silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,746
- 123,926
- 8,399
The threat actors associated with the Gootkit malware have made "notable changes" to their toolset, adding new components and obfuscations to their infection chains.
Google-owned Mandiant is monitoring the activity cluster under the moniker UNC2565, noting that the usage of the malware is "exclusive to this group."
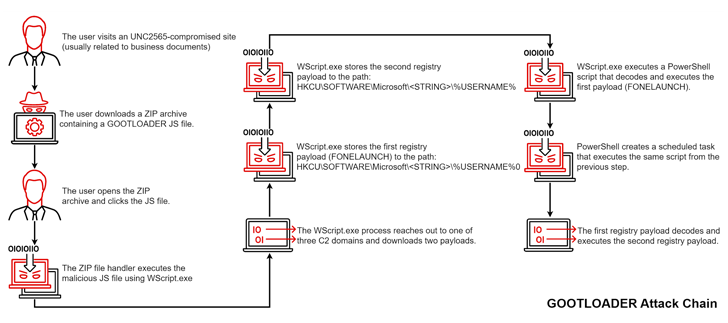
Gootkit, also called Gootloader, is spread through compromised websites that victims are tricked into visiting when searching for business-related documents like agreements and contracts via a technique called search engine optimization (SEO) poisoning.
The purported documents take the form of ZIP archives that harbor the JavaScript malware, which, when launched, paves the way for additional payloads such as Cobalt Strike Beacon, FONELAUNCH, and SNOWCONE.
FONELAUNCH is a .NET-based loader designed to load an encoded payload into memory, whereas SNOWCONE is a downloader that's tasked with retrieving next-stage payloads, typically IcedID, via HTTP.

Gootkit Malware Continues to Evolve with New Components and Obfuscations
Gootkit malware continues to evolve and become more sophisticated, with notable changes to the toolkit, adding new components and obfuscations.