- Feb 7, 2014
- 1,540
An estimated 500 million Android phones don't completely wipe data when their factory reset option is run, a weakness that may allow the recovery of login credentials, text messages, e-mails, and contacts, computer scientists said Thursday.
In the first comprehensive study of the effectiveness of the Android feature, Cambridge University researchers found that they were able to recover data on a wide range of devices that had run factory reset. The function, which is built into Google's Android mobile operating system, is considered a crucial means for wiping confidential data off of devices before they're sold, recycled, or otherwise retired. The study found that data could be recovered even when users turned on full-disk encryption.
Based on the devices studied, the researchers estimated that 500 million devices may not fully wipe disk partitions where sensitive data is stored and 630 million phones may not wipe internal SD cards where pictures and video are often kept. The findings, published in a research paper titled Security Analysis of Android Factory Resets, are sure to be a wake-up call for individual users and large enterprises alike.
"It's going to have a major impact in organizations that have fairly mature established disposal practices because they're not effective," Kenn White, a North Carolina-based computer scientist who has read the paper, told Ars. "It's a staggering number of devices out there that are exposed, and it's not just somebody's Gmail password. It's images, photos, text, chat. It's all these things that are private that you think if you've reset it you've reset it."
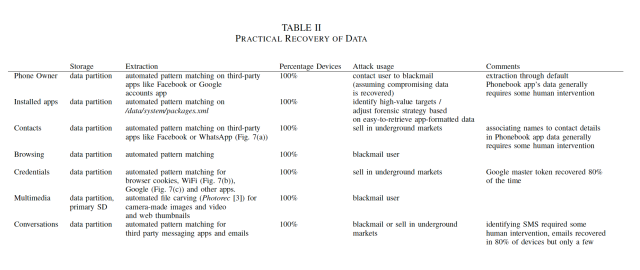
The researchers tested the factory reset of 21 Android smartphones that ran versions 2.3.x to 4.3 of the mobile OS and were sold by five manufacturers. All of the phones retained at least some fragments of old data, including contact data stored in the phone app and third-party apps such as Facebook and What'sApp, images and video from the camera, and text-based conversations from SMS and e-mail apps. In 80 percent of phones, the researchers were able to extract the master token Android uses to give access to most Google user data, such as Gmail and Google calendar.
Enlarge
Simon and Anderson
As an experiment, the researchers recovered a master token from a reset phone and restored the credential file.
"After the reboot, the phone successfully re-synchronised contacts, emails, and so on," they reported. "We recovered Google tokens in all devices with flawed Factory Reset, and the master token 80% of the time. Tokens for other apps such as Facebook can be recovered similarly. We stress that we have never attempted to use those tokens to access anyone's account."
You are not storing data
There were multiple reasons for the reset failures. In some cases, manufacturers didn't include the software drivers necessary to fully wipe flash chips that the smartphones used for non-volatile memory storage. More generally, and as researchers demonstrated more than four years ago, the composition of flash drives make them dangerously hard to erase. Drives are usually over-provisioned to accommodate for portions that are faulty from the beginning or wear out over time. As a result, they have more internal space than indicated by the operating system. As a researcher known as Bunnie observed during a presentation at the 2013 Chaos Communication Congress, when using Flash drives, "you are not storing data, you are storing a probabilistic approximation of your data." Deleting all of it with certainty, it seems, is exceedingly hard.
30C3: Exploration and Exploitation of an SD Memory Card.
The researchers' experiments—which were conducted on second-hand phones obtained from January to May of last year—didn't test phones running Android versions past 4.3. It's not clear how factory reset functions in versions 4.4 and beyond compare with those studied. The researchers told Ars that it's "plausible some newer devices are also affected." Google officials didn't immediately respond to Ars' request for a comment.
One of the most concerning findings is that data users presume has been wiped during reset in many cases can be recovered and read even when a phone has been protected with full-disk encryption. That's because the file that stores the decryption key isn't erased during the factory-reset process. While the key is itself encrypted with a cryptographic salt and a user-selected PIN or password, recovery of the "crypto footer," as the encrypted file is known, gives an attacker everything needed to perform an offline cracking attack. Based on the data supplied in this post, security consultant White estimated successful cracks would take a matter of seconds for typical PINs and a matter of a few hours to a day for longer passwords.
The findings create a vexing predicament for people who want to sell or dispose of phones or who lose a phone and want to remotely wipe it. Probably the most effective thing to do with Android devices that offer full-disk encryption is to turn it on and use a randomly generated password that includes numbers, upper- and lower-case letters, and symbols, and has a minimum of 11 characters. While such passwords would take years or decades to crack, they also come at a price, since they would have to be entered each time the phone is unlocked. Given the difficulty of entering strong passwords into smartphone keyboards and the frequency with which most phones are unlocked, most users are likely to consider the requirement prohibitive.
Beyond encrypting the phone with a strong password, the researchers said end users can perform a factory reset and then fill up a partition of interest with random-byte files, with the aim of overwriting all unallocated space. Still, the third-party app that would fill the partition with random-byte files would have to be installed manually to prevent a Google token from residing on the wiped phone. One of the only other avenues left for end users is to destroy devices rather than sell or recycle them. That advice, however, doesn't apply to people who lose a device and use Android's remote wipe feature. The researchers went on to recommend a variety of technical changes that Google or device manufacturers can make to improve the reliability of Android's factory reset process.
Lest antivirus providers attempt to use the findings to promote remote wiping features in their products, the researchers pointed to a separate paper they also published Thursday titled Security Analysis of Consumer-Grade Anti-Theft Solutions Provided by Android Mobile Anti-Virus Apps. It uncovered significant wiping flaws in 10 Android apps downloaded hundreds of millions of times. "We conclude the only viable solutions are those driven by vendors themselves," they wrote.
PROMOTED COMMENTS
- dcf_lolSmack-Fu Master, in traininget Subscriptorjump to post
d4Njv wrote:
As of Lollipop the encryption key is no longer derived from a user-entered password (https://source.android.com/devices/tech ... encryption).
The issue isn't that the encryption key is derived from the user-entered password, it's that it's protected by it.
From the article:
Quote:
That's because the file that stores the decryption key isn't erased during the factory-reset process. While the key is itself encrypted with a cryptographic salt and a user-selected PIN or password, recovery of the "crypto footer," as the encrypted file is known, gives an attacker everything needed to perform an offline cracking attack.
Unless 5.0 does something different with the crypto footer on wipe this would still be an issue.
EDIT: just reread the linked android documentation page. Recovery of the data could still be possible but the offline cracking attack would have to occur on the device to take advantage of the TEE key. It would take longer but conceivably would still be possible (especially for short and purely numerical pins).
2 posts | registered Oct 20, 2014 - maphewykSmack-Fu Master, in trainingjump to post
SixnaHalfFeet wrote:
... Google has their data gathering algorithms built in, and there are issues like this continually popping up.
Seriously, why go Android? Choice/freedom? At what cost are the problems worth it? For me, it is not worth it.
This research proves many (most?) android phones are vulnerable. It does not prove that other phones are safe. Has anyone given the same level of study and analysis to wiped iPhone or Windows phone or Blackberry and found them secure?
The related story about flash storage being actually incredibly hard to erase indicates there is a lot of room for everyone to be nervous, regardless of device manufacturer.
10 posts | registered Jun 19, 2012

