- Aug 30, 2012
- 6,598
Update at 2:32pm PST / 5:32pm EST: Firefox released a fix for this a few minutes ago. Update to Firefox 50.0.2 now to patch this vulnerability. Tor have also released a fix with version 6.0.7 of their browser.There is also a Thunderbird fix out, version 45.5.1. I also posted an extended update at the end of the post including data indicating this exploit may be part of a law enforcement operation.
/End Update.
We’re publishing this as an emergency bulletin for our customers and the larger web community. A few hours ago a zero day vulnerability emerged in the Tor browser bundle and the Firefox web browser. Currently it exploits Windows systems with a high success rate and affects Firefox versions 41 to 50 and the current version of the Tor Browser Bundle which contains Firefox 45 ESR.
If you use Firefox, we recommend you temporarily switch browsers to Chrome, Safari or a non-firefox based browser that is secure until the Firefox dev team can release an update. The vulnerability allows an attacker to execute code on your Windows workstation. The exploit is in the wild, meaning it’s now public and every hacker on the planet has access to it. There is no fix at the time of this writing.
Currently this exploit causes a workstation report back to an IP address based at OVH in France. But this code can likely be repurposed to infect workstations with malware or ransomware. The exploit code is now public knowledge so we expect new variants of this attack to emerge rapidly.
This is a watering hole attack, meaning that a victim has to visit a website that contains this exploit code to be attacked. So our forensic team is keeping an eye on compromised WordPress websites and we expect to see this code show up on a few of them during the next few days. An attackers goal would be to compromise workstations of visitors to WordPress websites that have been hacked.
How this unfolded
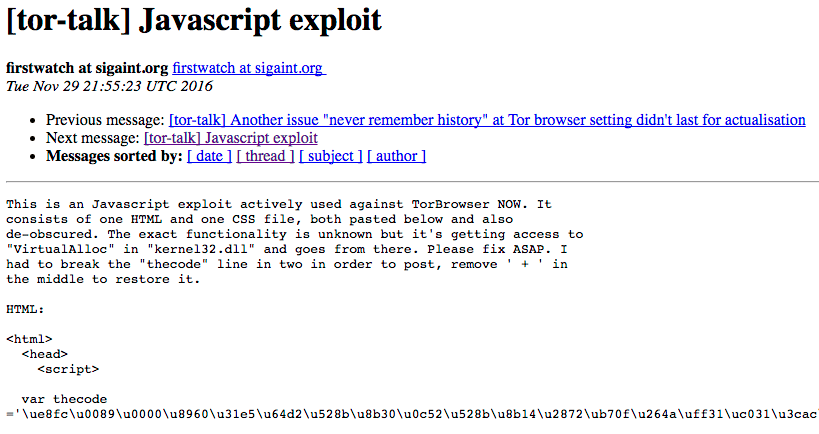
On Tuesday just after noon Pacific time, someone published a 0 day exploit for Firefox and Tor to the tor browser mailing list.
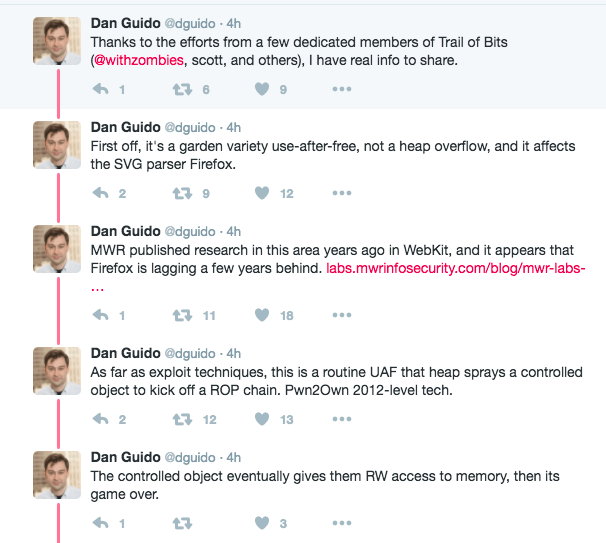
Since then researcher Dan Guido posted a series of tweets with some analysis of the exploit itself.
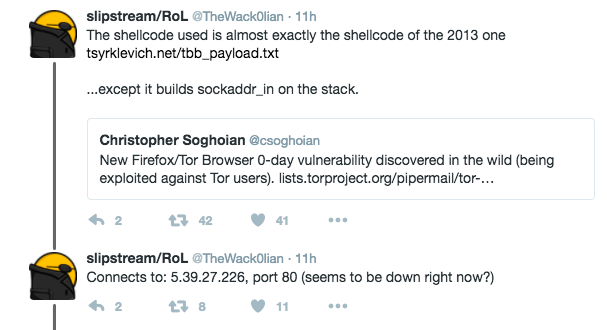
Twitter user @TheWack0lian noticed the shellcode (code that executes on your Windows workstation once exploited) is very similar to shellcode likely used by the FBI back in 2013 to deanonymize visitors to child porn websites hosted by FreedomHosting. The FBI confirmed that they compromised that server and days later it was serving malware that would infect site visitor workstations. The code then reported site visitor real IP addresses, MAC addresses (network card hardware address) and windows computer name to a central server. This code is very similar.
What we found
The shell code in this attack calls back to IP address 5.39.27.226, which was a web server hosted at OVH in France. The site is now down. Our own research shows that if you look up this IP address in Shodan, it had an SSL certificate that is a wildcard for the energycdn.com domain name. That site for energycdn is simplistic and according to archive.org, it has not changed since 2014.
Googling energycdn.com shows that the domain is used frequently to host pirated content. Norton Safe Web reports it hosts viruses. Google Safe Browsing transparency report says the domain hosts malware and redirects to malicious sites.
One could speculate that the server at 5.39.27.226 was used by energycdn.com as one of their servers to host pirated content. Perhaps the server was compromised by whoever controls energycdn to host that content and then was reinfected by the perpetrator of this new malware variant. But we’re speculating.
Additional press coverage
Update at 2:03pm PST / 5:03PM EST on Wednesday:
Vice’s Motherboard have provided an update 2 hours ago on this issue from a few sources. Here’s the summary and some context:
Remember, this attack targeted Tor users specifically and the goal of the attack was to reveal the identity of the browser operator. It is also very similar to a 2013 attack that was likely launched on child porn website visitors by the FBI to identify and arrest them. The fact that this exploit simply tries to reveal a user’s identity rather than infect them with malware indicates it is being perpetrated by a law enforcement branch in some country.
Vice is now reporting that their sources are saying this exploit is active on a child porn website called The GiftBox Exchange. There are also warnings on the Dark Web about the presence of this malware. In my opinion this strongly indicates that this exploit is in fact the FBI or another agency targeting visitors of The GiftBox Exchange.
Vice has reached out to FBI and Europol. FBI declined to comment and Europol did not respond.
My guess is that you will hear about this again a few months from now when the indictments start to emerge. If that is the case, and it is confirmed this is an FBI operation, this would make it clear that using 0 day vulnerabilities to actively exploit browsers for surveillance is the new modus operandi of the FBI. This technique was used in 2013 to target visitors of websites on FreedomHosting. It was used again to target and indict visitors of Playpen in 2015. And this technique is being used again today.
Firefox have now released a fix with version 50.0.2.
Tor released an update to their browser today that fixes this vulnerability.
Thunderbird have also released a security fix related to this.
You can find the actual Firefox vulnerability report here.
/End Update.
We’re publishing this as an emergency bulletin for our customers and the larger web community. A few hours ago a zero day vulnerability emerged in the Tor browser bundle and the Firefox web browser. Currently it exploits Windows systems with a high success rate and affects Firefox versions 41 to 50 and the current version of the Tor Browser Bundle which contains Firefox 45 ESR.
If you use Firefox, we recommend you temporarily switch browsers to Chrome, Safari or a non-firefox based browser that is secure until the Firefox dev team can release an update. The vulnerability allows an attacker to execute code on your Windows workstation. The exploit is in the wild, meaning it’s now public and every hacker on the planet has access to it. There is no fix at the time of this writing.
Currently this exploit causes a workstation report back to an IP address based at OVH in France. But this code can likely be repurposed to infect workstations with malware or ransomware. The exploit code is now public knowledge so we expect new variants of this attack to emerge rapidly.
This is a watering hole attack, meaning that a victim has to visit a website that contains this exploit code to be attacked. So our forensic team is keeping an eye on compromised WordPress websites and we expect to see this code show up on a few of them during the next few days. An attackers goal would be to compromise workstations of visitors to WordPress websites that have been hacked.
How this unfolded
On Tuesday just after noon Pacific time, someone published a 0 day exploit for Firefox and Tor to the tor browser mailing list.

Since then researcher Dan Guido posted a series of tweets with some analysis of the exploit itself.

Twitter user @TheWack0lian noticed the shellcode (code that executes on your Windows workstation once exploited) is very similar to shellcode likely used by the FBI back in 2013 to deanonymize visitors to child porn websites hosted by FreedomHosting. The FBI confirmed that they compromised that server and days later it was serving malware that would infect site visitor workstations. The code then reported site visitor real IP addresses, MAC addresses (network card hardware address) and windows computer name to a central server. This code is very similar.

What we found
The shell code in this attack calls back to IP address 5.39.27.226, which was a web server hosted at OVH in France. The site is now down. Our own research shows that if you look up this IP address in Shodan, it had an SSL certificate that is a wildcard for the energycdn.com domain name. That site for energycdn is simplistic and according to archive.org, it has not changed since 2014.
Googling energycdn.com shows that the domain is used frequently to host pirated content. Norton Safe Web reports it hosts viruses. Google Safe Browsing transparency report says the domain hosts malware and redirects to malicious sites.
One could speculate that the server at 5.39.27.226 was used by energycdn.com as one of their servers to host pirated content. Perhaps the server was compromised by whoever controls energycdn to host that content and then was reinfected by the perpetrator of this new malware variant. But we’re speculating.
Additional press coverage
Update at 2:03pm PST / 5:03PM EST on Wednesday:
Vice’s Motherboard have provided an update 2 hours ago on this issue from a few sources. Here’s the summary and some context:
Remember, this attack targeted Tor users specifically and the goal of the attack was to reveal the identity of the browser operator. It is also very similar to a 2013 attack that was likely launched on child porn website visitors by the FBI to identify and arrest them. The fact that this exploit simply tries to reveal a user’s identity rather than infect them with malware indicates it is being perpetrated by a law enforcement branch in some country.
Vice is now reporting that their sources are saying this exploit is active on a child porn website called The GiftBox Exchange. There are also warnings on the Dark Web about the presence of this malware. In my opinion this strongly indicates that this exploit is in fact the FBI or another agency targeting visitors of The GiftBox Exchange.
Vice has reached out to FBI and Europol. FBI declined to comment and Europol did not respond.
My guess is that you will hear about this again a few months from now when the indictments start to emerge. If that is the case, and it is confirmed this is an FBI operation, this would make it clear that using 0 day vulnerabilities to actively exploit browsers for surveillance is the new modus operandi of the FBI. This technique was used in 2013 to target visitors of websites on FreedomHosting. It was used again to target and indict visitors of Playpen in 2015. And this technique is being used again today.
Firefox have now released a fix with version 50.0.2.
Tor released an update to their browser today that fixes this vulnerability.
Thunderbird have also released a security fix related to this.
You can find the actual Firefox vulnerability report here.
