- Mar 16, 2019
- 4,060
- Content source
- https://blog.es3n1n.eu/posts/how-i-ruined-my-vacation/
Full blog post:In this post I will briefly describe the journey I went through while implementing defendnot.
Even though this is most likely not what you expected to see here, but rather than going into full technical details on how everything works, I will describe what rabbitholes I went through and how painful everything was due to myspecial
environment.
Beware, most likely this post will be too informal unlike the previous posts of mine, pretty sure all the other posts with irl tag will be written in a style like this. If you are looking for a more detailed technical description of how everything works, a writeup like this will be released a bit later by someone else and I will link it here.
A one-year step back
Almost exactly one year ago I released a tool no-defender, a project that was disabling windows defender using the special windows api made for antiviruses to let the system know that there is an another antivirus so there is no need to run defender scans.
The part of the system that manages all this mess is called Windows Security Center - WSC for short. The way how it worked is that it was using a thirdparty code from some already existing antivirus and forced it to register the antivirus without having anything else installed.
Then after a few weeks after the release, the project blew up quite a bit and gained ~1.5k stars, after that the developers of the antivirus I was using filled a DMCA takedown request and I didn’t really want to do anything with that so just erased everything and called a day.
How it started
Currently, even while writing this article, I am sitting in an airbnb we rented in Seoul. After numerous trips to other parts of the planet for CTFs and stuff, me and a friend of mine decided that we want to visit Seoul and arrived a few months after that.
My current main machine for non-ctf things is an M4Pro MacBook and usually, when I am going for a CTF I bring an another x86 laptop with me to do some extensive reverse engineering/pwn stuff as it is usually built for the x86 cpus, emulation would kind of work for this task but it is pretty painful so I just use an another laptop for all the x86 stuff.
And, as you might have guessed, for this trip I did not bring that x86 laptop with me, but I did bring my macbook with me to do some other development stuff in my free-free time.
And, on May 4th, after a few days spent in South Korea meeting my favorite South Korean CTF friends and drinking alcohol with them, I received a message from MrBruh where they said that they were looking at no-defender and were looking into whether it would be possible to create a “clean” implementation of my project without using any AVs.
Initial research (Day 1)
I am having some troubles with my sleep schedule and I woke up a bit earlier than my friends so I decided to take a look at this while I am waiting for my friends to wake up.
MrBruh provided me the latest binaries of wsc because I was too lazy to spin up my parallels vm to get the binaries and I started looking into what we got.
As a reference implementation, I took the WSC registration implementation made by the same AV I was using a year ago. I was somewhat familiar with the internals of their thing and it was a great call.
Essentially, WSC has a COM API that all antiviruses are using, so I quickly rebuilt everything that AV was doing with it in ~1hr, booted an arm64 windows in parallels and tested the thing. I was greeted with an access denied error.
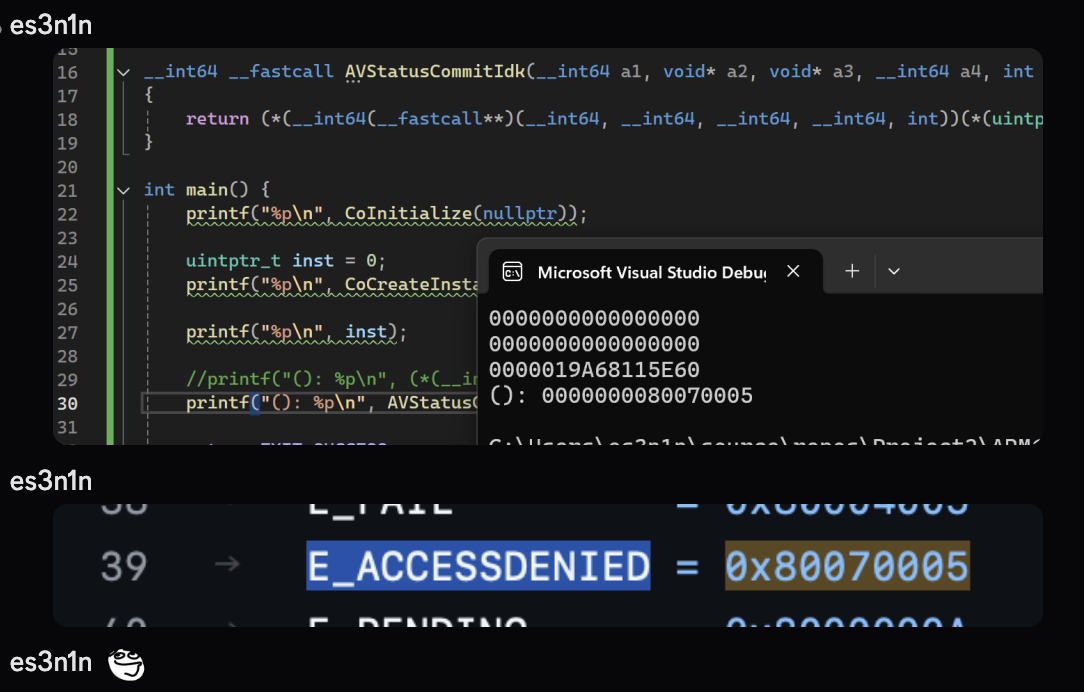
But from my last year’s courtesy I knew that WSC was
somehow validating the process that calls these APIs, my guess was that they are validating the signatures, which was indeed a correct guess but I didn’t know that for sure at that time. My move then was to...........................................
How I ruined my vacation by reverse engineering WSC
In this post I will briefly describe the journey I went through while implementing defendnot. Even though this is most likely not what you expected to see here, but rather than going into full technical details on how everything works, I will describe what rabbitholes I went through and how...

