Two Belgian security researchers have presented their latest work at the Black Hat security conference in Las Vegas: a new Web-based attack that can steal encrypted content from HTTPS traffic using nothing more than JavaScript.
Their attack is called HEIST, which stands for HTTP Encrypted Information can be Stolen through TCP-Windows.
The attack relies on a malicious entity embedding special JavaScript code on a Web page. This can be done right on the website if the attacker owns the site, or via JS-based ads if the attacker needs to embed the attack vector on third-party sites.
The most deadly attack scenario is the latter, when the attacker sneakily embeds malicious JS inside an ad, which is shown on your banking portal or social media accounts.
HEIST is another side-channel attack on HTTPS
At its core, the JavaScript code performs two main functions. The first is to try and fetch content via a hidden JavaScript call from a private page that holds sensitive information such as credit card numbers, real names, phone numbers, SSNs, etc.. This page is protected in most cases by HTTPS.
Secondly, as the content is retrieved, using a repeated probing mechanism of JavaScript calls, the attacker pinpoints the size of the data embedded on the sensitive page.
HEIST basically brute-forces the size of small portions of data that get added to a page as it loads. As such, the attack can take a while. If the page is loaded using the next-gen version of HTTP, the HTTP/2 protocol, the time needed to carry out the attack is much shorter because HTTP/2 supports native parallel requests.
At its core, HEIST is another side-channel attack on HTTPS, one that doesn't break SSL encryption but leaks enough information about the data exchanged in HTTPS traffic to guess its content. As data is transferred in small TCP packets, by guessing the size of these packets, an attacker can infer their content.
HEIST is CRIME or BREACH attacks embedded in JavaScript
"Combined with the fact that SSL/TLS lacks length-hiding capabilities, HEIST can directly infer the length of the plaintext message," the researchers explain. "Concretely, this means that compression-based attacks such as CRIME and BREACH can now be performed purely in the browser, by any malicious website or script, without requiring a man-in-the-middle position."
According to the researchers, the simplest way to block HEIST attacks is by disabling support for either third-party cookies or JavaScript execution in your browser. At this point in time, and judging by how the Internet has evolved, disabling JavaScript is not a solution.
Below is a breakdown of the complicated attack routine. More details are available in Tom Van Goethem and Mathy Vanhoef's research paper.
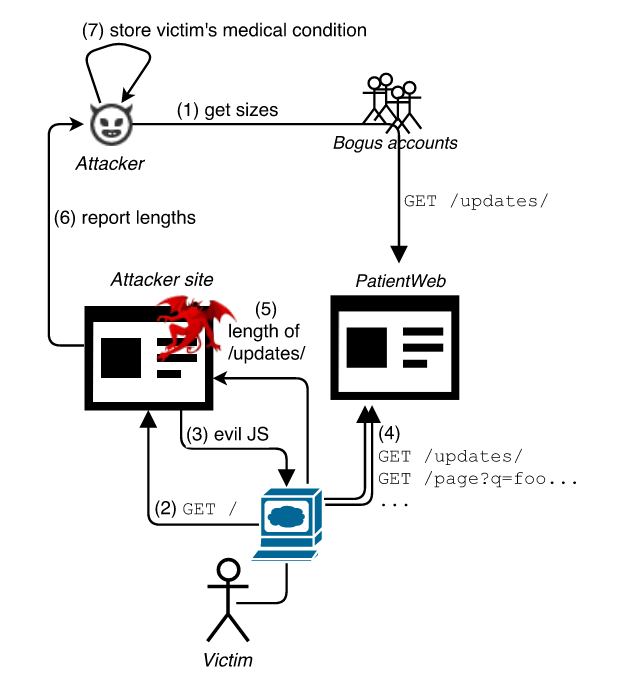
Their attack is called HEIST, which stands for HTTP Encrypted Information can be Stolen through TCP-Windows.
The attack relies on a malicious entity embedding special JavaScript code on a Web page. This can be done right on the website if the attacker owns the site, or via JS-based ads if the attacker needs to embed the attack vector on third-party sites.
The most deadly attack scenario is the latter, when the attacker sneakily embeds malicious JS inside an ad, which is shown on your banking portal or social media accounts.
HEIST is another side-channel attack on HTTPS
At its core, the JavaScript code performs two main functions. The first is to try and fetch content via a hidden JavaScript call from a private page that holds sensitive information such as credit card numbers, real names, phone numbers, SSNs, etc.. This page is protected in most cases by HTTPS.
Secondly, as the content is retrieved, using a repeated probing mechanism of JavaScript calls, the attacker pinpoints the size of the data embedded on the sensitive page.
HEIST basically brute-forces the size of small portions of data that get added to a page as it loads. As such, the attack can take a while. If the page is loaded using the next-gen version of HTTP, the HTTP/2 protocol, the time needed to carry out the attack is much shorter because HTTP/2 supports native parallel requests.
At its core, HEIST is another side-channel attack on HTTPS, one that doesn't break SSL encryption but leaks enough information about the data exchanged in HTTPS traffic to guess its content. As data is transferred in small TCP packets, by guessing the size of these packets, an attacker can infer their content.
HEIST is CRIME or BREACH attacks embedded in JavaScript
"Combined with the fact that SSL/TLS lacks length-hiding capabilities, HEIST can directly infer the length of the plaintext message," the researchers explain. "Concretely, this means that compression-based attacks such as CRIME and BREACH can now be performed purely in the browser, by any malicious website or script, without requiring a man-in-the-middle position."
According to the researchers, the simplest way to block HEIST attacks is by disabling support for either third-party cookies or JavaScript execution in your browser. At this point in time, and judging by how the Internet has evolved, disabling JavaScript is not a solution.
Below is a breakdown of the complicated attack routine. More details are available in Tom Van Goethem and Mathy Vanhoef's research paper.
