A "Teamviewer" with only 200 KB size that has also been uploaded as "Prison.Architect.The.Sunset.Update.Incl.A...exe" is clearly not legit.
I found an area that is XOR encoded with 0x1D, you can literally see the XOR key in the hex editor
After decoding it looks like this
The decoded portion contains a JS script, some additional strings and ZIP archive. The archive seems to be a Chrome extension with the ID jdejdmchbgaciegdmifmnkopbdbfhcfb
Strings related to Chrome extension installation.
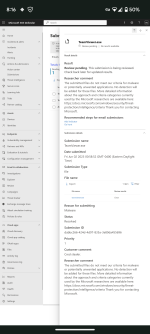
The manifest of the Chrome extension just names itself "Apps" and shows the author's email address as sg(dot)guru1030(at)gmail(dot)com:
That extension hijacks search results, redirects them to searchesmia(dot)com (the following image shows content.js):
In sum it is clearly malware (not PUP, because there is not a shred of something useful).
So far it is also not really dangerous, more annoying. There might be more going on, e.g., the ShellExecuteW could be a point for more examination, but this is already enough to declare it malware.
If Microsoft declared this as clean, they did an obvious mistake.