i contacted emsi support and they removed the detection:Many AVs do not detect PUAs/PUPs because they are not malware. Although they may often seem harmless, they can cause a series of problems, such as changing your browser's home page, installing search bars from unknown sources, and even adding extensions to your browser without your "consent". That's right, even Comodo (CIS) detects PUPs as malware and moves them to quarantine. I mentioned this because I used CIS. The good news is that adware has fallen into disuse, and today PUPs are no longer a problem. Even if your AV does not detect them, they can be easily removed. However, I would prefer that all AVs detect and move these pests to quarantine as well, as is the case with EMSI and MWB products.
App Review Emsisoft Anti-Malware Home 2025
- Thread starter Shadowra
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
It is advised to take all reviews with a grain of salt. In extreme cases some reviews use dramatization for entertainment purposes.
- Content created by
- Shadowra
Hey all,
I'd like to point out a flaw in this test. It's a simple mistake, but it's one that was the turning point.
Shadowra claims that "The machine [...] is ultimately destroyed by GDI malware that modifies the MBR." This is not true.
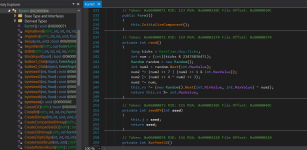
The SHA-256 hash of this file that Shadowra claimed to destroy the master boot record and make the computer unusable is daae8d64d00c481cf69922ce8770c5db6d74e273ae03573691602545280779d2, as seen at the timestamp in the video around 5:05. It's 230 KB and written in C# (.NET). The file isn't packed, and the code isn't obfuscated. The source code is fully readable.
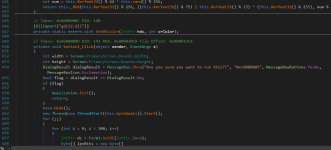
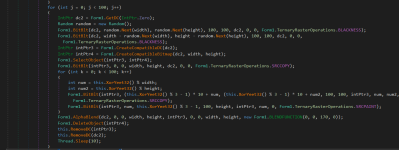
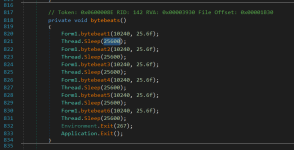
Upon reading the source code, you can see that the file actually does not touch the MBR. For 153600 milliseconds (around two and a half minutes), the code just displays colorful graphics on the screen and plays chiptune sounds. After that, the program closes itself. It doesn't touch the MBR or anything else. If you were to wait for it to close itself or reboot the computer after executing this, your PC would be fine and completely operational.
This is also evident from some of the already present signatures upon submitting the file to VirusTotal.
BitDefender Trojan.GenericKD.76984079
Emsisoft Trojan.GenericKD.76984079 (B)
ESET-NOD32 A Variant Of MSIL/BadJoke_AGen.BN
Ikarus Trojan.MSIL.BadJoke
Lionic Trojan.Win32.BadJoke.4!c
It's labeled as a "Bad Joke." Joke programs like this don't do any damage, and they either scare the person who runs them or do something interesting but harmless.
I felt this needed to be pointed out because the file here does not do anything malicious. Emsisoft's behaviour blocker had nothing to detect, and so it was right not to notice malicious behaviour. The test was finished too early. Emsisoft should be retested due to this.
I'd like to point out a flaw in this test. It's a simple mistake, but it's one that was the turning point.
Shadowra claims that "The machine [...] is ultimately destroyed by GDI malware that modifies the MBR." This is not true.
The SHA-256 hash of this file that Shadowra claimed to destroy the master boot record and make the computer unusable is daae8d64d00c481cf69922ce8770c5db6d74e273ae03573691602545280779d2, as seen at the timestamp in the video around 5:05. It's 230 KB and written in C# (.NET). The file isn't packed, and the code isn't obfuscated. The source code is fully readable.
Upon reading the source code, you can see that the file actually does not touch the MBR. For 153600 milliseconds (around two and a half minutes), the code just displays colorful graphics on the screen and plays chiptune sounds. After that, the program closes itself. It doesn't touch the MBR or anything else. If you were to wait for it to close itself or reboot the computer after executing this, your PC would be fine and completely operational.
This is also evident from some of the already present signatures upon submitting the file to VirusTotal.
BitDefender Trojan.GenericKD.76984079
Emsisoft Trojan.GenericKD.76984079 (B)
ESET-NOD32 A Variant Of MSIL/BadJoke_AGen.BN
Ikarus Trojan.MSIL.BadJoke
Lionic Trojan.Win32.BadJoke.4!c
It's labeled as a "Bad Joke." Joke programs like this don't do any damage, and they either scare the person who runs them or do something interesting but harmless.
I felt this needed to be pointed out because the file here does not do anything malicious. Emsisoft's behaviour blocker had nothing to detect, and so it was right not to notice malicious behaviour. The test was finished too early. Emsisoft should be retested due to this.
Attachments
hello Master, Could you run it , and make a video too here on this topic , about this bad joke showing us the bad and the joke behind it ^^ ?Hey all,
I'd like to point out a flaw in this test. It's a simple mistake, but it's one that was the turning point.
Shadowra claims that "The machine [...] is ultimately destroyed by GDI malware that modifies the MBR." This is not true.
The SHA-256 hash of this file that Shadowra claimed to destroy the master boot record and make the computer unusable is daae8d64d00c481cf69922ce8770c5db6d74e273ae03573691602545280779d2, as seen at the timestamp in the video around 5:05. It's 230 KB and written in C# (.NET). The file isn't packed, and the code isn't obfuscated. The source code is fully readable.
Upon reading the source code, you can see that the file actually does not touch the MBR. For 153600 milliseconds (around two and a half minutes), the code just displays colorful graphics on the screen and plays chiptune sounds. After that, the program closes itself. It doesn't touch the MBR or anything else. If you were to wait for it to close itself or reboot the computer after executing this, your PC would be fine and completely operational.
This is also evident from some of the already present signatures upon submitting the file to VirusTotal.
BitDefender Trojan.GenericKD.76984079
Emsisoft Trojan.GenericKD.76984079 (B)
ESET-NOD32 A Variant Of MSIL/BadJoke_AGen.BN
Ikarus Trojan.MSIL.BadJoke
Lionic Trojan.Win32.BadJoke.4!c
It's labeled as a "Bad Joke." Joke programs like this don't do any damage, and they either scare the person who runs them or do something interesting but harmless.
I felt this needed to be pointed out because the file here does not do anything malicious. Emsisoft's behaviour blocker had nothing to detect, and so it was right not to notice malicious behaviour. The test was finished too early. Emsisoft should be retested due to this.
PS : use a real pc (no VM) but not yours, for the joke ^^
Last edited:
99% of people would not have known it was a 'joke actually Emsisoft was founded because of a 'joke' program - I would not have been laughing at all.
'Emsisoft’s roots can be traced all the way to back to 1999 when our CEO Christian Mairoll kept receiving a nasty backdoor Trojan, “Back Orifice”, from so-called ‘friends’ via ICQ. As it forced the CD drive to repeatedly open and close, his curiosity sparked. How does this Trojan work? How do I get rid of it? It was then that the first line of Emsisoft Anti-Malware’s code was written.
About Emsisoft
'Emsisoft’s roots can be traced all the way to back to 1999 when our CEO Christian Mairoll kept receiving a nasty backdoor Trojan, “Back Orifice”, from so-called ‘friends’ via ICQ. As it forced the CD drive to repeatedly open and close, his curiosity sparked. How does this Trojan work? How do I get rid of it? It was then that the first line of Emsisoft Anti-Malware’s code was written.
About Emsisoft
Hello,hello Master, Could you run it , and make a video too here on this topic , about this bad joke showing us the bad and the joke behind it ^^ ?
PS : use a real pc (no VM) but not yours, for the joke ^^
You can find videos of people running the same file on YouTube, showcasing what it does.
Here's a video where someone runs the file:
As you can see, it displays colorful graphics on the screen and plays chiptune sounds. Then after 2 and a half minutes, it closes the program, and the computer is completely operational, including the desktop. The MBR was not touched, and if it was, the desktop would be broken.
Hello,99% of people would not have known it was a 'joke actually Emsisoft was founded because of a 'joke' program - I would not have been laughing at all.
'Emsisoft’s roots can be traced all the way to back to 1999 when our CEO Christian Mairoll kept receiving a nasty backdoor Trojan, “Back Orifice”, from so-called ‘friends’ via ICQ. As it forced the CD drive to repeatedly open and close, his curiosity sparked. How does this Trojan work? How do I get rid of it? It was then that the first line of Emsisoft Anti-Malware’s code was written.
About Emsisoft
Your quote refers to a backdoor that the CEO of Emsisoft found when he was young. The file that we're talking about isn't a backdoor. The two are not comparable. The file in no way connects to any malicious domains and no data or information is exfiltrated from the PC.
As for people not knowing that the file isn't a joke, the file shows a popup clearly stating what the program does and asks if the user wants to run it. It isn't meant to be spread to infect people. It's highly unlikely you would ever see it in the wild. In fact, it shouldn't have been uploaded to MalwareBazaar in the first place. Their rules state that all uploaded files must be malicious and not PUPs. The file is not malware, and it doesn't cause any damage.
If you look at who made the file, you'll notice that the creator of it likes to make these types of "GDI malware" aka programs that use the Windows Graphics Device Interface to flash effects on your screen and play sounds. They can be malicious and include payloads, but they don't have to be. In this case, it's more of an art project and a hobby to the creator. The point is to make unique and interesting-looking graphics and patterns on the screen combined with interesting sounds. There are communities of people who make these types of programs.
It may be a hobby to the idiot who makes these files. but would likely be very upsetting to the average PC user who does not have the info you have - As you say 'They can be malicious and include payloads, but they don't have to be. In this case, it's more of an art project and a hobby to the creator.
Who is to know if is or is not malicious? We are talking about the millions of users who know nothing about such things & could bring worry & concern to them & maybe expense thinking their system is infected, which would be a reasonable concern for many - People IMHO who produce such junk & distribute thinking its funny are morons of the highest order - I suspect you are one of the people who produce these things??
Final comment on the subject & Have a nice day
Who is to know if is or is not malicious? We are talking about the millions of users who know nothing about such things & could bring worry & concern to them & maybe expense thinking their system is infected, which would be a reasonable concern for many - People IMHO who produce such junk & distribute thinking its funny are morons of the highest order - I suspect you are one of the people who produce these things??
Final comment on the subject & Have a nice day
Last edited:
If this is really a joke app, how could behavioral analysis detect it? Some app launches full-screen video effects... What if it's a game? Such a behavioral analyzer would give too many false positives. I don't think it's a problem that Emsisoft didn't detect little-known joke software.
What I'm curious about is whether @Shadowra could share a sample and confirm that this is a joke app and the MBR wasn't destroyed?
What I'm curious about is whether @Shadowra could share a sample and confirm that this is a joke app and the MBR wasn't destroyed?
Most of fp detections I have encountered were by behavioral analysis.If this is really a joke app, how could behavioral analysis detect it
That's sad.
I was a multi year user of Online Armor and Mamutu way waaay back in the day when I used to squat at Wilder's; I loved mamutu and OA; then they got absorbed into Emisisoft solution and I found that solution to be extremely resource heavy. Thus, I abandoned their lic and only used their stand alone emergency scanner every few months or so.
I was a multi year user of Online Armor and Mamutu way waaay back in the day when I used to squat at Wilder's; I loved mamutu and OA; then they got absorbed into Emisisoft solution and I found that solution to be extremely resource heavy. Thus, I abandoned their lic and only used their stand alone emergency scanner every few months or so.
Yes, joke programmes with minimal behaviour are usually not the objective of behavioural blocking at all. They don’t provide any sequences or policy violations and on top of that, they’ve got almost no API calls.If this is really a joke app, how could behavioral analysis detect it? Some app launches full-screen video effects... What if it's a game? Such a behavioral analyzer would give too many false positives. I don't think it's a problem that Emsisoft didn't detect little-known joke software.
What I'm curious about is whether @Shadowra could share a sample and confirm that this is a joke app and the MBR wasn't destroyed?
Emsisoft outsources malware detection to Bitdefender. Bitdefender did not detect the joke program. But Emsisoft missed other malware too.
However, its behavioral protection needs a major overhaul: several malware programs, such as scripts and RATs, slipped through undetected.
If Emsisoft is set to its default configuration, then this can and will happen. However, the product provides robust protection if the behavior blocker is set to manual/alert. The problem with that is that it requires the user to know what an alert means, what it says, and what they should not and should do from there.However, its behavioral protection needs a major overhaul: several malware programs, such as scripts and RATs, slipped through undetected.
Worse still, a GDI malware program got through and destroyed the system.
Still pounding it out on the keyboard. Just not interfacing with the general public. Consumers on the Emsisoft forum used to give him high blood pressure.Where is Fabian? Gone like the wind.
Telenetwork model and low overhead. Keep the company small, hire remote workers from eastern Europe and other low-cost labor regions, and execute a niche product reasonably well.Not sure how they're gonna survive having less than 50 employees globally.
Without a full dissection and analysis of what occurred in the test, it is really a stretch to generalize or extrapolate all the way to the company level. Now if the behavior blocker or other capabilities are discovered to have serious inadequacies, then is it poor company performance, negligence, not yet tested and incorporated into the product, insufficient personnel, etc?
I'm confident that if the video got reported to Emsisoft then it would investigate and fix the problem(s) as required.
You may also like...
-
App Review Bitdefender Total Security 2026
- Started by Shadowra
- Replies: 60
-
App Review QuickHeal Total Security 2026
- Started by Shadowra
- Replies: 13
-
App Review Microsoft Defender Antivirus feat AI Defender
- Started by Shadowra
- Replies: 13
-
App Review DrWeb Security Space BETA
- Started by Shadowra
- Replies: 11
-
App Review ESET Internet Security v19
- Started by Shadowra
- Replies: 81