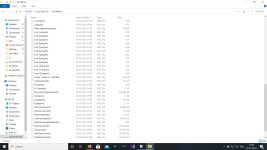
Hi this is Deepu, my laptop is attacked by DJVU ransomware, .ehiz file extension, can someone help me
- Thread starter Deepu
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
- Apr 9, 2020
- 667
Hello Deepu
I am Karsten and will gladly help you with any malware-related problems.
Please familiarize yourself with the following ground rules before you start.
Your system has been infected by STOP/DJVU ransomware. STOP/DJVU ransomware variants after August 2019 are only decryptable if an offline key was used. For variants with an online key you cannot decrypt files.
Please try this decrypter by Emsisoft: Emsisoft Decryptor for STOP Djvu
It will only work for STOP ransomware with an offline key, though.
I am Karsten and will gladly help you with any malware-related problems.
Please familiarize yourself with the following ground rules before you start.
- Read my instructions thoroughly, carry out each step in the given order.
- Do not make any changes to your system, or run any tools other than those I provided. Do not delete, fix, uninstall, or install anything unless I tell you to.
- If you are unsure about anything or if you encounter any problems, please stop and inform me about it.
- Stick with me until I tell you that your computer is clean. Absence of symptoms does not mean that your computer is free of malware.
- Back up important files before we start.
- Note: On weekends I might be slow to reply
Your system has been infected by STOP/DJVU ransomware. STOP/DJVU ransomware variants after August 2019 are only decryptable if an offline key was used. For variants with an online key you cannot decrypt files.
Please try this decrypter by Emsisoft: Emsisoft Decryptor for STOP Djvu
It will only work for STOP ransomware with an offline key, though.
- Apr 9, 2020
- 667
That means your variant is not decryptable.
Your options without a backup:
1) Recovery: In rare cases ransomware fails to delete shadow volume copies or fails to delete the original files properly. You can try to recover files via shadow volume copies and file recovery software.
2) Repair: Certain file types, mainly video and audio files, can possibly be repaired with tools like MediaRepair. But these files will loose some data.
3) Wait: Backup encrypted files and a ransom note and wait in case a solution comes up later. Maybe law enforcement gets hands on the keys or the criminals publish the keys as it happened with, e.g., GandCrab. I suggest reading the news on this. Emsisoft will update their decrypter if that happens.
4) Pay: There is the option of paying the criminals, but we highly recommend against this step. You will just fund later attacks. You may also pay without getting your files back. These are criminals and as such not trustworthy.
Please let me know if you need help for the steps 1) or 2)
Your options without a backup:
1) Recovery: In rare cases ransomware fails to delete shadow volume copies or fails to delete the original files properly. You can try to recover files via shadow volume copies and file recovery software.
2) Repair: Certain file types, mainly video and audio files, can possibly be repaired with tools like MediaRepair. But these files will loose some data.
3) Wait: Backup encrypted files and a ransom note and wait in case a solution comes up later. Maybe law enforcement gets hands on the keys or the criminals publish the keys as it happened with, e.g., GandCrab. I suggest reading the news on this. Emsisoft will update their decrypter if that happens.
4) Pay: There is the option of paying the criminals, but we highly recommend against this step. You will just fund later attacks. You may also pay without getting your files back. These are criminals and as such not trustworthy.
Please let me know if you need help for the steps 1) or 2)
- Apr 9, 2020
- 667
1. Shadow Explorer
- Make sure the correct drive letter is selected (usually "C:" )
- There is a date on the upper bar. Check if there is a date available that was before the ransomware attack. If the date isn't available, you don't have any shadow volume copies from before and recovery is not possible.
- Within Shadow Explorer, navigate to files or folders you want to recover
- To recover: Right-click and click Export... then choose a folder to save the files to and click OK
- Apr 9, 2020
- 667
That means you have no shadow volume copies. Ransomware often deletes them. You cannot recover with Shadow Explorer in this case.
If you haven't tried already, see if you have success with any of the following:
1. File Recovery Software
If you had any external drives encrypted, you may try the same on them.
2. File Repair
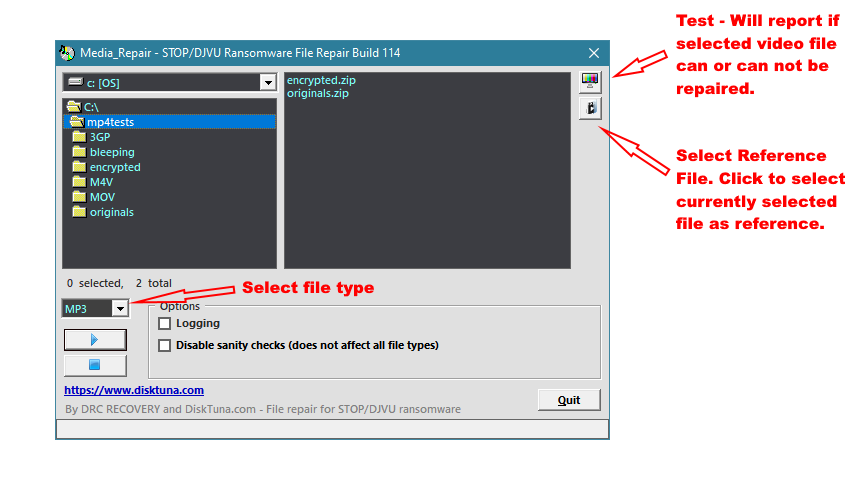
The tool can repair 6 file types: MP3, WAV, MP4, MOV, M4V, 3GP
If you have such files encrypted by STOP ransomware, download and run MediaRepair.
For most file types, you need a reference file, that is a non-encrypted file of the same file format as the encrypted ones. Video files will need this reference file. File types like MP3 do not need one.
If you haven't tried already, see if you have success with any of the following:
1. File Recovery Software
- Please download PhotoRec, choose Windows 64-bit from that list.
- Right-click on the testdisk-7.1.win64.zip archive and click Extract all.
- Now navigate into the extracted folder and run qphotorec_win.exe
- Select your Hard Disk from the list.
- Make sure that FAT/NTFS/HFS+/ReiserFS is selected
- Choose a destination for your recovered files by clicking on the "Browse" button
- Now click "Search" and the tool will start recovering. Wait for it to finish, then click Quit
If you had any external drives encrypted, you may try the same on them.
2. File Repair
The tool can repair 6 file types: MP3, WAV, MP4, MOV, M4V, 3GP
If you have such files encrypted by STOP ransomware, download and run MediaRepair.
For most file types, you need a reference file, that is a non-encrypted file of the same file format as the encrypted ones. Video files will need this reference file. File types like MP3 do not need one.
- Run MediaRepair.
- Select a file type
- Navigate to the folder with your encrypted files.
- Now select one of your encrypted files and click on the Test
button to check if the file can be repaired (see image below to find the button)

- Note: If the program tells you at this point that it cannot repair these files, abort and continue with another file type.
- Now select a reference file that is not encrypted and has the same file type and click on the Select Reference
button (see image below).
- Note: If you have several reference files, prefer the smallest.
- Select the encrypted files you want to repair and click on the Play
button (below the file types) to start repair.

- Now wait for the program to finish.
- Navigate to your encryped files, you should find a folder named FIXED in there. This folder contains your repaired files.

- Apr 9, 2020
- 667
- Status
- Not open for further replies.
Similar threads
- Locked
Waiting for reply
A variant of DJVU (.nood) says online forum, please help.
- Replies
- 1
- Views
- 662
- Replies
- 2
- Views
- 1,047