Hello, Welcome to MalwareTips.
I'm nasdaq and will be helping you.
If you can please print this topic it will make it easier for you to follow the instructions and complete all of the necessary steps in the order listed.
===
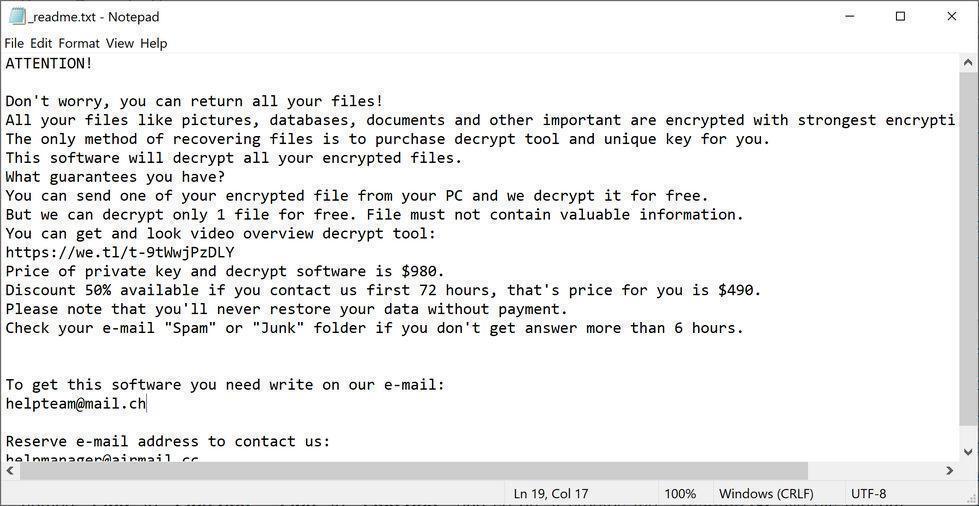
Read about your nusm ransomware infection.
This guide teaches you how to remove NUSM ransomware for free by following easy step-by-step instructions.

malwaretips.com
Your Computer Operating system has not been infected.
Only the documents with these extension are.
it will scan your computer for images, videos, and important productivity documents and files such as .doc, .docx, .xls, .pdf. When these files are detected, the ransomware will encrypt them and change their extension to “.nusm”
Copy the infected files to a CD or Flash Drive. You can hope that a solution may be found later.
However the it's impossible to repair these files now and may be never.
Unless you presently have a good backup of these files on an external drive.
From now on I suggest you make a copy of all your new important files to a Flash or External Hard drive.
===
If you have any other issues with this computer please scan your computer with this program.
Download the Farbar Recovery Scan Tool (FRST).
Choose the 32 or 64 bit version for your system.
and save it to a folder on your computer's Desktop.
Ensure that you are in an Administrator Account
Double-click to run it. When the tool opens click Yes to disclaimer.
Check the boxes as seen here:
Press Scan button.
It will make a log (FRST.txt) in the same directory the tool is run. Please copy and
paste it to your reply.
The first time the tool is run, it makes also another log (Addition.txt). Please
attach it to your reply.
How to attach a file to your reply:
In the
Reply section in the bottom of the topic Click the "
more reply Options" button.
[img=[URL]http://deeprybka.trojaner-board.de/eset/eng/attachlogs.png[/URL]]
Attach the file(s). A 2 Steps process.
Reply to this topic.
Select the "
Choose a File" navigate to the location of the File.
Click the file you wish to Attach. <- Step 1.
Click Attach this file. <- Step 2.
Click the
Add reply button.
Please post the logs for my review.
Let me know what problems persists.
Wait for further instructions
p.s.
The
Farbar program is updated often.
If it's identified as suspicious by your Anti-Virus program trust it if Downloaded from the link I provided.
You should restore the program from the Quarantine folder.
====