- Jan 24, 2011
- 9,379
An RSA researcher claims to have found an entirely new trojan during his trawls of the criminal underground.
RSA researcher Eli Marcus says the "Pandemiya" trojan comprises about 25,000 lines of fresh code. With most malware based on proven platforms, entirely new code is a rarity.
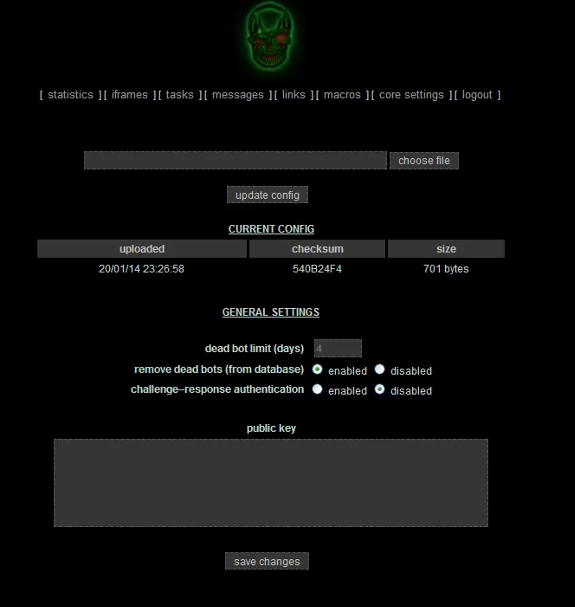
Pandemiya is nasty: it infects Windows PCs, steals data from forms, creates fake web pages and takes screen shots to send back to the botmasters who deploy it.
The software is modular and pervasive, and unique thanks to its ability to inject itself into all new processes via the Windows security registry function CreateProcess API.
It even has an upgrade path: Marcuswrites that a US$1,500 version offers basic functions but a US$2,000 cut allows .dll file plug-ins to enhance its functionality. A Facebook attack module is reportedly in the works.
"The advent of a freshly coded new trojan malware application is not too common in the underground," Marcus writes, adding that the modular approach means Pandemiya could become "more pervasive in the near future."
Pandemiya can also sign off botnet files, a trick Marcus said helped prevent hijacking and analysis by cops and security bods. Dynamic encrypted communications help it to dodge network analysers.
Read more: http://www.theregister.co.uk/2014/0..._built_malware_constantly_infects_everything/
RSA researcher Eli Marcus says the "Pandemiya" trojan comprises about 25,000 lines of fresh code. With most malware based on proven platforms, entirely new code is a rarity.
Pandemiya is nasty: it infects Windows PCs, steals data from forms, creates fake web pages and takes screen shots to send back to the botmasters who deploy it.
The software is modular and pervasive, and unique thanks to its ability to inject itself into all new processes via the Windows security registry function CreateProcess API.
It even has an upgrade path: Marcuswrites that a US$1,500 version offers basic functions but a US$2,000 cut allows .dll file plug-ins to enhance its functionality. A Facebook attack module is reportedly in the works.
"The advent of a freshly coded new trojan malware application is not too common in the underground," Marcus writes, adding that the modular approach means Pandemiya could become "more pervasive in the near future."

Pandemiya can also sign off botnet files, a trick Marcus said helped prevent hijacking and analysis by cops and security bods. Dynamic encrypted communications help it to dodge network analysers.
Read more: http://www.theregister.co.uk/2014/0..._built_malware_constantly_infects_everything/