- Oct 23, 2012
- 12,527
The H1N1 malware is slowly turning into an infostealer, according to reports from security experts at Cisco, Proofpoint, and independent researchers.
This old threat is what's known as a "malware downloader," a specific type of virus that is specialized in gaining a foothold on a victim's PC, with little features except the ability to bypass antivirus software, gain boot persistence, and download & install other more potent malware.
According to a report from Cisco this week, and one from Proofpoint released in May (citing researchers on KernelMode), recent H1N1 versions contain a lot more features, which in theory, should place H1N1 in the infostealer category.
New features make H1N1 an infeastealer, not just a dropper
Experts say that H1N1 now includes a shiny new UAC (User Access Control) bypass exploited via a novel DLL hijacking technique and unique code obfuscation techniques that make reverse engineering much harder.
The malware also comes with self-propagation features to spread to nearby computers on the same network (via network shares) or onto plugged in USB drives.
Most importantly, H1N1 now has the ability to collect information from infected systems and send it to a central C&C server encrypted using the RC4 algorithm.
This old threat is what's known as a "malware downloader," a specific type of virus that is specialized in gaining a foothold on a victim's PC, with little features except the ability to bypass antivirus software, gain boot persistence, and download & install other more potent malware.
According to a report from Cisco this week, and one from Proofpoint released in May (citing researchers on KernelMode), recent H1N1 versions contain a lot more features, which in theory, should place H1N1 in the infostealer category.
New features make H1N1 an infeastealer, not just a dropper
Experts say that H1N1 now includes a shiny new UAC (User Access Control) bypass exploited via a novel DLL hijacking technique and unique code obfuscation techniques that make reverse engineering much harder.
The malware also comes with self-propagation features to spread to nearby computers on the same network (via network shares) or onto plugged in USB drives.
Most importantly, H1N1 now has the ability to collect information from infected systems and send it to a central C&C server encrypted using the RC4 algorithm.
H1N1 can collect and steal information such as Firefox profile login data, Internet Explorer Intelliform data, and email login data from Microsoft Outlook. It's not as much information as other infostealers can target, but this is most likely to expand in future versions.
Furthermore, researchers also detected that H1N1 also deletes shadow copies and disables of system recovery options. "These commands are commonly used in conjunction with Ransomware, but we have not found evidence that H1N1 has been loading such types of malware," Cisco's Josh Reynolds explains.
New spam flood spreads H1N1
H1N1 has been historically seen in campaigns that spread the Pony infostealer or the Vawtrack banking trojan, but recent campaigns are dropping H1N1 and nothing else. The malware dropper functionality is still there, and attackers could deploy it if necessary in the future.
Cisco experts say they've detected a recent spam flood that spreads this new H1N1 version.
Crooks are distributing emails that have a malicious DOC file attached. The file uses the classic "Enable Editing" macro activation trick to run an embedded VBA script that downloads and installs H1N1.
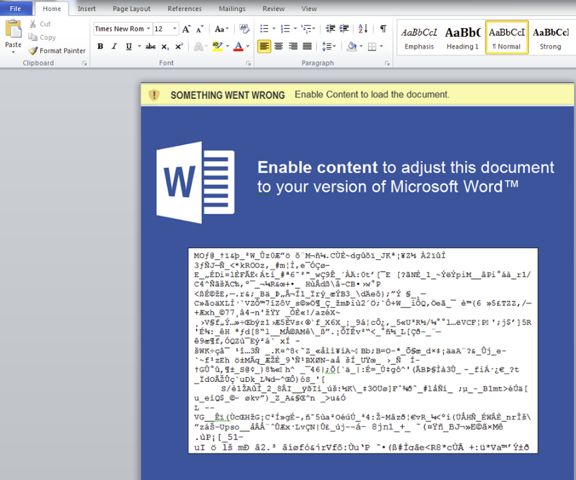
One of the malicious documents spreading H1N1
The campaign currently targets organizations in the financial, energy, communications, military and government sectors, with different email subjects and lures employed.
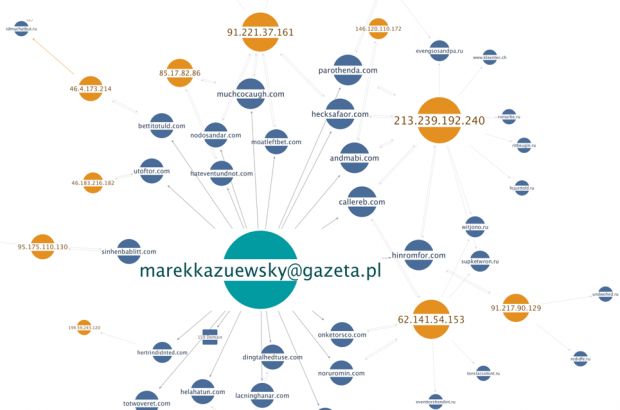
Leveraging data provided by OpenDNS, Cisco researchers were able to discover that a crook/group using the marekkazuewsky@gazeta.pl had registered 177 domains, which he used to send the spam flood that spread these new H1N1 versions.
H1N1 deployed by a group with experience in malware distribution
Taking into account data on other malware campaigns, the researchers linked these domains and the group behind them to several other malware operations that also spread the Bayrob backdoor trojan, the Rovnix banking trojan, a variant of the Zeus banking trojan, the Sality (botnet) trojan, the Virut (botnet) trojan, and some generic ransomware versions.
Coincidentally, the Bayrob backdoor trojan also received a recent update after nine years. This happened in May, around the same time Proofpoint started to detect the first revamped versions of H1N1.
"H1N1 is an example of the many dropper variants that continue to evolve over time, and become threats to your organization in and of themselves, as opposed to the sophisticated variants they are meant to drop," Cisco's Emmett Koen says.
"The amount of obfuscation within this binary demonstrates the length at which malware authors are prepared to protect their original code, and even with this amount of complexity there are still a large number of variants that present much larger challenges for analysts," the expert also added.