Malware is usually generated by compiling it from source code, or by using automated software that takes certain input parameters and outputs a customized malware payload on a per-campaign basis.
The latter are known in the industry as malware builders and usually come as command-line applications or GUI-based tools.
The author of the FireCrypt ransomware uses a command-line application that automates the process of putting FireCrypt samples together, allowing him to modify basic settings without having to tinker with bulky IDEs that compile its source code.
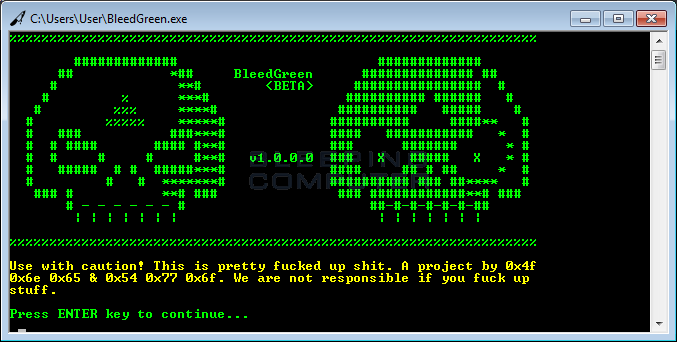
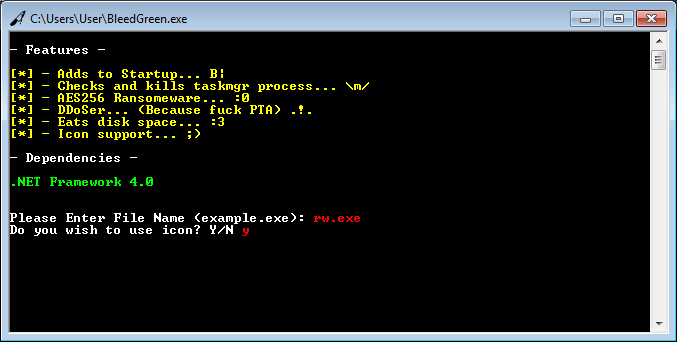
FireCrypt's builder is named BleedGreen (seen below), and allows the FireCrypt author to generate a unique ransomware executable, give it a custom name, and use a personalized file icon. Compared to other ransomware builders, this is a very low-end application. Similar builders usually allow crooks to customize a wider set of options, such as the Bitcoin address where to receive payments, the ransom demand value, contact email address, and more.
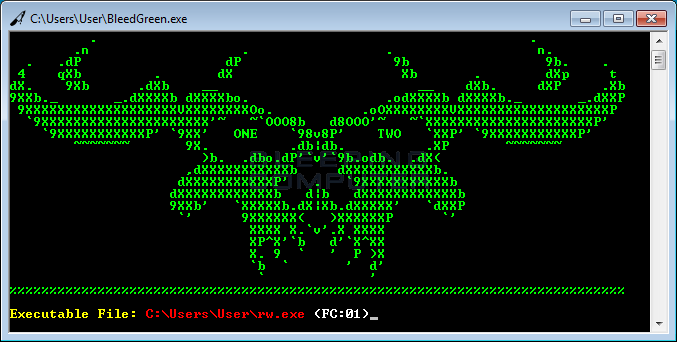
The builder's role, besides disguising an EXE file under a PDF or DOC icon, is also to slightly alter the ransomware's binary, in order to generate a file with a different hash at every new compilation.
The technique is often used by malware developers to create so-called "polymorphic malware" that's harder to detect by standard antivirus software. According to MalwareHunterTeam, "the builder is very basic, so this shouldn't help anything against real AVs."
Read more: FireCrypt Ransomware Comes With a DDoS Component
The latter are known in the industry as malware builders and usually come as command-line applications or GUI-based tools.
The author of the FireCrypt ransomware uses a command-line application that automates the process of putting FireCrypt samples together, allowing him to modify basic settings without having to tinker with bulky IDEs that compile its source code.
FireCrypt's builder is named BleedGreen (seen below), and allows the FireCrypt author to generate a unique ransomware executable, give it a custom name, and use a personalized file icon. Compared to other ransomware builders, this is a very low-end application. Similar builders usually allow crooks to customize a wider set of options, such as the Bitcoin address where to receive payments, the ransom demand value, contact email address, and more.



The builder's role, besides disguising an EXE file under a PDF or DOC icon, is also to slightly alter the ransomware's binary, in order to generate a file with a different hash at every new compilation.
The technique is often used by malware developers to create so-called "polymorphic malware" that's harder to detect by standard antivirus software. According to MalwareHunterTeam, "the builder is very basic, so this shouldn't help anything against real AVs."
Read more: FireCrypt Ransomware Comes With a DDoS Component