- Oct 23, 2012
- 12,527
A remote code execution (RCE) vulnerability is about as bad as it gets. And if it is in Windows, then a multitude of people are at risk until it is patched.
The question is, though, if the existence of a critical flaw is disclosed shortly before Patch Tuesday, will Microsoft scramble to immediately close that hole or will the company sit on it and wait out the 90-day disclosure deadline? We will find out tomorrow on Patch Tuesday if Microsoft took immediate action to close a “crazy bad” RCE flaw in Windows that was discovered by Google’s zero-day finders.
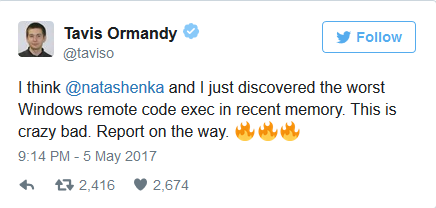
On the cusp of the weekend, Google Project Zero researcher Tavis Ormandy sent out an alarming tweet. He and fellow Project Zero researcher Natalie Silvanovich had discovered not just an RCE in Windows, but the “worst Windows remote code exec in recent memory.” He went so far as to call it “crazy bad.”
Naturally, security-minded people wanted more information—and not just if the discovery was about to ruin their weekend.
The question is, though, if the existence of a critical flaw is disclosed shortly before Patch Tuesday, will Microsoft scramble to immediately close that hole or will the company sit on it and wait out the 90-day disclosure deadline? We will find out tomorrow on Patch Tuesday if Microsoft took immediate action to close a “crazy bad” RCE flaw in Windows that was discovered by Google’s zero-day finders.
On the cusp of the weekend, Google Project Zero researcher Tavis Ormandy sent out an alarming tweet. He and fellow Project Zero researcher Natalie Silvanovich had discovered not just an RCE in Windows, but the “worst Windows remote code exec in recent memory.” He went so far as to call it “crazy bad.”
Naturally, security-minded people wanted more information—and not just if the discovery was about to ruin their weekend.
Although Ormandy didn’t give enough details that cyber thugs could start remotely exploiting the critical Windows flaw, he did reveal a few more alarming facts:
"Attack works against a default install, don't need to be on the same LAN, and it's wormable."
Project Zero gives vendors a 90-day heads-up about vulnerabilities. At the end of the 90-day disclosure deadline, details of the flaw are shared with the public whether or not the affected company issued a patch. Microsoft has been on the bad end of that before by failing to resolve issues before the deadline.
Ormandy’s tweets about the “crazy bad” RCE in Windows caused some criticism. For example, security researcher Alec Muffett suggested the critical flaw was “delivered in the manner of a WWF wrestling match.” Muffett claims not to be opposed to public disclosure, “but being a dick about it…is unhelpful.”
In response to various complaints and a fair bit of fear that Ormandy’s cryptic tweets about the vulnerability caused, Project Zero researcher Silvanovich—who helped discover the flaw—suggested that if such news if greeted with panic, then the panicking company is the one with the problem.
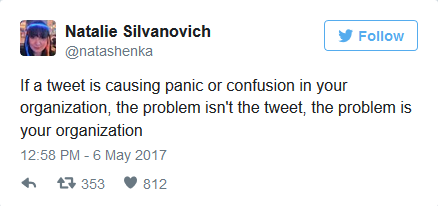
doesn’t even know what an OS is and would be clueless to comprehend Ormandy’s tweets. If technically literate folks comprehend the threat and are worried about his tweets, then she considers it a “positive” response. No matter what the public response is, she objects “to the idea that we shouldn’t talk about things because users might panic or come to the wrong conclusion.”
There are some people who undoubtedly cause executives to sweat, to panic, just by seeing their names in certain circumstances, such as Ormandy’s on a bug report or having caller ID show an incoming call from security journalist Brian Krebs. If there’s a vulnerability in a vendor’s product or if a company has been breached, we’re all better off when some light is shed on it than being kept in the dark when a company tries to hide the hack or hole.
Microsoft in the past did not have a great reputation among security researchers who quietly and confidentially reported bugs to the software giant and then had to wait and wait and wait for Microsoft to patch them. Seven years ago, after Microsoft was “hostile” to Ormandy and others, a group of security researchers formed the Microsoft-Spurned Researcher Collective to publicly disclose flaws in Windows.
Since then, Microsoft has made a lot of changes and is supposedly much more responsive. But Project Zero holds to its 90-day disclosure policy, and it will go public with vulnerability details if Microsoft fails to patch within the allotted time.