- Oct 23, 2012
- 12,527
Malware Investigator is FBI’s own solution for analyzing computer threats and it was presented at the Virus Bulletin security conference in Seattle this month.
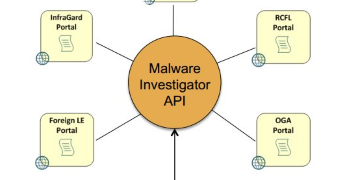
In a presentation by a special agent, it was announced that the system would be open to outside individuals such as other government agencies, law enforcement, researchers, and private sector partners.
Partners outside FBI will be given access to the platform
Entities that have established a relation with the Bureau will be able to benefit from the details provided by Malware Investigator.
According to the slides of the presentation, it will be available as a web service through an API that can be integrated into other systems; organizations and individuals are free to “share as much or as little intelligence, as desired.”
Through this approach, both the FBI and the private sector take advantage of a common database with significant information about malware.
With input from multiple sources, Malware Investigator can expand at a more rapid pace; this looks like a tactic to quickly build up the database.
Special Agent Jonathan Burns, program manager in the FBI's Advanced Digital Forensics Program, said that a separate portal would be developed for outside access to the tool.
Malware Investigator is an intelligence platform
With development started in 2013, the platform aims at characterizing malware and establishing a relationship between various samples. At the moment, it is designed as an 80% solution for malware analysis and as help to investigate incidents and respond to them.
The information reported after malware input into the system includes file hashes (MD5, SHA-1, SHA-256, SSDEEP), details about threat similarities (fuzzy and section hashing), as well as behavior of the malware (file system modification, handling of processes, registry changes, network connections).
This type of approach should be more efficient than wasting time waiting for reverse engineering. Additional intelligence is gathered from observing the behavior of malware over time.
A security researcher going by the handle @9bplus used the features in the paid version of VirusTotal to track the activity of cybercriminals behind NetTraveler that tested the malware.
He devised a scoring system that would bring out similarities between different samples based on the pattern used in their filename, thus establishing a connection between them.
The next step was to classify the account holders by monitoring their behavior and additional details provided through VirusTotal. “If implemented properly, it’s possible to automate the discovery of likely actor activity for an analyst to review,” said the researcher.
By correlating malware samples, the FBI system could reveal a shift in cybercriminal activity and the threats they switch to.

In a presentation by a special agent, it was announced that the system would be open to outside individuals such as other government agencies, law enforcement, researchers, and private sector partners.
Partners outside FBI will be given access to the platform
Entities that have established a relation with the Bureau will be able to benefit from the details provided by Malware Investigator.
According to the slides of the presentation, it will be available as a web service through an API that can be integrated into other systems; organizations and individuals are free to “share as much or as little intelligence, as desired.”
Through this approach, both the FBI and the private sector take advantage of a common database with significant information about malware.
With input from multiple sources, Malware Investigator can expand at a more rapid pace; this looks like a tactic to quickly build up the database.
Special Agent Jonathan Burns, program manager in the FBI's Advanced Digital Forensics Program, said that a separate portal would be developed for outside access to the tool.
Malware Investigator is an intelligence platform
With development started in 2013, the platform aims at characterizing malware and establishing a relationship between various samples. At the moment, it is designed as an 80% solution for malware analysis and as help to investigate incidents and respond to them.
The information reported after malware input into the system includes file hashes (MD5, SHA-1, SHA-256, SSDEEP), details about threat similarities (fuzzy and section hashing), as well as behavior of the malware (file system modification, handling of processes, registry changes, network connections).
This type of approach should be more efficient than wasting time waiting for reverse engineering. Additional intelligence is gathered from observing the behavior of malware over time.
A security researcher going by the handle @9bplus used the features in the paid version of VirusTotal to track the activity of cybercriminals behind NetTraveler that tested the malware.
He devised a scoring system that would bring out similarities between different samples based on the pattern used in their filename, thus establishing a connection between them.
The next step was to classify the account holders by monitoring their behavior and additional details provided through VirusTotal. “If implemented properly, it’s possible to automate the discovery of likely actor activity for an analyst to review,” said the researcher.
By correlating malware samples, the FBI system could reveal a shift in cybercriminal activity and the threats they switch to.