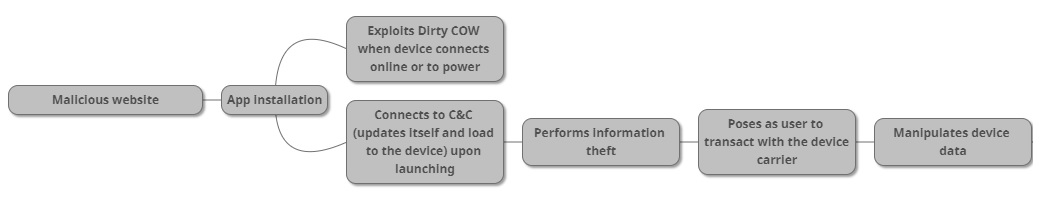
ZNIU malware uses Dirty COW to root devices, plant backdoor
Yesterday, security researchers from Trend Micro published a report detailing a new malware family named ZNIU that uses Dirty COW to root devices and plant a backdoor.
Researchers say attackers use this backdoor to collect information on infected devices. The second stage of the attack happens only if the user is located in China. Attackers use the full control the backdoor grants them over the device to subscribe the user to premium SMS numbers that benefit a local company.
Trend Micro says it discovered more than 1,200 malicious apps that carry ZNIU available via various online websites. Most of the infected apps were gaming and pornography related.
The company says it detected about 5,000 users infected with the ZNIU malware, but the number could be bigger as the company had visibility only inside devices protected by its mobile security solution.
ZNIU made victims across 40 countries, but most were located in China and India.