- Nov 15, 2016
- 867
Ethiopia Deployed Israeli-Made Spyware Against Dissidents
New Report Raises Concern About Sale of Commercial Spyware to Governments
Ethiopian dissidents living overseas were infected with spyware made by an Israeli defense company, Canadian researchers allege. Their findings again raise questions about whether surveillance tools should be supplied to governments with shaky human rights records.
See Also: How to Scale Your Vendor Risk Management Program
Dissidents living in Australia, India, Japan, Norway, the United Kingdom, the United States and beyond received emails with links purported to be to videos or news content. But the links actually tried to deliver a spying program disguised as Adobe Systems software updates or PDF plugins, say the researchers at Citizen Lab, which is based at the Munk School of Global Affairs at the University of Toronto.
The targeted spying campaigns began in 2016, but so many operational security errors were made that Citizen Lab researchers were able to unravel them. And their findings have been seized on by privacy and human rights watchers.
"Ethiopia continues to be one of the sloppiest state actors in the nation-state spyware game and Israeli companies continue to be gleeful enablers," says Eva Galperin, director of cybersecurity for the Electronic Frontier Foundation, who was not involved in the research.
Ethiopia continues to be one of the sloppiest state actors in the nation-state spyware game and Israeli companies continue to be gleeful enablers.
— Eva (@evacide) December 6, 2017
Due Diligence?
Citizen Lab has conducted several investigations over the past few years into commercial spying tools from surveillance software vendors such as Hacking Team, NSO Group and Gamma Group.
The software used in the Ethiopian surveillance campaign, however, was built by Cyberbit, a subsidiary of large Israeli defense contractor Elbit Systems. The surveillance software is called PC 360, but was formerly known as PC Surveillance System. Once it infects a system it can harvest VOIP calls, files, emails and log keystrokes on a computer, among other invasive functions.
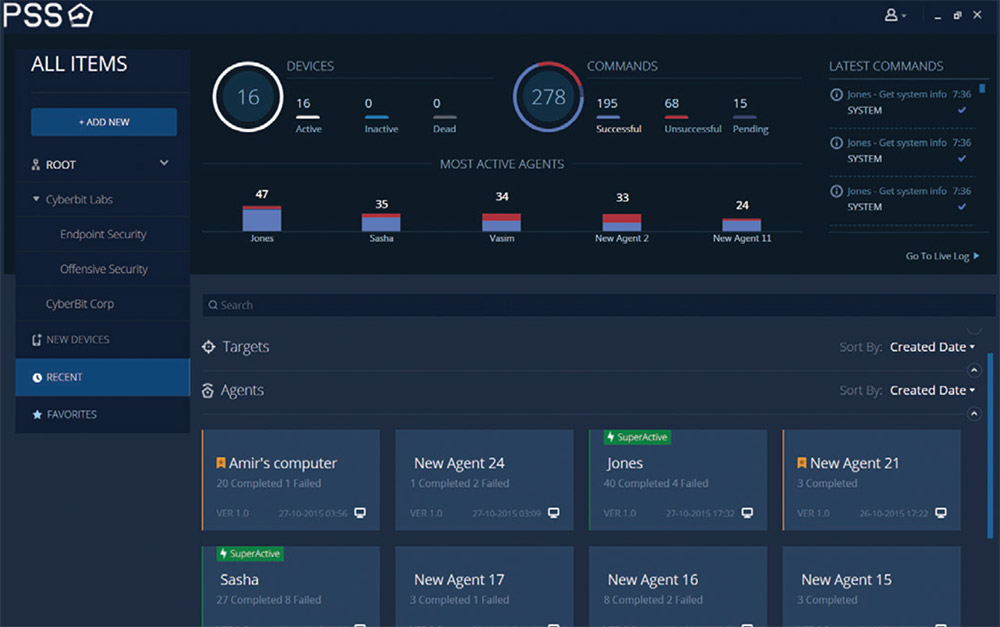
PSS software control panel, as displayed in Cyberbit's marketing materials.
Citizen Lab questioned whether Israeli authorities property scrutinized Cyberbit's supply of the tool to Ethiopia, given the country's history of using spyware against activists.
"The fact that a sale must have taken place in spite of this reality raises a number of concerns regarding Cyberbit's due diligence practices and any assessment of human rights impact undertaken during the export licensing process," the researchers write.
Cyberbit: We're Just A Vendor
Citizen Lab notified Cyberbit of its findings last month in a letter. In response, the company did not confirm that the Ethiopian government was a client and also attempted to distance itself from the findings. Cyberbit says that it "is a vendor and it does not operate any of its products."
Cyberbit's letter in response, published by Citizen Lab, continues: "The activity of such law enforcement and intelligence agencies is a matter of national security in any country and as a foreign vendor Cyberbit is not exposed to their operational activity."
Officials from Cyberbit and Elbit did not immediately respond to requests for comment from Information Security Media Group.
Ronald Deibert, director of Citizen Lab, writing in Wired, says that Israel does regulate the sale of commercial spyware but apparently not from a human rights perspective.
"Governments like Ethiopia no longer depend on their own in-country advanced computer science, engineering, and mathematical capacity in order to build a globe-spanning cyber espionage operation," Deibert writes. "They can simply buy it off the shelf from a company like Cyberbit."
Poor OpSec
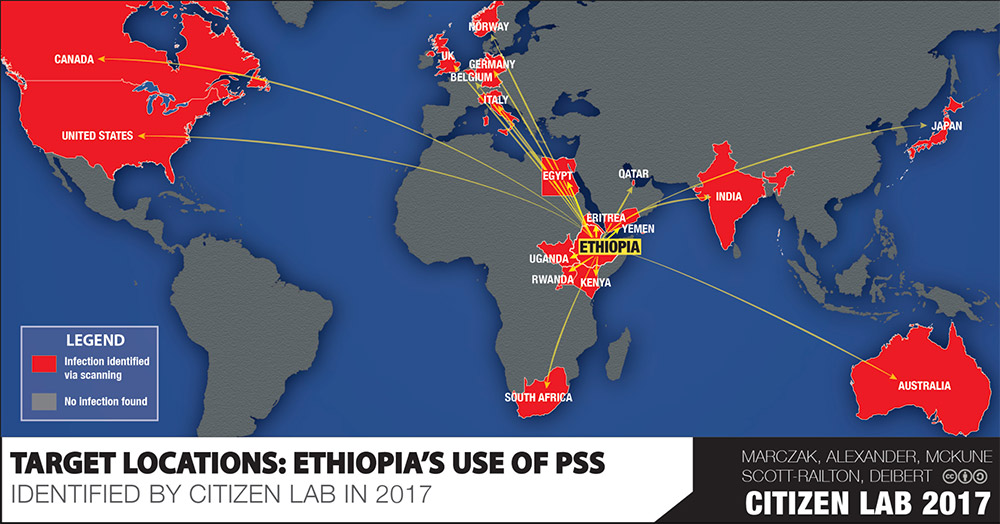
Source: Citizen Lab
Poor operational security practices on the part of Ethiopia helped Citizen Lab's investigation, researchers say. They found public log files for command-and-control servers that showed activity both by the controller of the spyware and victims. They monitored the log files for more than a year, which provided strong circumstantial evidence of activity linked to Cyberbit's infrastructure.
Through those logs, the researchers identified other victims that helped build a fuller picture of how attacks were executed. Unlike other commercial spying suites, the attacks using PSS relied entirely on socially engineering victims by trying to trick them into clicking on links and installing bogus software updates.
Some attacks relied on spoofed domains that appeared at first glance to be associated with legitimate websites as well as Adobe Systems. One target, researchers say, was Jawar Mohammed, the executive director of U.S.-based Oromia Media Network, which covers Ethiopian issues. He received an email with a link to getadobeplayer[.]com, which offered a supposed Flash update. Unbeknownst to victims, however, this update was bundled with spyware.
Adobe Fights 'Miscreants'
Citizen Lab wrote to Adobe on Dec. 1, alerting the company that its trademark was being abused as part of targeted spyware attacks. In response, Adobe thanked Citizen Lab, saying in part that "only through such partnerships can we hope to fight these miscreants."
Adobe adds: "We have taken steps to swiftly address this issue, including but not limited to contacting Cyberbit and other relevant service providers and filing the appropriate dispute regarding the registration and use of domain name at issue."
New Report Raises Concern About Sale of Commercial Spyware to Governments
Ethiopian dissidents living overseas were infected with spyware made by an Israeli defense company, Canadian researchers allege. Their findings again raise questions about whether surveillance tools should be supplied to governments with shaky human rights records.
See Also: How to Scale Your Vendor Risk Management Program
Dissidents living in Australia, India, Japan, Norway, the United Kingdom, the United States and beyond received emails with links purported to be to videos or news content. But the links actually tried to deliver a spying program disguised as Adobe Systems software updates or PDF plugins, say the researchers at Citizen Lab, which is based at the Munk School of Global Affairs at the University of Toronto.
The targeted spying campaigns began in 2016, but so many operational security errors were made that Citizen Lab researchers were able to unravel them. And their findings have been seized on by privacy and human rights watchers.
"Ethiopia continues to be one of the sloppiest state actors in the nation-state spyware game and Israeli companies continue to be gleeful enablers," says Eva Galperin, director of cybersecurity for the Electronic Frontier Foundation, who was not involved in the research.
Ethiopia continues to be one of the sloppiest state actors in the nation-state spyware game and Israeli companies continue to be gleeful enablers.
— Eva (@evacide) December 6, 2017
Due Diligence?
Citizen Lab has conducted several investigations over the past few years into commercial spying tools from surveillance software vendors such as Hacking Team, NSO Group and Gamma Group.
The software used in the Ethiopian surveillance campaign, however, was built by Cyberbit, a subsidiary of large Israeli defense contractor Elbit Systems. The surveillance software is called PC 360, but was formerly known as PC Surveillance System. Once it infects a system it can harvest VOIP calls, files, emails and log keystrokes on a computer, among other invasive functions.

PSS software control panel, as displayed in Cyberbit's marketing materials.
Citizen Lab questioned whether Israeli authorities property scrutinized Cyberbit's supply of the tool to Ethiopia, given the country's history of using spyware against activists.
"The fact that a sale must have taken place in spite of this reality raises a number of concerns regarding Cyberbit's due diligence practices and any assessment of human rights impact undertaken during the export licensing process," the researchers write.
Cyberbit: We're Just A Vendor
Citizen Lab notified Cyberbit of its findings last month in a letter. In response, the company did not confirm that the Ethiopian government was a client and also attempted to distance itself from the findings. Cyberbit says that it "is a vendor and it does not operate any of its products."
Cyberbit's letter in response, published by Citizen Lab, continues: "The activity of such law enforcement and intelligence agencies is a matter of national security in any country and as a foreign vendor Cyberbit is not exposed to their operational activity."
Officials from Cyberbit and Elbit did not immediately respond to requests for comment from Information Security Media Group.
Ronald Deibert, director of Citizen Lab, writing in Wired, says that Israel does regulate the sale of commercial spyware but apparently not from a human rights perspective.
"Governments like Ethiopia no longer depend on their own in-country advanced computer science, engineering, and mathematical capacity in order to build a globe-spanning cyber espionage operation," Deibert writes. "They can simply buy it off the shelf from a company like Cyberbit."
Poor OpSec

Source: Citizen Lab
Poor operational security practices on the part of Ethiopia helped Citizen Lab's investigation, researchers say. They found public log files for command-and-control servers that showed activity both by the controller of the spyware and victims. They monitored the log files for more than a year, which provided strong circumstantial evidence of activity linked to Cyberbit's infrastructure.
Through those logs, the researchers identified other victims that helped build a fuller picture of how attacks were executed. Unlike other commercial spying suites, the attacks using PSS relied entirely on socially engineering victims by trying to trick them into clicking on links and installing bogus software updates.
Some attacks relied on spoofed domains that appeared at first glance to be associated with legitimate websites as well as Adobe Systems. One target, researchers say, was Jawar Mohammed, the executive director of U.S.-based Oromia Media Network, which covers Ethiopian issues. He received an email with a link to getadobeplayer[.]com, which offered a supposed Flash update. Unbeknownst to victims, however, this update was bundled with spyware.
Adobe Fights 'Miscreants'
Citizen Lab wrote to Adobe on Dec. 1, alerting the company that its trademark was being abused as part of targeted spyware attacks. In response, Adobe thanked Citizen Lab, saying in part that "only through such partnerships can we hope to fight these miscreants."
Adobe adds: "We have taken steps to swiftly address this issue, including but not limited to contacting Cyberbit and other relevant service providers and filing the appropriate dispute regarding the registration and use of domain name at issue."