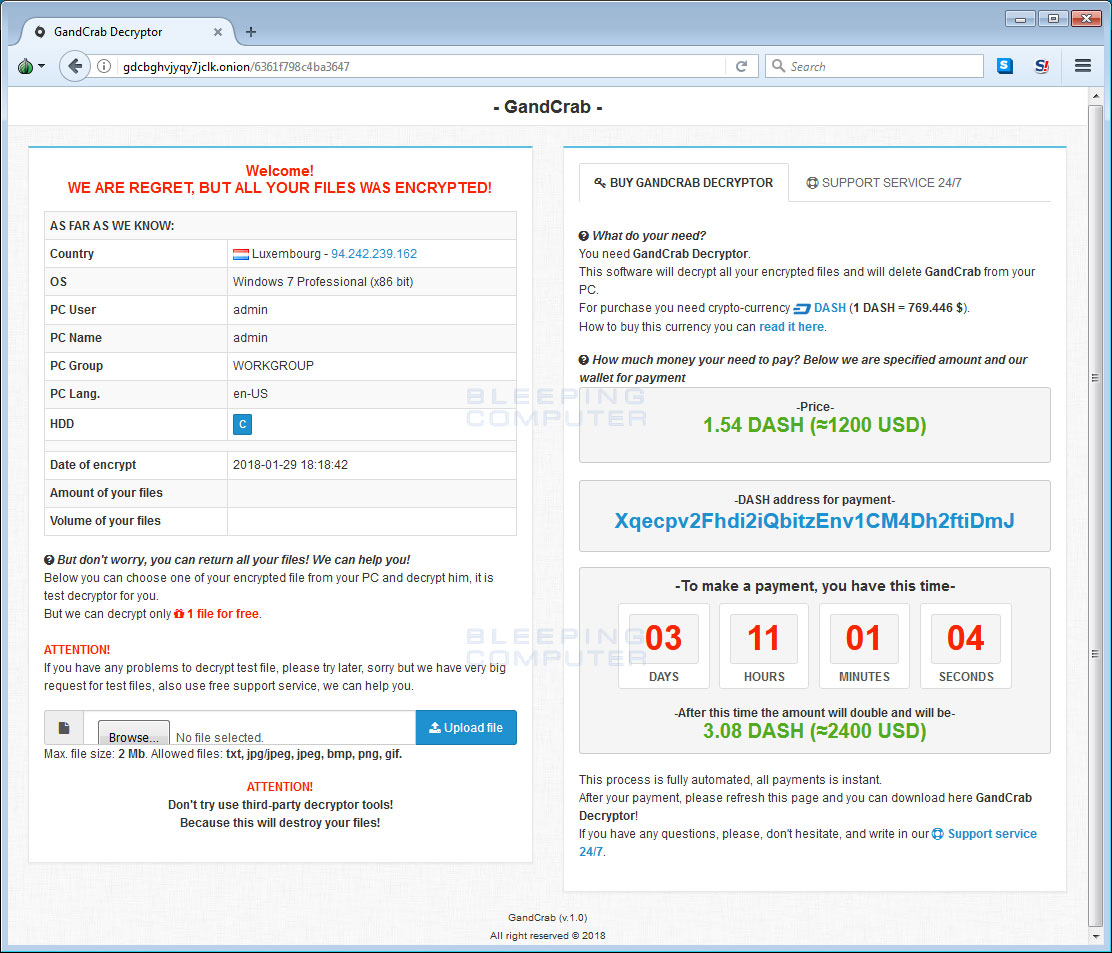
A new ransomware called GandCrab was released towards the end of last week that is currently being distributed via exploit kits. GandCrab has some interesting features not seen before in a ransomware, such as being the first to accept the DASH currency and the first to utilize the Namecoin powered .BIT tld.
First discovered by security researcher
David Montenegro, researchers quickly jumped in to analyze the ransomware and post their results on Twitter. This article will dive into what has been discovered by myself and other researchers.
Unfortunately, at this time there is no way to decrypt files encrypted by GandCrab for free. This ransomware is being researched, though, and if any new information is released we will be sure to update this article.
For now, if you wish to discuss GandCrab you can this article's comments section or our dedicated
GandCrab Help & Support Topic.
GandCrab being distributed through the Rig exploit kit
According to exploit kit researchers
nao_sec and
Brad Duncan, GandCrab is currently being distributed through a malvertising campaign called Seamless that then pushes the visitors to the RIG exploit kit. The exploit kit will then attempt to utilize vulnerabilities in the visitor's software to install GandCrab without their permission.
If the exploit kit is able to install the ransomware, the victim will probably not realize they are infected until it is too late.