- Apr 1, 2017
- 1,824
- 8,263
- 2,768
Hello 
I was searching for a free and high-quality EDR tool.
Today I found it. its CWatch EDR by Comodo.
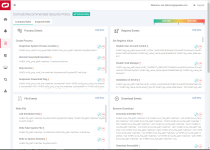
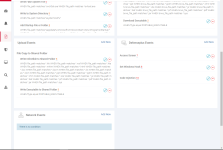
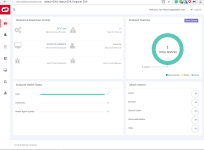
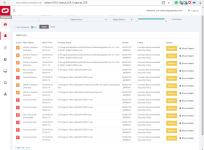
Its the only Comodo product that I'm in love with it:notworthy:! this application monitors your windows for suspicious activities and generates smart alerts to your dashboard! very cool application.i just uploaded the installer to vt and 3 Avs detected it as an unsafe(it was not in VT before).
VirusTotal
Idk how safe it is but very paranoid and cleverer tool.
You can add more parameters to monitor(i added Access Screen/ Set Windows Hook and Code Injection) !it works better than any HIPS/HIDS I really ♥ it.
I really ♥ it.
Its free : )
Give it a try.
Go here:
1-https://edr.cwatch.comodo.com/plans
2-choice the free plan.
3-Sign up
4- DW and install the tool.
5- You are protected
You can use it alongside with any Av! very light and effective tool.
I was searching for a free and high-quality EDR tool.
Today I found it. its CWatch EDR by Comodo.
Its the only Comodo product that I'm in love with it:notworthy:! this application monitors your windows for suspicious activities and generates smart alerts to your dashboard! very cool application.i just uploaded the installer to vt and 3 Avs detected it as an unsafe(it was not in VT before).
VirusTotal
Idk how safe it is but very paranoid and cleverer tool.
You can add more parameters to monitor(i added Access Screen/ Set Windows Hook and Code Injection) !it works better than any HIPS/HIDS
Its free : )
Give it a try.
Go here:
1-https://edr.cwatch.comodo.com/plans
2-choice the free plan.
3-Sign up
4- DW and install the tool.
5- You are protected
You can use it alongside with any Av! very light and effective tool.
Attachments
Last edited: