- Jul 16, 2014
- 215
Get $1M for reporting zero-day flaws in Tor to “help Govt fight crime

Usually, a bug bounty program helps companies secure their software and products from zero day vulnerabilities that can cause massive damage if cyber criminals get their hands on them.
But Zerodium, an American information security company, and premium zero-day acquisition platform have launched a Tor Browser Zero-Day Bounty; the purpose of which is to get hackers and security researchers to find zero-day flaws in Tor browser on Tails Linux and Windows operating system and report it to the company.
In return, Zerodium will award a sum of $1 million to the successful participant. But will the company share those zero-day flaws with Tor? Well, apparently not as the company’s Tor Bounty page suggests that the sole purpose of launching the special bounty for Tor is to “help our government customers fight crime and make the world a better and safer place for all.”
“While Tor network and Tor Browser are fantastic projects that allow legitimate users to improve their privacy and security on the internet, the Tor network and browser are, in many cases, used by ugly people to conduct activities such as drug trafficking or child abuse,” states Zerodium.
The bounty program is open until November of this year but depending on the payout, the program may be terminated before the end date. Another important rule to keep in mind is that while JavaScript exploits are eligible for submission, a hacker with fully functional zero-day exploit without JavaScript will go home with more money.
Furthermore, the submission report research must rely on exclusive, unknown, unpublished, and unreported zero-days, and must bypass all exploit mitigations applicable to each target category. The initial attack vector must be a web page targeting the latest versions of Tor Browser while The whole exploitation process should be achieved silently, without triggering any message or popup, and without requiring any user interaction except visiting a web page.
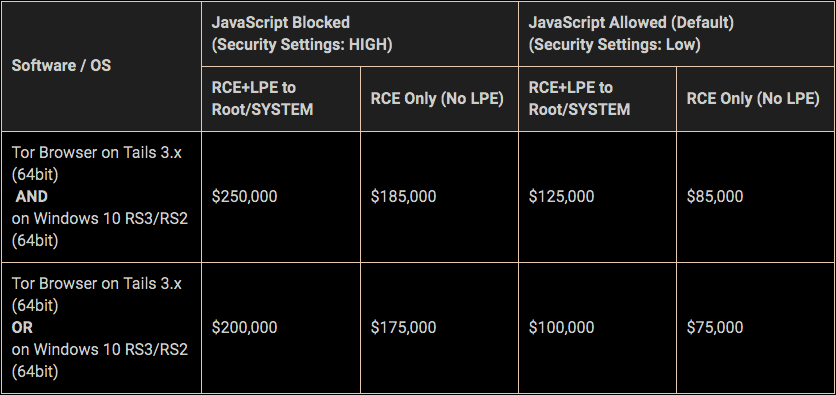
Payout details
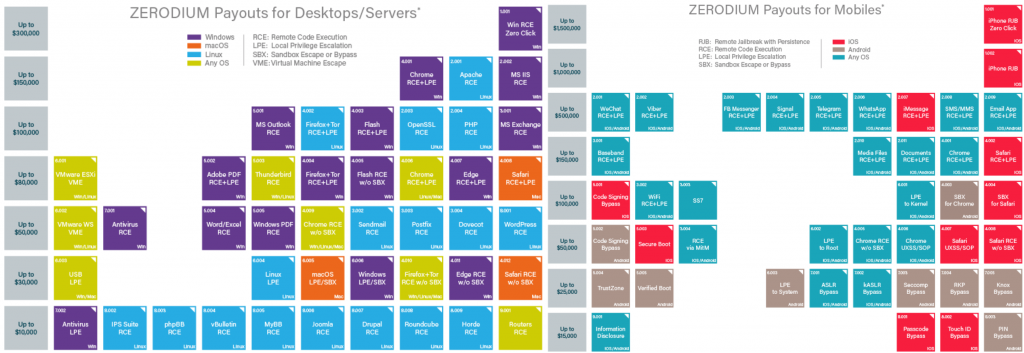
Zerodium has been facilitating bug bounty programs for the last few years. In August, the company launched a program to hack Messenger apps such as Telegram, WeChat, iMessage, WhatsApp, Signal and Facebook Messenger.
The company also invited hackers to find zero-day flaws in iPhone and remotely hack the device and receive $1,500,000 in return. Moreover, platforms like Windows 10, Chrome, Firefox, and WordPress, etc. are also in line for the hackers to try their skills.
However, since the company has suggested that these exploits will be shared with government it will be important to see the response from privacy advocates since Microsoft a couple of months ago slammed government agencies for not sharing vulnerabilities with manufacturers and piling up codes of software that can be easily stolen by hackers and exploited for their own unscrupulous gain.
Tor network itself launched its first public bug bounty program back in July this year. Understandably, the reward for which is only $4000 since it’s run by a group of volunteer-operated servers that allows people to improve their privacy and security on the Internet.
You can learn more about current and previous bug bounty programs by following this link.

Usually, a bug bounty program helps companies secure their software and products from zero day vulnerabilities that can cause massive damage if cyber criminals get their hands on them.
But Zerodium, an American information security company, and premium zero-day acquisition platform have launched a Tor Browser Zero-Day Bounty; the purpose of which is to get hackers and security researchers to find zero-day flaws in Tor browser on Tails Linux and Windows operating system and report it to the company.
In return, Zerodium will award a sum of $1 million to the successful participant. But will the company share those zero-day flaws with Tor? Well, apparently not as the company’s Tor Bounty page suggests that the sole purpose of launching the special bounty for Tor is to “help our government customers fight crime and make the world a better and safer place for all.”
“While Tor network and Tor Browser are fantastic projects that allow legitimate users to improve their privacy and security on the internet, the Tor network and browser are, in many cases, used by ugly people to conduct activities such as drug trafficking or child abuse,” states Zerodium.
The bounty program is open until November of this year but depending on the payout, the program may be terminated before the end date. Another important rule to keep in mind is that while JavaScript exploits are eligible for submission, a hacker with fully functional zero-day exploit without JavaScript will go home with more money.
Furthermore, the submission report research must rely on exclusive, unknown, unpublished, and unreported zero-days, and must bypass all exploit mitigations applicable to each target category. The initial attack vector must be a web page targeting the latest versions of Tor Browser while The whole exploitation process should be achieved silently, without triggering any message or popup, and without requiring any user interaction except visiting a web page.

Payout details
Zerodium has been facilitating bug bounty programs for the last few years. In August, the company launched a program to hack Messenger apps such as Telegram, WeChat, iMessage, WhatsApp, Signal and Facebook Messenger.
The company also invited hackers to find zero-day flaws in iPhone and remotely hack the device and receive $1,500,000 in return. Moreover, platforms like Windows 10, Chrome, Firefox, and WordPress, etc. are also in line for the hackers to try their skills.

However, since the company has suggested that these exploits will be shared with government it will be important to see the response from privacy advocates since Microsoft a couple of months ago slammed government agencies for not sharing vulnerabilities with manufacturers and piling up codes of software that can be easily stolen by hackers and exploited for their own unscrupulous gain.
Tor network itself launched its first public bug bounty program back in July this year. Understandably, the reward for which is only $4000 since it’s run by a group of volunteer-operated servers that allows people to improve their privacy and security on the Internet.
You can learn more about current and previous bug bounty programs by following this link.
