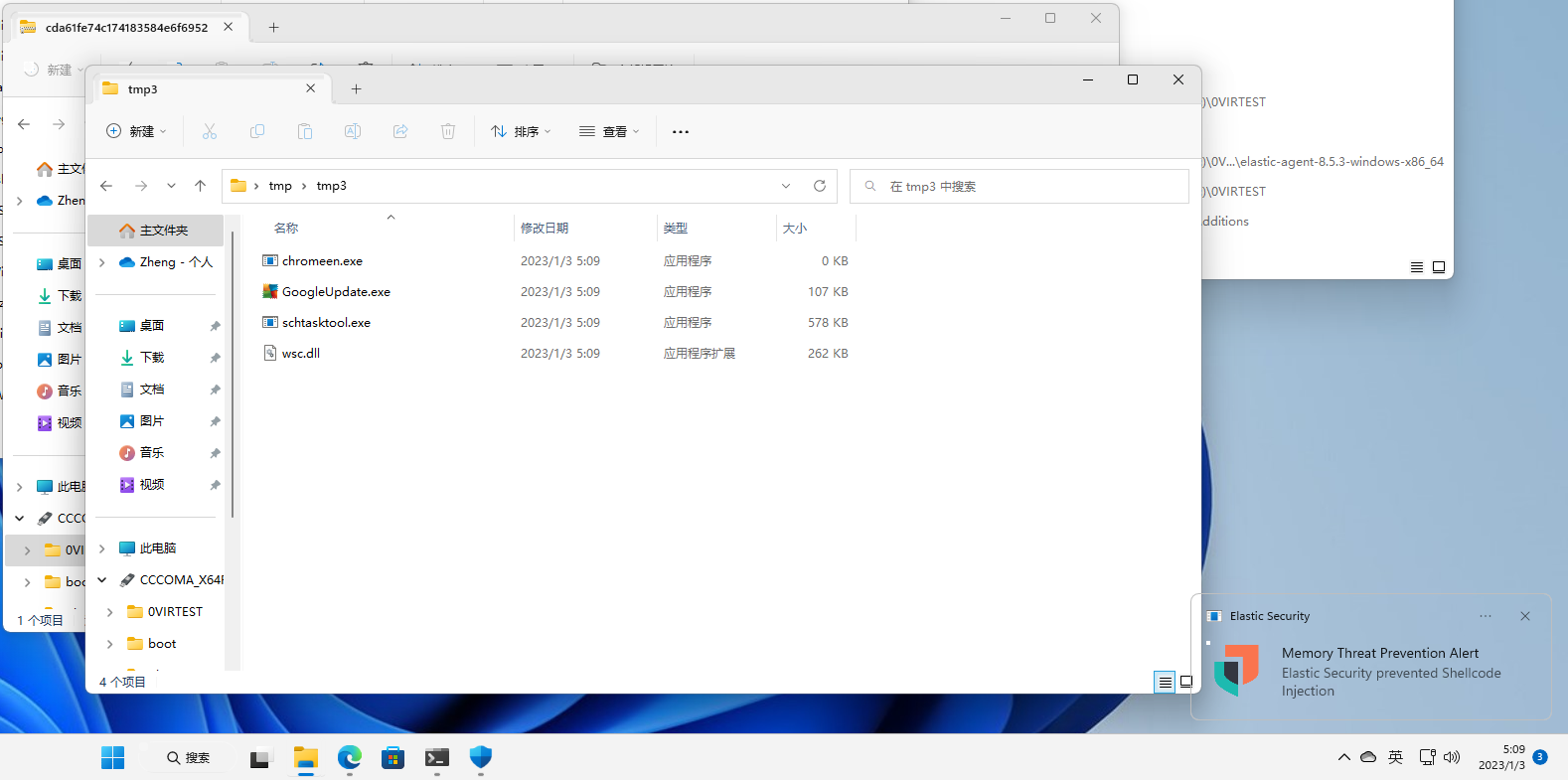
The sample successfully released an exe derivative of AVG, which was then detected by Memory Protection as a shellcode and intercepted when the black dll was loaded.
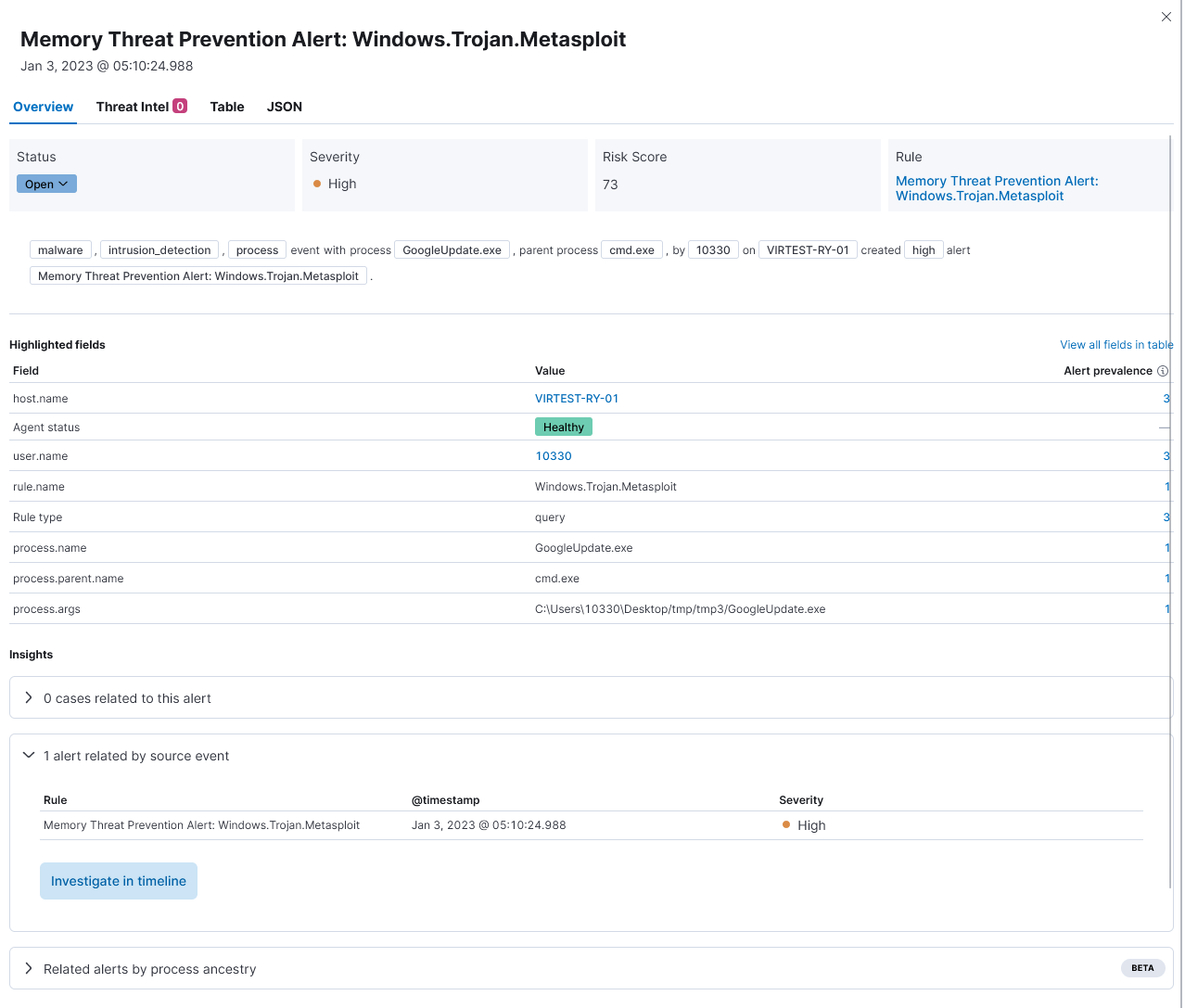 From the Elastic backend, we can see that although EDR detected the Shellcode injection, it was a little slow.
From the Elastic backend, we can see that although EDR detected the Shellcode injection, it was a little slow.
However, everything turned out to be fine, as the in-memory threat protection detected the Metasploit feature and closed the sample before it could.
Finally, let's summarize, Elastic Defend's strength is generally sufficient, as to whether this result is worth buying the Platinum Edition, it is a matter of opinion.
From the process of testing just now, this configuration of ES with a terminal to do EDR is seriously overkill, if there are a large number of devices then the cost performance will be significantly improved.
Of course, as NGAV when a supplemental protection + installed on the local machine free to use the open source version is also a good choice.
Elasticsearch B.V. is an Internet company registered in Mountain View, California, and their flagship product is ElasticSearch, an "open source software" with enterprise search as its main function. analysis and big data purposes.
In June 2019, they acquired another security startup, Endgame, for $234 million (they had attended AVC prior to the acquisition, and you can see the face of their product through AVC's Enterprise Annual Report at the time), officially entering the security industry, and in early 2021 they incorporated Endgame's product into their ElasticSearch framework, and launched ElasticAgent for rapid deployment, and then the name Endgame was as "End" as it gets.
Currently, there are basically only two options for security software "open source" solutions, one is ClamAV launched by Cisco, which only provides a pure command-line invocation of the engine, and the other is Elastic Defend, which provides a complete security solution (including NGAV and EDR).
One thing to note though, ClamAV is released using the GPLv2 open source agreement, so as an open source software it is used in various places without any objection. Elastic's product line, on the other hand, is released using the Elastic License 2 (which once also used the same SSPL protocol as MongoDB), and there is some disagreement as to whether this can be called an open source protocol.
The difference between Elastic License 2 and other mainstream open source protocols is that EL2 allows you to modify and redistribute its source code, both commercial and non-commercial, and does not require you to open source your modified code, but explicitly states that you cannot remove other copyright information such as Elastic's logo and cannot provide hosting services.
This can not provide hosting services, a simple understanding is that you can help other companies as MSP vendors to install and deploy Elastic software, but the other company must use ElasticSearch directly, not you directly provide a service for them to access and not at all to direct access the ElasticSearch product.
Many people in the industry believe that such an agreement does not count as "open source software" because it is "open source" but not "free".
Here I do not want to discuss too much about whether he is open source software, I care more about his current as a free security program is sufficient or not.
I've been following Elastic's development because their ElasticSearch and Kibana consoles are inherently well-suited for EDR use, something that no other security-focused company can offer. But unfortunately, as a commercial company and not an open source foundation, they are always looking for ways to make a profit rather than just doing "public good", so in 2022 they will start to include many new features in the paid version of the exclusive, no longer open source version = full version (previously there were also paid features like XPACK but there is no difference for security).
Currently, you need to purchase the Platinum version to use behavioral anti-ransom as well as memory threat detection (I'm not sure if the English version is called Platinum, the package name comes from their Simplified Chinese website).
I decided to use the paid version because I wanted to experience the full version and see how it works in my current environment.
Then I decided to use the paid version because it is difficult to purchase the paid version, and considering that my knowledge of ES is only that I can use it, and I am worried about the effect caused by the deployment error, I directly used the cloud pre-deployment EFK (Elastic+Fleet+Kibana, as a security use without Logstash) provided by AWS (Amazon Cloud) to conduct the evaluation.
The configuration used is as follows:
EC2.c6gd / 2 cores guaranteed, 8 cores burst (ARM) / 6GB RAM / 35GB SSD + 840GB cold storage
ElasticSearch Platinum Edition
In this configuration, the cost incurred without considering outgoing traffic is $33.408 / month, which I consider an acceptable level considering the current price of enterprise-class security software (as a comparison CrowdStrike full version is $200 / appliance / year). After all, it only charges according to the level of resources used, and as long as your configuration is high enough, you can theoretically deploy an unlimited number of endpoints.
First, go to the Elastic backend (or Kibana) and from the menu go to Integrations, then find Elastic Defend.
Click on the Add Elastic Defend button to add it to your Fleet.
After adding it, besides giving it a name, you also need to choose which type of feature you need.
Here we take into account that the cloud server only has 35GB SSD, choose Essential EDR (Endpoint Detection & Response).
If you only need him as a basic antivirus, choose NGAV, which consumes negligible disk resources at this point.
Once added, we can go back to Policy and see the Integrations (which I named Defend-EDR) we just added.
Here you can change some settings, such as anti-virus, anti-ransom, memory threat protection switch and trigger behavior.
If you set it to Detect, it will only detect and log but not intercept, if you set it to Prevent, it will automatically block the process when detected.
The Notify user at the bottom, if turned on, will display a message on the client to alert the user when triggered.
There is an important feature at the bottom, Elastic Defend will be registered as security software and Windows Defender will be turned off when it is turned on.
We turned it on during the review so that WD would not interfere with our later tests.
After completing all the settings, we are now ready to add the terminal.
Download ElasticAgent from Elastic's website and transfer it to your device, then open Fleet and click Add Agent.
You can see that Elastic automatically generates the commands that you need to execute, just cd to the Agent directory and enter the corresponding commands.
Once executed, wait a few minutes for it to synchronize its rules, and you will see that Elastic has replaced Windows Defender in your security center.
Yes, just like Crowdstrike which @Shadowra tested before, it has no UI.
For the first test we got a security lab to borrow a fake Telegram that hadn't been widely distributed yet.
Elastic intercepted the dll released by the sample and then the sample exited with an error.
Also, Elastic is the only security software that detected this sample as of my testing on VT.
From the timeline we can see all the things the sample did, including the files released. Although Elastic only killed the derivative DLL to block the sample, it can still clean the rest of the derivatives through this timeline, which is an ability that many "specialized" security software does not have.
Following the timeline we easily found the rest of the derivatives and were able to clean them up along the way.
Then we tested samples from the
of AVG white exe + black dll remote control.
The sample successfully released an exe derivative of AVG, which was then detected by Memory Protection as a shellcode and intercepted when the black dll was loaded.
However, everything turned out to be fine, as the in-memory threat protection detected the Metasploit feature and closed the sample before it could.
Finally, let's summarize, Elastic Defend's strength is generally sufficient, as to whether this result is worth buying the Platinum Edition, it is a matter of opinion.
From the process of testing just now, this configuration of ES with a terminal to do EDR is seriously overkill, if there are a large number of devices then the cost performance will be significantly improved.
Of course, as NGAV when a supplemental protection + installed on the local machine free to use the open source version is also a good choice.