DNC Hackers Target Lawmakers With Decoy Sites; Some Senators Demand Action

The cyber espionage group that executed a campaign against the Democratic Party has been targeting the U.S. Senate, a cybersecurity firm warns. The news comes as Senate minority staffers have released a report warning that Russia will likely attempt to disrupt 2018 and 2020 U.S. elections, which calls on the White House to do more to counter such efforts.
See Also: Addressing the Identity Risk Factor in the Age of 'Need It Now'
Tokyo-based cybersecurity firm Trend Micro says the groundwork for an attack against the Senate began last summer. It says the attackers have been using infrastructure that's been tied to attacks launched in 2016 and 2017 by the cyber espionage group known as Fancy Bear, aka APT28, Group 74, Pawn Storm, Sofacy, Strontium and Tsar Team, among other names. Many information security experts believe Fancy Bear is tied to Russia's GRU military intelligence agency (see Fancy Bear Invites DC Conference-Goers to Install Malware).
This campaign began last June, when phishing sites were set up to mimic the Senate's Active Directory Federation Services, which provides single sign-on access to systems and applications located across organizational boundaries, Trend Micro says.
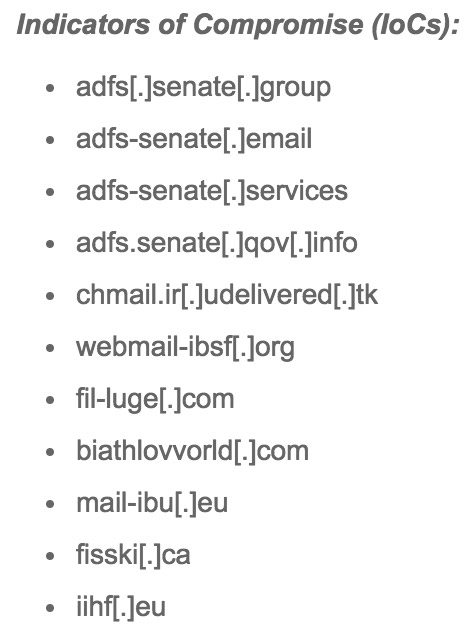
Decoy servers used in recent months to target the U.S. Senate and others by using lookalike but fake domain names. (Source: Trend Micro)
"The real ADFS server of the U.S. Senate is not reachable on the open internet, however, phishing of users' credentials on an ADFS server that is behind a firewall still makes sense," Trend Micro says in a report released Friday, authored by its senior threat researcher Feike Hacquebord. "In case an actor already has a foothold in an organization after compromising one user account, credential phishing could help him get closer to high-profile users of interest," it adds.
The Associated Press first reported on the findings.
The Senate's Office of the Sergeant at Arms, which is responsible for Senate security, including cybersecurity matters, could not be immediately reached for comment.
Trend Micro says the same attack infrastructure and decoy website tactics were used last year to try and disrupt German elections, as well as the campaign being run by Emmanuel Macron, now the president of France, who was also targeted during elections via an 11th hour document dump (see Au Revoir, Alleged Russian 'Fancy Bear' Hackers).
The company has also tied the same attack infrastructure and tactics to campaigns targeting Turkish and Montenegro parliaments, the World Anti-Doping Agency, nuclear power generator Westinghouse Electric Company as well as the earlier breach of the Democratic National Committee and Clinton campaign chairman John Podesta.
U.S. intelligence agencies in January 2017 alleged that Russian President Vladimir Putin directly authorized the campaign against Clinton (see Report: U.S. Weighs DNC Hacking Charges Against Russians).
More recently, Fancy Bear has been targeting organizations tied to the Olympic Winter Games being held from Feb. 9 to 25 in Pyeongchang County, South Korea, Trend Micro says, noting that this is repeat behavior. "In 2016, Pawn Storm had some success in compromising WADA (the World Anti-Doping Agency) and TAS-CAS (the Court of Arbitration for Sport)," it says. "At that time, Pawn Storm sought active contact with mainstream media either directly or via proxies and had influence on what some of them published."
The more recent efforts appear to be tied, in part, to last month's decision by the International Olympic Committee to immediately suspend the Russian Olympic Committee. The IOC also banned some Russian athletes for life and said it would invite individual Russian athletes to the Winter Olympics, provided they meet specific conditions determined by a panel.
The IOC's decision was endorsed by WADA.
Information Warfare, Social Media Style
Trend Micro's report also warns of the ease attackers continue to have when influencing public opinion via social media platforms. Fancy Bear, for example, maintains multiple Twitter accounts, and has recently been using them to criticize WADA (see No Shock: Russia Confirms 'Cyber War' Efforts).
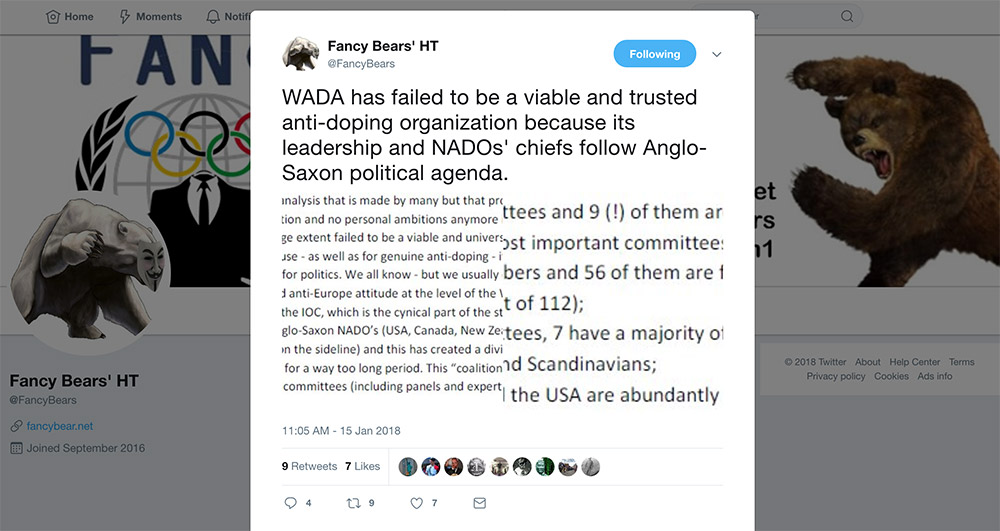
Tweet posted to @FancyBears on Jan. 15 criticizes WADA.
"Publishing stolen data together with spreading fake news and rumors on social media gives malicious actors powerful tools," Trend Micro says. "While a successful influence campaign might seem relatively easy to do, it needs a lot of planning, persistence and resources to be successful. Some of the basic tools and services, like ones used to spread fake news on social media, are already being offered as a service in the underground economy."
Expect other attackers to learn from these types of "influence ops," Trend Micro says. It's already seeing signs of such attacks from developing countries, including a cyber espionage group it calls C Major that "primarily targets the Indian military," but which has also built botnets aimed at "compromised targets in Iranian universities, Afghanistan and Pakistan" and more recently begun compromising "military and diplomatic targets in the West."
Senate Issues Russia Warning
U.S. concern over Russia's information warfare tactics continues to mount. And unless the U.S. government acts now, it risks seeing the Russian government disrupt 2018 and 2020 U.S. elections, a new Senate minority report warns.
"For years, Vladimir Putin's government has engaged in a relentless assault to undermine democracy and the rule of law in Europe and the United States," writes Sen. Benjamin Cardin, D-Maryland, in the introduction to the report, "Putin's Asymmetric Assault On Democracy In Russia And Europe: Implications For U.S. National Security," which was prepared for the Senate's Committee on Foreign Relations and released last week.
Senate minority staff report, "Putin's Asymmetric Assault On Democracy In Russia And Europe: Implications For U.S. National Security," was prepared for the Senate's Committee on Foreign Relations and released last week.
"Mr. Putin's Kremlin employs an asymmetric arsenal that includes military invasions, cyberattacks, disinformation, support for fringe political groups, and the weaponization of energy resources, organized crime and corruption," the report reads. "The Kremlin has refined the use of these tools over time, and these attacks have intensified in scale and complexity across Europe. If the United States fails to work with urgency to address this complex and growing threat, the regime in Moscow will become further emboldened. It will continue to develop and refine its arsenal to use on democracies around the world, including against U.S. elections in 2018 and 2020."
The operational security expert known as the Grugq, referring to the report, says that it's "worth knowing it exists and seeing what lessons the Americans are drawing from a return to disinformation campaigns."
The report looks at other regions that have been targeted and how they have responded, citing examples from Germany, Spain, France, the Nordic and Baltic states, as well as efforts being coordinated by cyber defense centers launched by both NATO and the EU, among others (see Microsoft Battles Fancy Bear Hackers - With Lawyers).
But Congressional efforts to combat the problem are being stymied, the report alleges. "In early 2017, Congress provided the State Department's Global Engagement Center the resources and mandate to address Kremlin disinformation campaigns, but operations have been stymied by the department's hiring freeze and unnecessarily long delays by its senior leadership in transferring authorized funds to the office," the report says. The report also says President Donald Trump's refusal to call out Russian interference has created a "leadership vacuum" that stymies effective response.
The White House could not be immediately reached for comment.
Lawmakers Demand Action
But other lawmakers have demanded that the administration do more.
"Last year, FBI Director [James] Comey said he was certain that Senate IT systems have been targeted and the attorney general said we weren't doing enough to prepare for Russia's next attack," U.S. Senator Ben Sasse, R-Nebraska, a member of the Senate Armed Services Committee, said in a statement
"The administration needs to take urgent action to ensure that our adversaries cannot undermine the framework of our political debates," he added, calling on Attorney General Jeff Sessions to "come back to Congress and explain what steps he's taken since last year."
