Attackers spreading HC7 Ransomware in network using PsExec
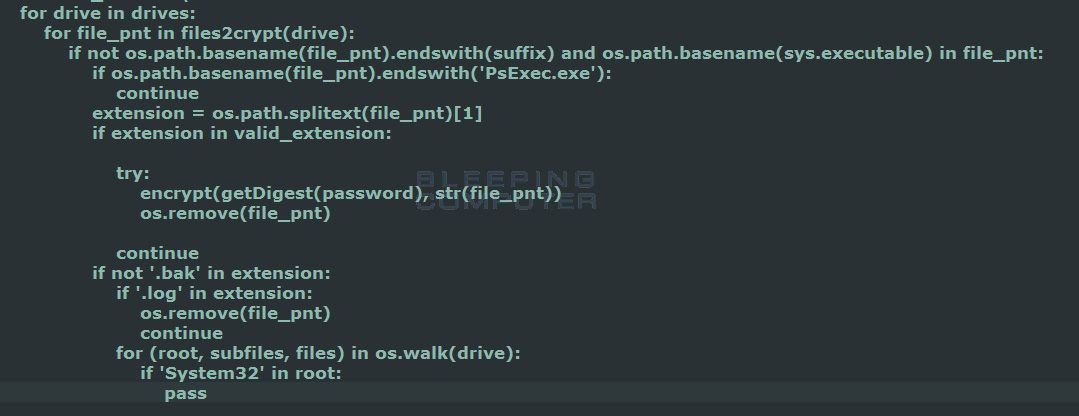
Currently the attackers are hacking into exposed remote desktop services, and once inside, use PsExec to install the ransomware on other computers in the network. The use of PsExec is evident in the source code below, which specifically looks for the PsExec.exe and skips it from being encrypted.
Finding Files to Encrypt Source Code
As previously stated, when the attacker executes the ransomware they will provide the encryption key as a command line argument. This key is then used to encrypt files that match the following extensions with AES-256 encryption.
.001, .3fr, .3gp, .7z, .ARC, .DOT, .MYD, .MYI, .NEF, .PAQ, .SQLITE3, .SQLITEDB, .accdb, .aes, .ai, .apk, .arch00, .arw, .asc, .asf, .asm, .asp, .asset, .avi, .bar, .bay, .bc6, .bc7, .big, .bik, .biz, .bkf, .bkp, .blob, .bmp, .brd, .bsa, .cas, .cdr, .cer, .cfr, .cgm, .class, .cmd, .cpp, .cr2, .crt, .crw, .csr, .css, .csv, .d3dbsp, .das, .dazip, .db0, .dbf, .dbfv, .dch, .dcr, .der, .desc, .dif, .dip, .djv, .djvu, .dmp, .dng, .doc, .docb, .docm, .docx, .dotm, .dotx, .dwg, .dxg, .epk, .eps, .erf, .esm, .exe, .ff, .fla, .flv, .forge, .fos, .fpk, .frm, .fsh, .gdb, .gho, .gpg, .hkdb, .hkx, .hplg, .htm, .html, .hvpl, .hwp, .ibank, .ibd, .icxs, .indd, .itdb, .itl, .itm, .iwd, .iwi, .jar, .java, .jpeg, .jpg, .js, .kdb, .kdc, .key, .kf, .lay, .lay6, .layout, .lbf, .ldf, .litemod, .log, .lrf, .ltx, .lvl, .m2, .m3u, .m4a, .map, .max, .mcgame, .mcmeta, .mdb, .mdbackup, .mddata, .mdf, .mef, .menu, .mid, .mkv, .mlx, .mml, .mov, .mp3, .mpeg, .mpg, .mpqge, .mrwref, .ms11 (Security copy), .ncf, .nrw, .ntl, .ocx, .odb, .odc, .odm, .odp, .ods, .odt, .orf, .otg, .ots, .ott, .p12, .p7b, .p7c, .pak, .pas, .pdd, .pdf, .pef, .pem, .pfx, .php, .pkpass, .pl, .png, .ppam, .ppsm, .ppsx, .ppt, .pptm, .pptx, .psd, .psk, .pst, .ptx, .py, .qcow2, .qdf, .qic, .r3d, .raf, .rar, .raw, .rb, .re4, .rgss3a, .rim, .rofl, .rtf, .rw2, .rwl, .sav, .sb, .sc2save, .sch, .sid, .sidd, .sidn, .sie, .sis, .sldm, .sldx, .slk, .slm, .snx, .sql, .sr2, .srf, .srt, .srw, .stc, .stw, .sum, .svg, .swf, .sxc, .sxm, .sxw, .syncdb, .t12, .t13, .tar, .tar.bz2, .tar.gz, .tax, .tbk, .tgz, .tif, .tiff, .tor, .txt, .unity3d, .uot, .upk, .upx, .vbs, .vdf, .vdi, .vfs0, .vmdk, .vmx, .vob, .vpk, .vpp_pc, .vtf, .w3x, .wav, .wb2, .wma, .wmo, .wmv, .wotreplay, .wpd, .wps, .x3f, .xf, .xlc, .xlk, .xlm, .xls, .xlsb, .xlsm, .xlsx, .xlt, .xlw, .xml, .xxx, .zip, .ztmp, wallet.dat
When the ransomware encrypts a file it will append the
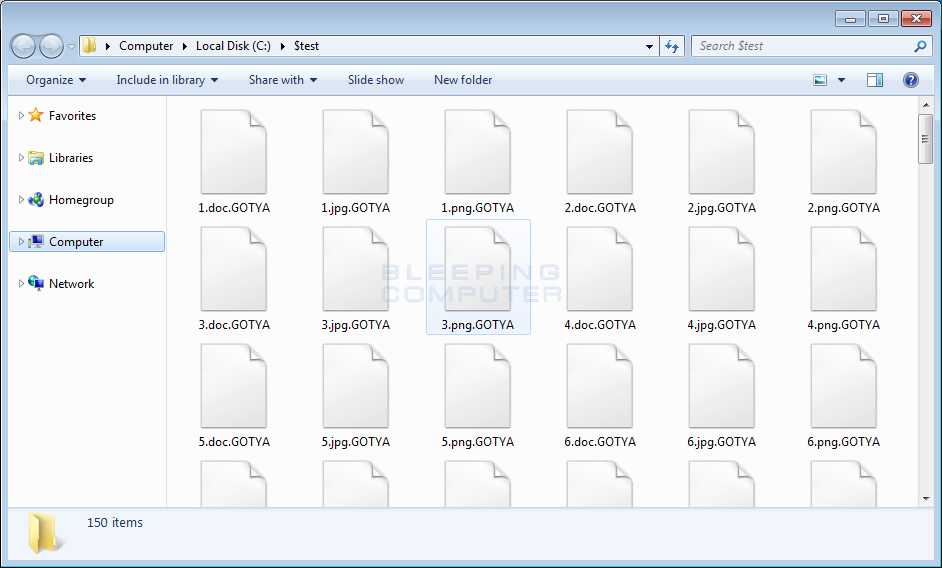
.GOTYA extension on the encrypted file's name. For example, the file test.jpg would be encrypted and renamed to test.jpg.GOTYA.
Encrypted Folder of Encrypted GOTYA Files
While encrypting a computer, the ransomware will create a ransom note named
RECOVERY.txt in each folder that a file was encrypted. This ransom note will contain a bitcoin address, a victim ID, payment instructions, and an email address that the victim can use to contact the ransomware developer. This email address is
m4zn0v@keemail.me. Currently, the ransom demands are $700 in BTC for one machine or $5,000 in BTC for all the infected computers on the network.