10 Leading 'Cybercrime-as-a-Service' Offerings, From $5

RDP credential pricing - overlaid on the most frequent origin of such credentials - on the UAS darknet market. (Source: Flashpoint)
How much does it cost to buy into cybercrime? Just $5 and up, security researchers say.
See Also: Ransomware: The Look at Future Trends
One measure of the challenge of stopping online attacks is the affordability and sheer volume of products and services available to anyone who wants to steal money from victims using online means. This cybercrime-as-a-service economy offers even unskilled attackers the chance to become a profit-generating cybercriminal (see Financial Sector Under Increasing Cybercrime Threat).
"Crime as a service is one of the most worrying developments in recent years," Alan Woodward, a computer science professor and cybercrime expert, says via Twitter. "It's getting very ugly."
Today's "professional underground service economy" is being tapped not just by low-level hackers but also "serious and organized crime" rings, says Rob Wainwright, executive director of Europol, the EU's law enforcement intelligence agency, in the forward to Europol's most recent Internet Organized Crime Threat Assessment.
Darknet marketplaces are providing criminals with "access to, amongst other things, compromised financial data to commit various types of payment fraud, firearms, counterfeit documents to facilitate fraud, trafficking in human beings and illegal immigration," Europol's report says. "Compared to more established darknet market commodities, such as drugs, the availability of cybercrime tools and services on the darknet appears to be growing more rapidly."
Top Marketplaces
It's a buyer's market for cybercrime services. Two of the leading marketplaces for stolen remote desktop protocol credentials are UAS - for "Ultimate Anonymity Services" - that's been around for two years, as well as xDedic, a Russian language forum started in 2014 now reachable only by using the Tor anonymizing browser, according to New York-based threat intelligence firm Flashpoint.
RDP credentials give attackers a way to gain remote access to a corporate environment, after which they might move laterally across a network in search of intellectual property or cryptolock systems and demand a ransom (see Hackers Exploit Weak Remote Desktop Protocol Credentials).
"We don't know sales volume, but what we did look into, particularly for RDP credentials for sale, was cybercrime chatter in our data set to see which of those two shops they were talking about more," Liv Rowley, an intelligence analyst at Flashpoint, tells Information Security Media Group. "And we found that chatter about xDedic, which is the more expensive one, was declining, whereas chatter about UAS was going up."
Variable Pricing
Pricing of goods and services can vary widely across forums. On UAS, the cost of an RDP credential ranged from $3 to $15.
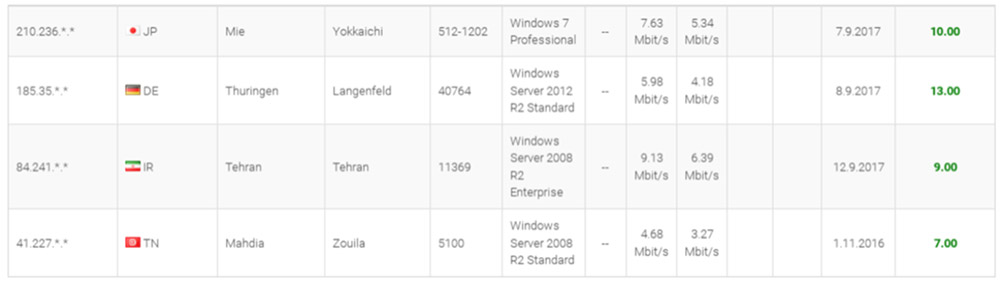
RDP credentials for sale on UAP (prices shown in far-right column) cost on average $10 each. (Source: Flashpoint)
But for reasons that are unclear, Flashpoint's Rowley says, xDedic is much more expensive: $10 was the minimum price for a stolen RDP credential and some sold for up to $100.
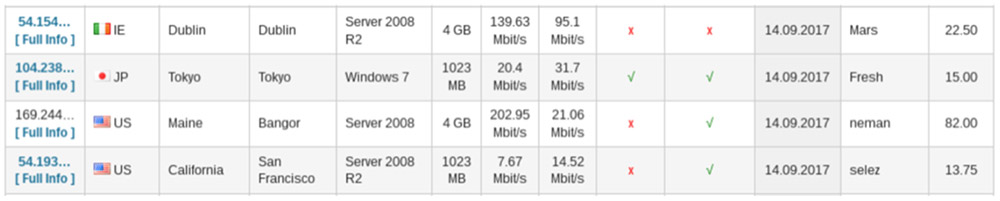
RDP credentials for sale on xDedic are much more expensive (prices shown in far-right column) than on UAS. (Source: Flashpoint)
In a potential clue as to who's running UAS, available in both English and Russian, the site doesn't offer any RDP credentials for organizations from the "Commonwealth of Independent States," which was formed when the former Soviet Union dissolved in 1991.
Selected Crime Services For Sale
Regardless of who's running any given underground forum, there are some common offerings, including firearms, illegal narcotics and myraid cybercrime products and services. Here's a selection of the latter:
1. Bank Accounts
Hacked bank accounts get sold on underground forums at a price that relates to an account's available balance, Rowley says. "Compromised bank accounts are priced as a percentage of how much is in the account," she says. "So you may have a bank account containing $1,000 that gets offered for $90, and another with $25,000 in the account and is being offered for $390." She says the majority of stolen bank accounts are located in the United States, Britain, Australia as well as Western Europe.
2. Banking Trojans
"A banking Trojan license is one of the most expensive elements of a cybercriminal campaign and can be obtained from professional malware developers for $3,000 to $5,000," Andrei Barysevich, a researcher at Boston-based threat intelligence firm Recorded Future, says in a blog post (see Understanding the Malware-as-a-Service Commodity Market).
The Trojan must then be customized with web injections designed to target customers of specific banks. Injecting HTML into web pages allows attackers to make it look to a user like they're normally browsing a site, when in reality an attacker might be transferring all of their savings to another bank (see Zeus Banking Trojan Spawn: Alive and Kicking).
A set of web injection credentials designed to target a specific financial institution costs anywhere from $150 to $1,000, according to Recorded Future. "In the past year, we've seen a significant increase in the cost of web-injects targeting Canadian institutions, offered at the upper-level of the price spectrum, while the cost of malware targeting U.S.-based banks has remained the same," Barysevich says.
3. Bulletproof Hosting
So-called bulletproof hosting services offer servers with high uptime and availability while promising to ask few if any questions about how the servers are being used. They can be used to handle exfiltrated data - online account and bank credentials, for example - from malware-infected PCs. Recorded Future says the majority of such services get procured from hosts in China, the Middle East or Eastern Europe and cost about $150 to $200 monthly.
4. Counterfeit Passports and Identity Documents
Underground forums sell illicit U.S. passports - and other types of identity documents - in three forms, Rowley says: digital scans, templates as well as physical versions of the travel documents. Whether such documents would hold up to police or customs agents' scrutiny, however, remains to be tested. But the documents are often procured to help with money laundering efforts, experts say.
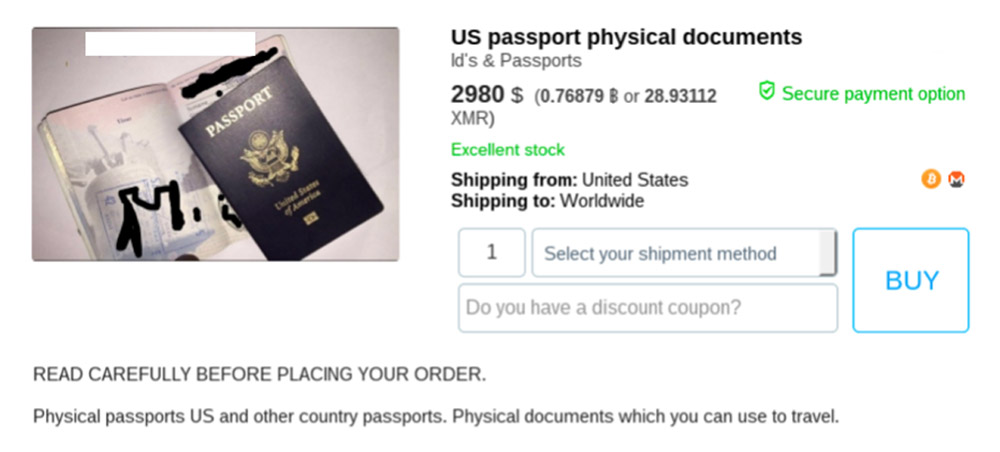
One darknet forum advertises physical U.S. passports for $2,980. (Source: Flashpoint)
5. Exploit Kits
These automated attack toolkits allow even poorly skilled criminals to deliver malware - including ransomware and banking Trojans - onto endpoints. The vast majority are rented on demand, rather than sold outright, according to Flashpoint, which says rental fees typically run from $80 to $100 per day, $500 to $700 per week and $1,400 to $2,000 per month (see Rent the Latest Exploit Toolkit for $80 Per Day).
6. Fullz
Fraudsters can use these complete sets of personally identifiable information - PII - for phishing, identity theft and other attacks. Increasingly, this information is being sold based on an individual's creditworthiness, Rowley says. "When looking at the pricing of fullz, we found that oftentimes, cybercriminals will organize their fullz by credit scores, which means they've compromised that information or more likely they're taking that information and pulling credit reports on everyone they've compromised, and then they've organized it by credit rating," she says.
7. Money Mules
Converting stolen bank account credentials into cash requires multiple steps, Barysevich says, typically including using money mules to withdraw cash or receive cash transfers (see Don't Be a Money Mule for the Holidays).
"The perpetrator has to work with a chain of mule handlers and money-laundering intermediaries to receive a final pay-off," he says. "A money launderer with a stellar reputation and capable of quick turnaround will charge a hefty 50 to 60 percent commission from each payment transferred from a victim's account. In some cases, an additional 5 to 10 percent commission might be required to launder the funds and deliver it to the main operator via preferred payment method, such as bitcoin, Web Money or Western Union."
Money transfers may also require confirmation, which can be provided by an underground calling service - cost: $10 to $15 per call - although additional documentation may be required, Barysevich says. This, too, can be provided by crime-as-a-service providers. "A counterfeit driver's license may be delivered within several hours for $25, while a more sophisticated video selfie will cost $100," he says.
8. Payment Card Data
Many underground shops sell "cards" - aka "dumps" - that are "often sourced directly from malware-infected or skimmed point-of-sale terminals," Rowley says. This information can then be illicitly converted into cash using money mules and money transfer services.
9. RDP Servers
Mentioned above, servers running remote desktop protocol for which the credentials have been guessed or cracked provide an easy entry point into enterprise networks. Beyond the initial intrusion to verify that harvested RDP credentials work, these credentials may be sold to other buyers to ransack networks for intellectual property before finishing with a crypto-locking ransom attack, among other possibilities.
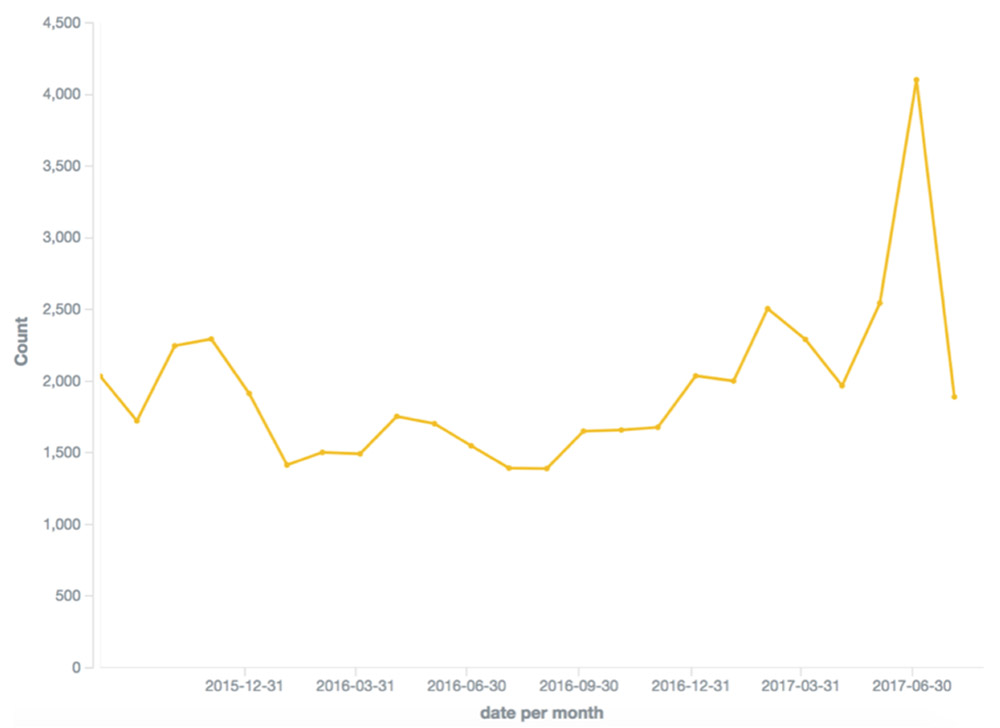
Mentions of "RDP" observed by Flashpoint in the first half of last year peaked in July 2017. (Source: Flashpoint)
10. Stresser/Booter Services
On-demand DDoS services enable criminals to disrupt websites of their choosing. "An attack on a regular website is typically just $10 per hour, whereas an attack on a website that employs basic protections against DDoS attacks is typically $25 per hour," Rowley says. "The most expensive DDoS-for-hire services are for attacks geared toward government, military or bank websites, ranging from $100 to $150 per hour." (See Teen Hacker Avoids Jail Over On-Demand DDoS Attacks)
Closing the Deal
Flashpoint's review of cybercrime chatter found that last year's law enforcement takedowns of the AlphaBay and Hansa darknet marketplaces have left many buyers and sellers spooked (see One Simple Error Led to AlphaBay Admin's Downfall).
"The whole underground is in flux right now and will be for a while," Rowley says. "In terms of chatter, people are very, very nervous."
Liv Rowley, an intelligence analyst at threat research firm Flashpoint, talks about how cybercrime-as-a-service providers are reacting to the 2017 takedowns of the AlphaBay and Hansa darknet marketplaces.
Already, many cybercrime forum users appear to be moving away from these centralized types of operations and embracing other options, such as encrypted messaging apps, Rowley says. "We've seen chat platforms being used for sales, which is interesting, and also one-on-one transactions between a buyer and a seller. Someone might post something and say, 'Hit me up on Wickr,' or whatever kind of communication platform they might want to use to conclude the sale."
The use of brand-name apps and services for selling cybercrime services is an increasing trend. "Law enforcement is witnessing a transition into the use of secure apps and other services by criminals across all crime areas," Europol notes in its IOCTA report. "The majority of the apps used are the everyday brand names popular with the general populace."
Others are starting their own shops. "We've seen a rise in personal shops going up," Rowley says. "A criminal will set up a shop, say they're not going to use a centralized shop anymore, if you want to do business with me, you visit me - there's no third party involved."