Nathan Scott, a malware analyst for Malwarebytes, was able to crack the encryption system used by the Telecrypt ransomware, discovered two weeks ago by researchers from Kaspersky Lab.
The peculiar feature that made this threat unique was the ransomware's command and control (C&C) client-server communications channel, for which the operators chose to use the Telegram protocol, instead of HTTP or HTTPS like most ransomware does these days.
This made Telecrypt stand out, albeit its threat vector was low, since it only targeted Russian users with its first version, and only bothered showing the ransom note in Russia alone.
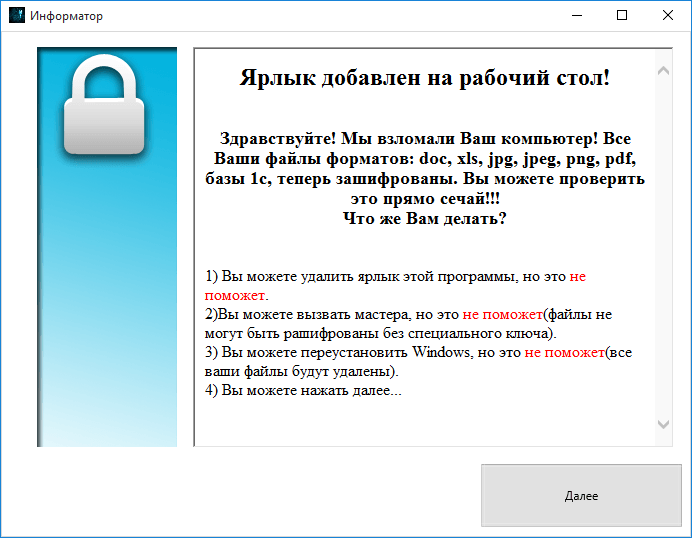
Telecrypt ransom note (via Kaspersky Lab)
You can get the Telecrypt ransomware decryptor created by Malwarebytes from this Box link.
Inside it you'll find two files: the decrypter itself and a text file with usage instructions. The decryptor's interface is self-explanatory, but make sure to read the usage instructions first.
The decryptor needs to run as the system administrator. In modern Windows versions, you can right-click it and select "Run as Administrator" from the drop-down menu. In older Windows versions you need to right-click the file, choose Properties, then the Compatibility tab, and select the "Run This Program As An Administrator" option.
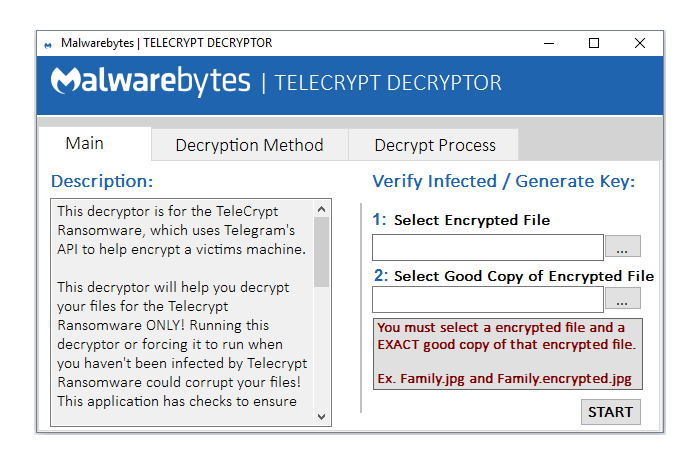
Telecrypt Decryptor
To run the Telecrypt decryptor, victims need a good and an encrypted version of the same file, so the decryptor can determine the ransomware's encryption key.
You can find unencrypted versions of your files in email accounts, file syncing services (Dropbox, Box), or from older system backups if you made any.
After the decryptor finds the encryption key, it will then present the user with the option to decrypt a list of all encrypted files, or from one specific folder. Telecrypt keeps a list of all encrypted files at "%USERPROFILE%\Desktop\База зашифр файлов.txt"
The peculiar feature that made this threat unique was the ransomware's command and control (C&C) client-server communications channel, for which the operators chose to use the Telegram protocol, instead of HTTP or HTTPS like most ransomware does these days.
This made Telecrypt stand out, albeit its threat vector was low, since it only targeted Russian users with its first version, and only bothered showing the ransom note in Russia alone.

Telecrypt ransom note (via Kaspersky Lab)
You can get the Telecrypt ransomware decryptor created by Malwarebytes from this Box link.
Inside it you'll find two files: the decrypter itself and a text file with usage instructions. The decryptor's interface is self-explanatory, but make sure to read the usage instructions first.
The decryptor needs to run as the system administrator. In modern Windows versions, you can right-click it and select "Run as Administrator" from the drop-down menu. In older Windows versions you need to right-click the file, choose Properties, then the Compatibility tab, and select the "Run This Program As An Administrator" option.

Telecrypt Decryptor
To run the Telecrypt decryptor, victims need a good and an encrypted version of the same file, so the decryptor can determine the ransomware's encryption key.
You can find unencrypted versions of your files in email accounts, file syncing services (Dropbox, Box), or from older system backups if you made any.
After the decryptor finds the encryption key, it will then present the user with the option to decrypt a list of all encrypted files, or from one specific folder. Telecrypt keeps a list of all encrypted files at "%USERPROFILE%\Desktop\База зашифр файлов.txt"