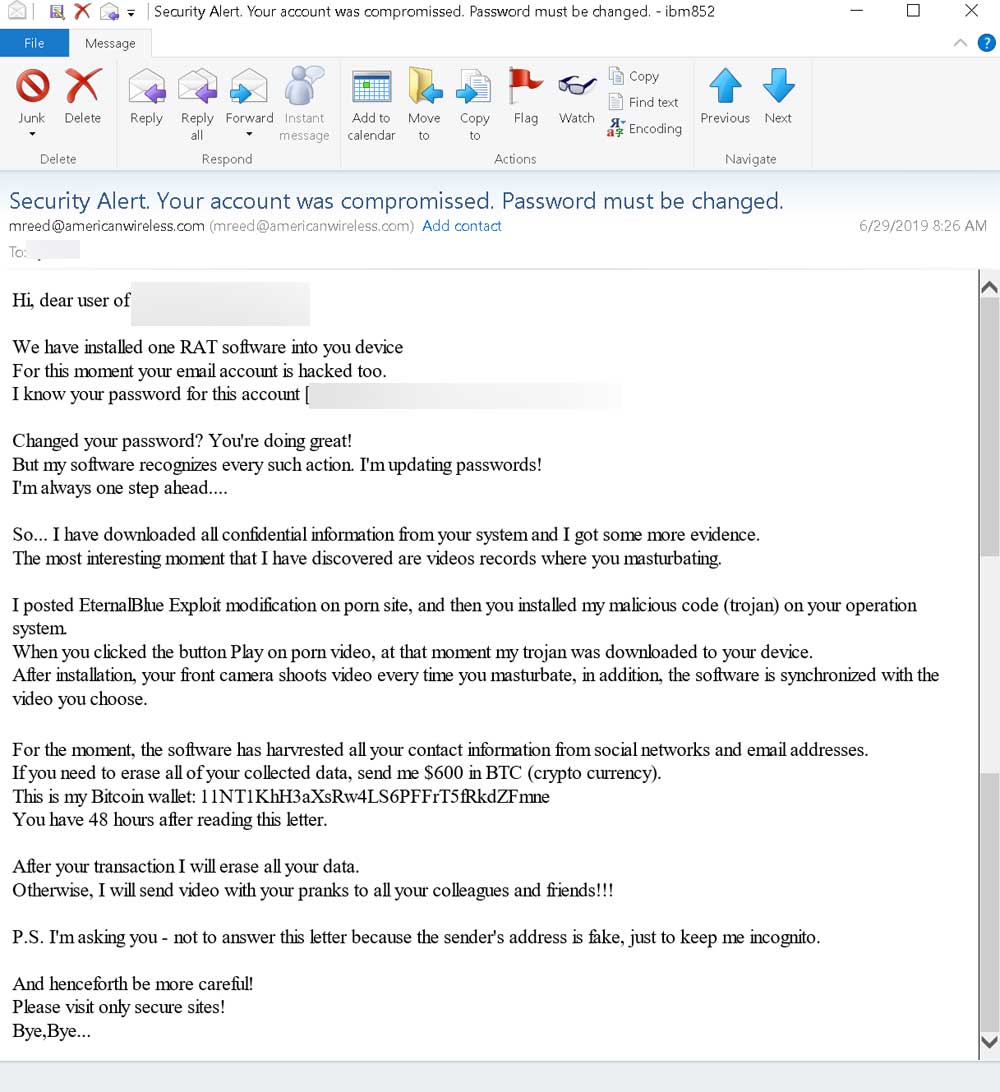
An extortion scam is being distributed that claims a Remote Access Trojan, or RAT, was installed on your computer using the EternalBlue exploit. The scammers then go on to say that they used the RAT to take videos of you on adult web sites and that you must pay a ransom or they will send it to all of your contacts.
EternalBlue is an exploit allegedly created by the NSA that targets a vulnerability in the SMBv1 protocol. This vulnerability allows attackers to execute commands on a vulnerable computer that can be used to install malware.
The extortion emails being distributed have a subject of "Security Alert. Your account was compromised. Password must be changed" and spins a tale that while visiting a porn site, the EternalBlue exploit was triggered to install a Remote Access Trojan on your computer.
This Trojan was then allegedly used to take videos of you, steal your contacts, and your passwords. It goes on to say if you do not pay a $600 extortion demand, the attacker will send your video to all of your contacts.
The reality is that this is just a scam and the senders have not utilized any exploits on your computer, there is no RAT installed, and there are no videos of you while using an adult web site. Any passwords or email addresses listed in the email are simply from data breaches where your account info was publicly disclosed.