- Sep 17, 2013
- 1,492
After installing/uninstalling few applications some entries gets left in startup that are not valid. These autorun entries causes delayed bootup or other error messages during bootup.
There is no automatic cleaning tool. You need to do it manually. For that you need Comodo Cleaning Essentials.
Comodo Cleaning Essentials (CCE) is a set of computer security tools designed to help users identify and remove malware and unsafe processes from infected computers.
Major features include:
CCE is a lightweight, portable application which requires no installation and can be run directly from removable media such as a USB key, CD or DVD. Home users can quickly and easily run scans and operate the software with the minimum of fuss. More experienced users will enjoy the high levels of visibility and control over system processes and the ability to configure customized scans from the granular options menu.
DOWNLOAD LINK
COMODO CLEANING ESSENTIALS 8 ( 64 Bit )
COMODO CLEANING ESSENTIALS 8 ( 32 Bit )
Read about categories
Everything – Displays all the autorun items in the main display pane.
Logon – Displays only the autorun items identified from standard autostart locations such as the Startup folder for all users, the Registry Run keys, and standard application launch locations.
Explorer – Displays only the Explorer shell extensions from various installed applications, browser helper objects (BHO), explorer toolbars, active setup executions and shell execute hooks.
Internet Explorer – Displays only the BHOs, Internet Explorer toolbars and extensions.
Scheduled Tasks – Displays the modules loaded by tasks and applications scheduled from Windows Task Scheduler.
Services – Displays the modules loaded as Windows Services.
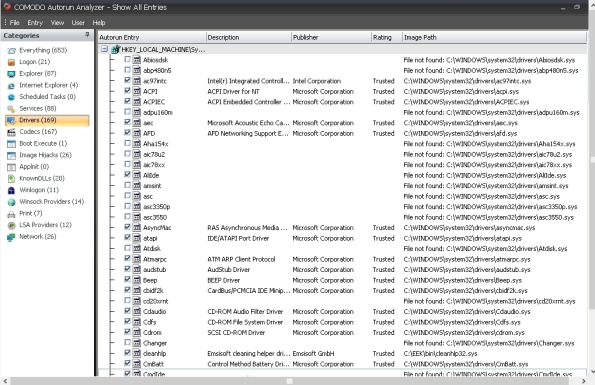
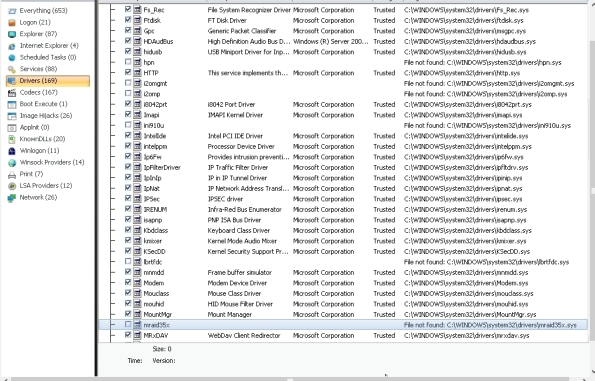
Drivers – Displays only the kernel-mode drivers that are in currently enabled on the system.
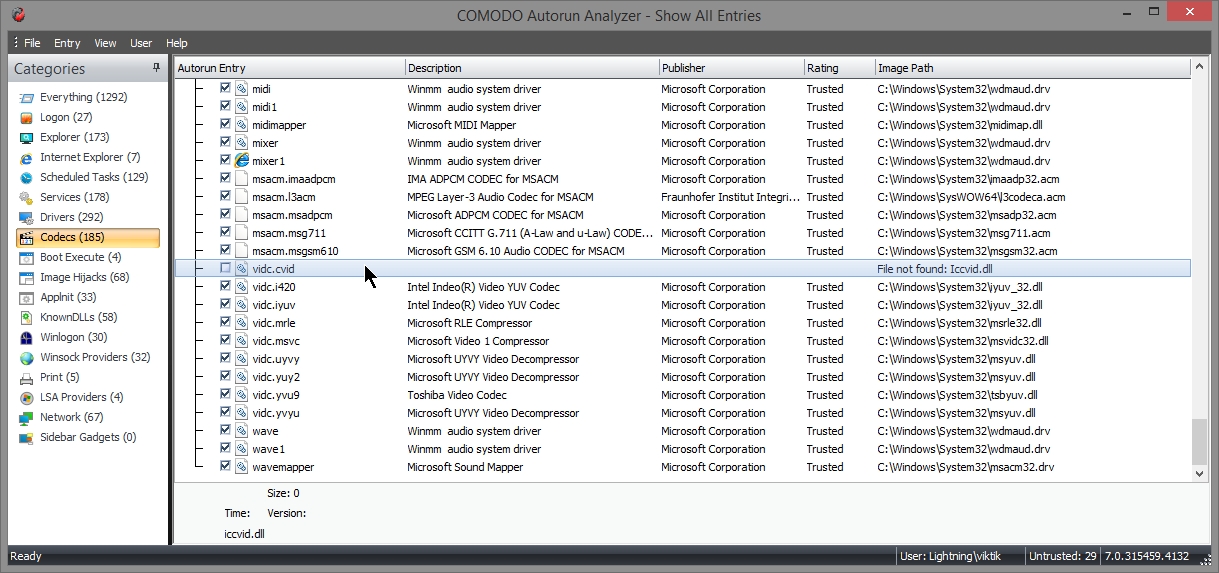
Codecs – Displays the autorun items loaded by various coders-decoders used for handling media files like audio and video files.
Boot Execute – Displays the autorun items loaded by applications, services and commands executed during the time period between the system boot-up and the user log-on.
Image Hijacks – Displays the modules loaded by image file execution options of various applications installed in your system. Most of the malware modify the image file execution options of a legitimate application and make themselves to run when the real application is started. Autorun Analyzer enables you to identify such illegitimate autorun items loaded by malware that affect the image file execution options of legitimate applications and to disable / remove them.
AppInit – Displays the application initialization Dynamic Link Library (DLL) modules loaded as autorun items.
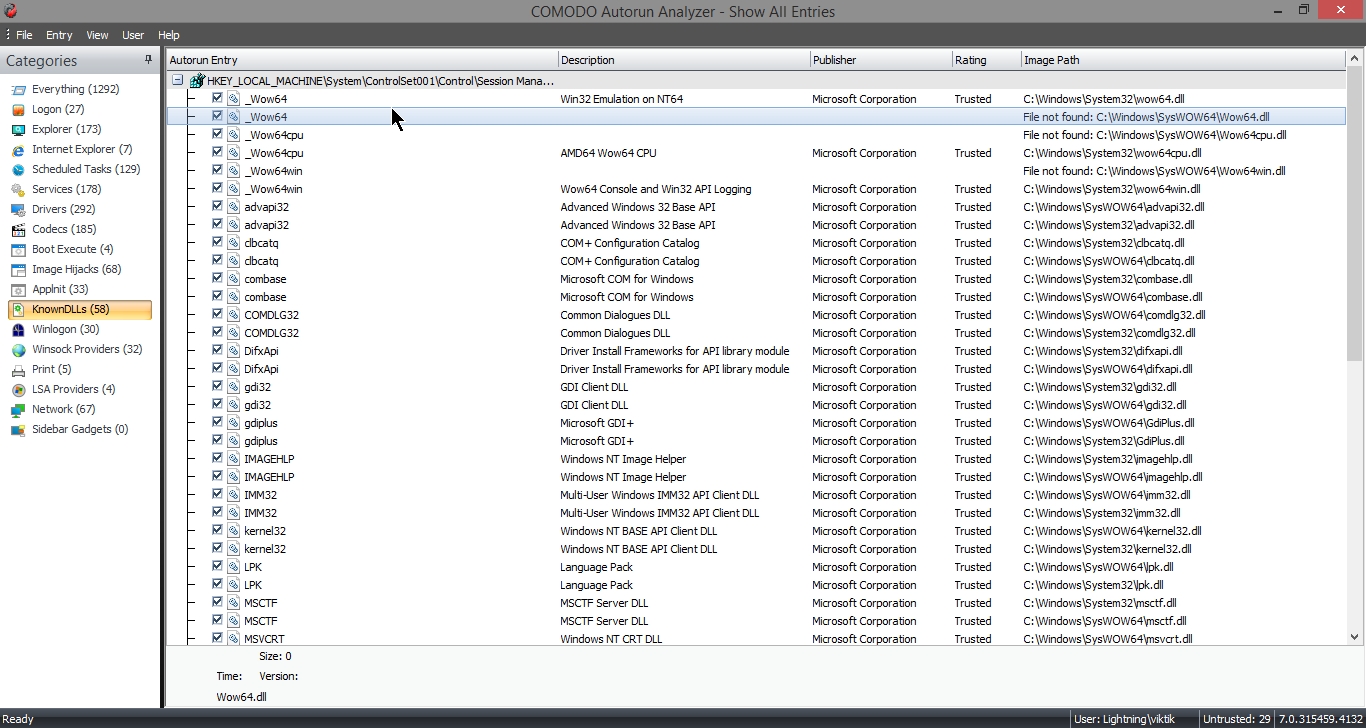
KnownDLLS – Displays the DLL modules loaded by Windows for the start-up applications that reference those DLLs.
Winlogon – Displays the DLL modules registered for Winlogon notification of logon events.
Winsock Providers – Displays the DLL modules registered for Winsock protocols, including Winsock service providers.
An anti-malware software do not scan Winsock Service Providers as it is treated as a safe zone. Taking advantage of this, some malware enter into your system as a Winsock Service Provider. But Autorun Analyzer can identify the DLL modules loaded by Winsock Service Providers and notify you if they are untrusted. It also enables you to remove those untrusted modules from your system.
Print – Displays the DLLs load into the print spoolers configured as services to start with Windows. Some malware find their entry through Print spooling service to start themselves automatically during system start-up.
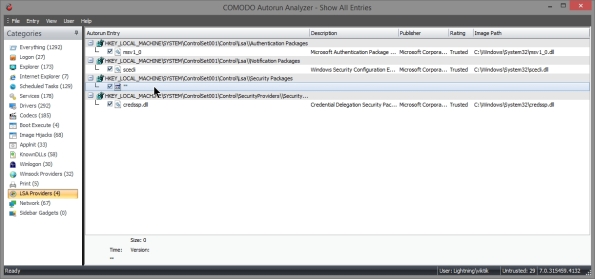
LSA Providers – Displays the DLL modules registered by Local Security Authority (LSA) authentication, notification and security packages.
Network – Displays the DLL modules loaded by network connection services.
Its better that you do this in categories
If you are not able to delete some entries, just leave it.
Try to not delete entries by Publisher "Microsoft Corporation".
DELETE ALL UNNECESSARY ENTRIES
Start Autorun Analyzer
Reboot when done
There is no automatic cleaning tool. You need to do it manually. For that you need Comodo Cleaning Essentials.
Comodo Cleaning Essentials (CCE) is a set of computer security tools designed to help users identify and remove malware and unsafe processes from infected computers.
Major features include:
- KillSwitch – an advanced system monitoring tool that allows users to identify, monitor and stop any unsafe processes that are running on their system.
- Malware scanner – Fully customizable scanner capable of unearthing and removing viruses, rootkits, hidden files and malicious registry keys hidden deep in your system.
Autorun Analyzer – An advanced utility to view and handle services and programs that were loaded when your system booted-up.
CCE is a lightweight, portable application which requires no installation and can be run directly from removable media such as a USB key, CD or DVD. Home users can quickly and easily run scans and operate the software with the minimum of fuss. More experienced users will enjoy the high levels of visibility and control over system processes and the ability to configure customized scans from the granular options menu.
DOWNLOAD LINK
COMODO CLEANING ESSENTIALS 8 ( 64 Bit )
- Comodo Cleaning Essentials 8 ( CCE 8 ) x64.zip
- Comodo Cleaning Essentials 8 ( CCE 8 ) x64.zip
- https://mega.nz/#!stEGmDRD!9s-1ZMI4K2foNudzBBybr2SnQEz0y1OrE756M8tdT_c
COMODO CLEANING ESSENTIALS 8 ( 32 Bit )
- Comodo Cleaning Essentials 8 ( CCE 8 ) x86.zip
- Comodo Cleaning Essentials 8 ( CCE 8 ) x86.zip
- https://mega.nz/#!Zs91CQbK!_Z4i_QBqyaBj-he96KeaTkp9yf4-cpApcChU0vXchqI
Read about categories
Everything – Displays all the autorun items in the main display pane.
Logon – Displays only the autorun items identified from standard autostart locations such as the Startup folder for all users, the Registry Run keys, and standard application launch locations.
Explorer – Displays only the Explorer shell extensions from various installed applications, browser helper objects (BHO), explorer toolbars, active setup executions and shell execute hooks.
Internet Explorer – Displays only the BHOs, Internet Explorer toolbars and extensions.
Scheduled Tasks – Displays the modules loaded by tasks and applications scheduled from Windows Task Scheduler.
Services – Displays the modules loaded as Windows Services.
Drivers – Displays only the kernel-mode drivers that are in currently enabled on the system.
Codecs – Displays the autorun items loaded by various coders-decoders used for handling media files like audio and video files.
Boot Execute – Displays the autorun items loaded by applications, services and commands executed during the time period between the system boot-up and the user log-on.
Image Hijacks – Displays the modules loaded by image file execution options of various applications installed in your system. Most of the malware modify the image file execution options of a legitimate application and make themselves to run when the real application is started. Autorun Analyzer enables you to identify such illegitimate autorun items loaded by malware that affect the image file execution options of legitimate applications and to disable / remove them.
AppInit – Displays the application initialization Dynamic Link Library (DLL) modules loaded as autorun items.
KnownDLLS – Displays the DLL modules loaded by Windows for the start-up applications that reference those DLLs.
Winlogon – Displays the DLL modules registered for Winlogon notification of logon events.
Winsock Providers – Displays the DLL modules registered for Winsock protocols, including Winsock service providers.
An anti-malware software do not scan Winsock Service Providers as it is treated as a safe zone. Taking advantage of this, some malware enter into your system as a Winsock Service Provider. But Autorun Analyzer can identify the DLL modules loaded by Winsock Service Providers and notify you if they are untrusted. It also enables you to remove those untrusted modules from your system.
Print – Displays the DLLs load into the print spoolers configured as services to start with Windows. Some malware find their entry through Print spooling service to start themselves automatically during system start-up.
LSA Providers – Displays the DLL modules registered by Local Security Authority (LSA) authentication, notification and security packages.
Network – Displays the DLL modules loaded by network connection services.
Its better that you do this in categories
If you are not able to delete some entries, just leave it.
Try to not delete entries by Publisher "Microsoft Corporation".
DELETE ALL UNNECESSARY ENTRIES
Start Autorun Analyzer
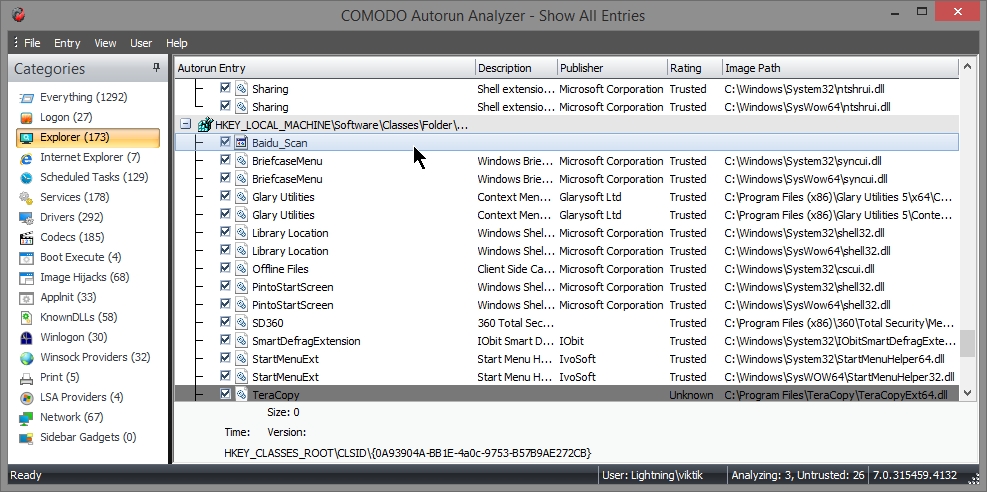
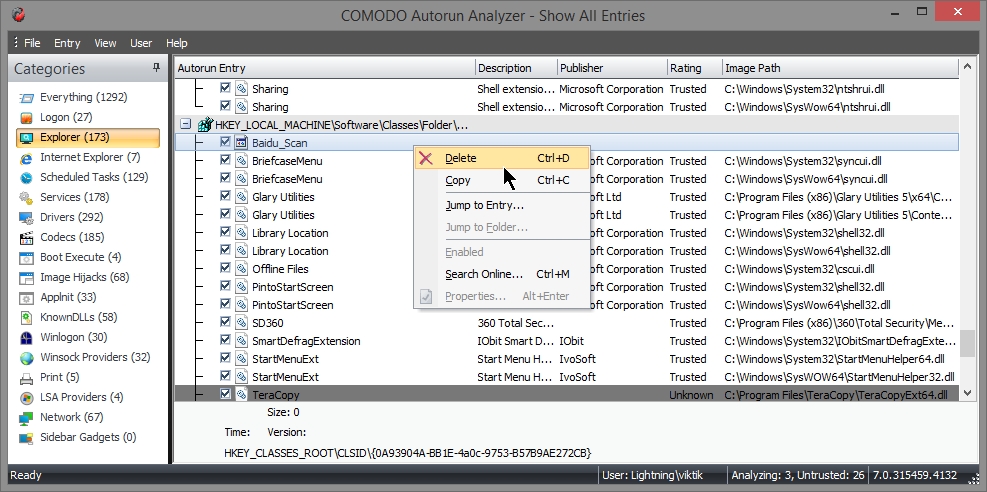
- In explorer shell extension entry , you can see Baidu entry with no Image path. Since the file does not exist in system the entry associated with must be deleted.
- Delete the entry
- Scheduled task
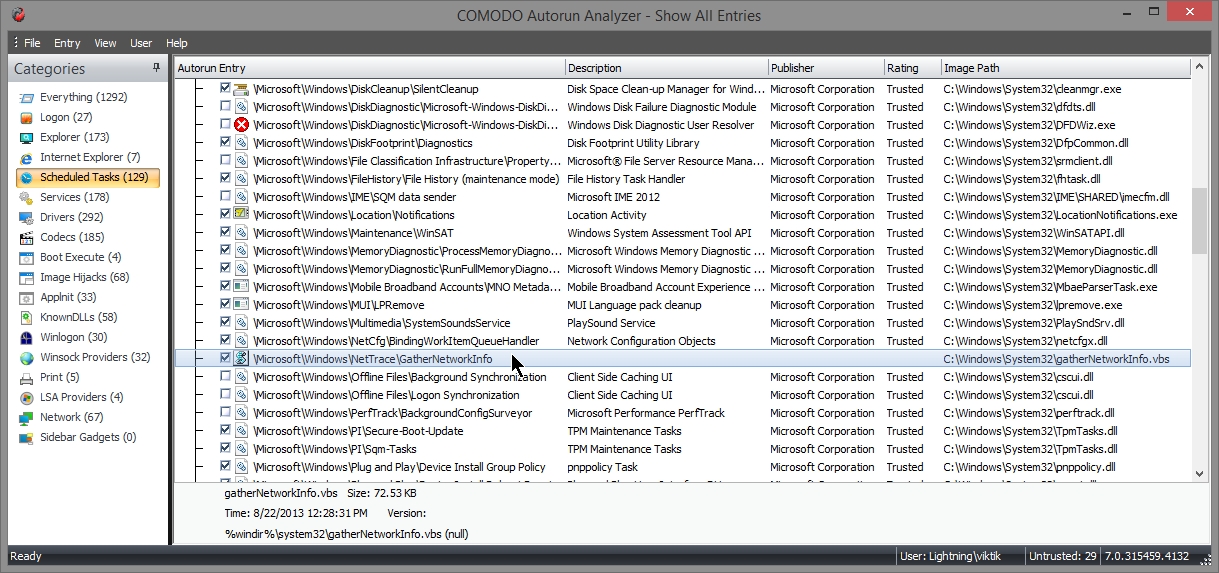
- Below you can see one entry which has “image path” but there is no description or publisher.
- You should look online for it.
- The file “gathernetworkinfo.vbs” is safe so you don not need to delete it
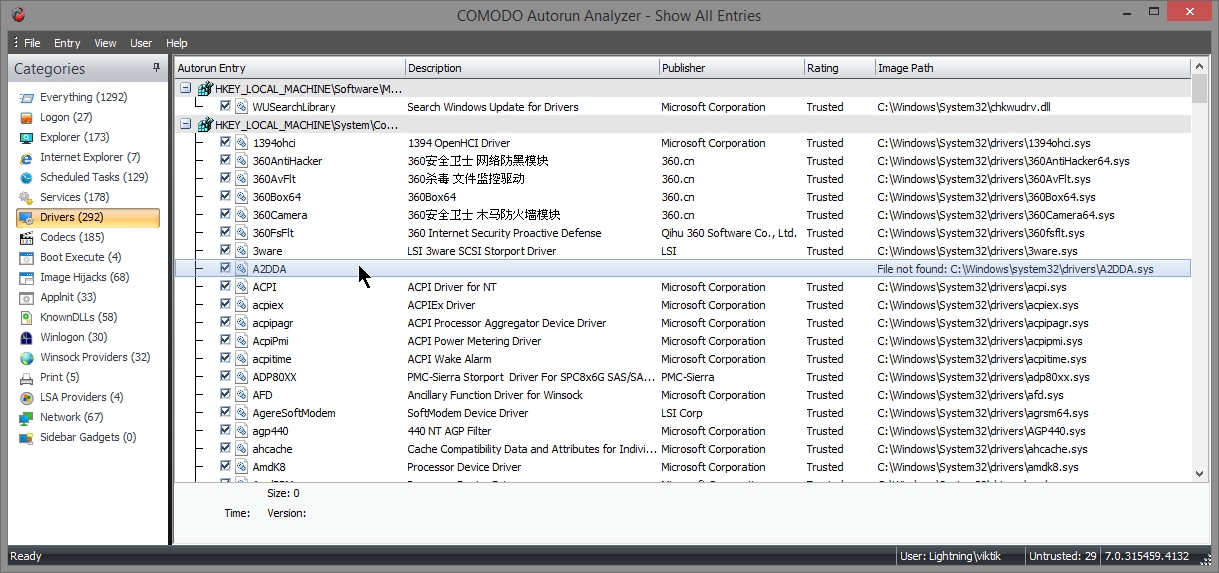
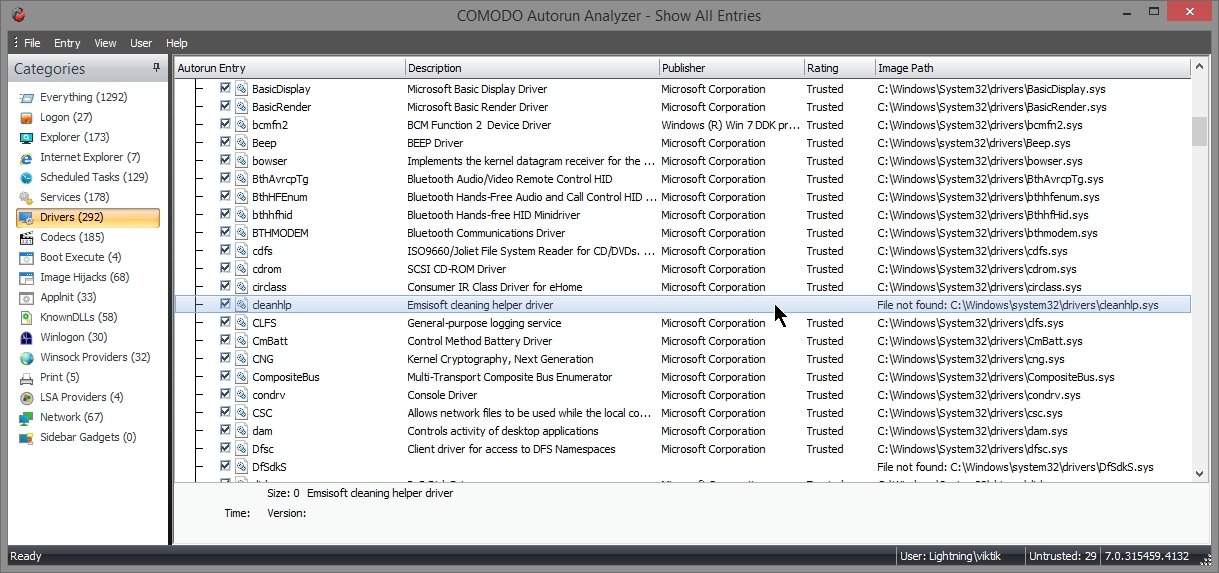
- Here is driver entry with name "A2DDA" with “Image path” saying "File not found". It means the file in not there in the hard disk.
- It can be deleted.
- Here is driver entry named "cleanhlp" for which the file does not exist . So its safe to delete the entry
- Again file not found in hard disk. It can be deleted.
- Here are two entries with o description & Publisher info. But the files exist in system and are safe.
- So no need to delete it
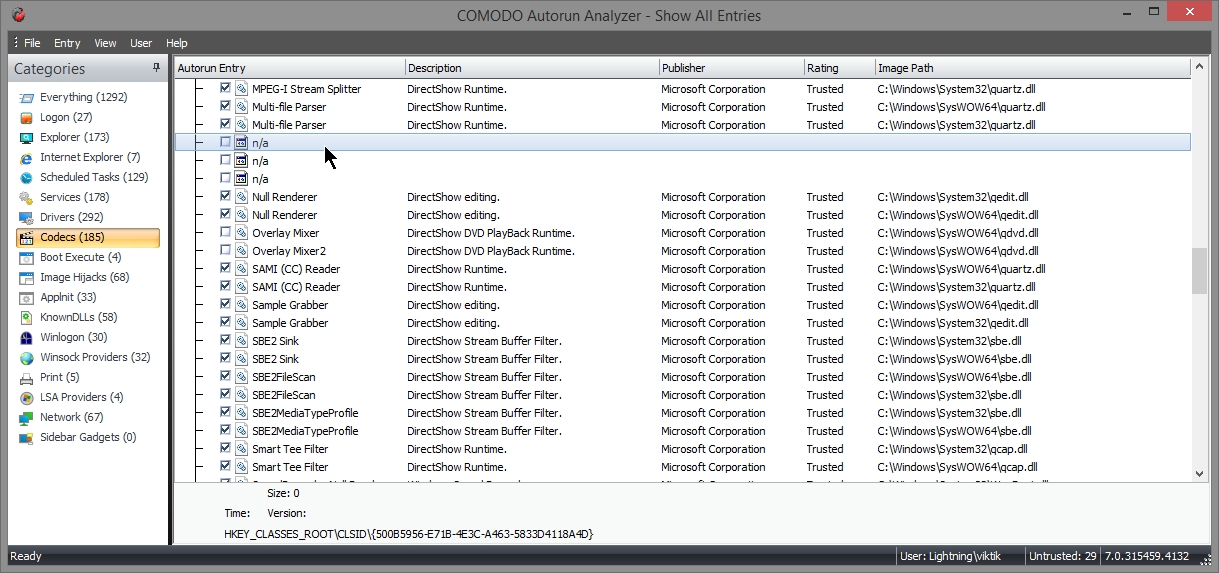
- Here is codecs entry. Three entries are there with no file in hard disk.
- So it can be deleted
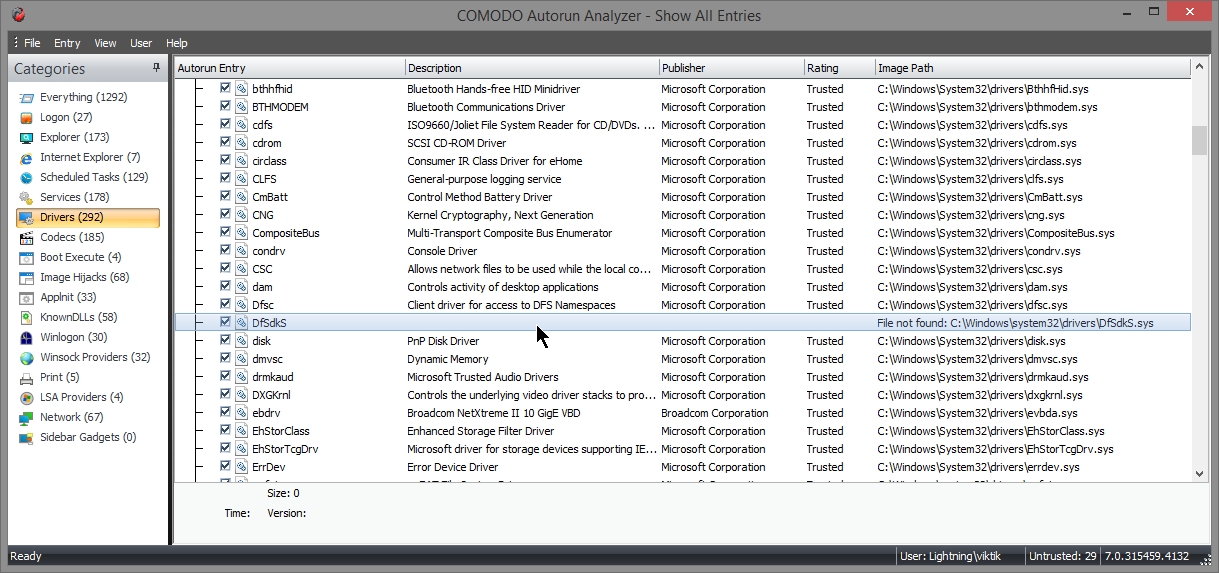
- Here again “file not found” . It can be deleted.
- here again “File not found”. It can be deleted.
- here in LSA provider. Entry size is zero.
- It can be deleted.

- Delete or Untick the entries for which “Image Path” shows “File not found”


Reboot when done
Last edited: