A new ransomware is going around that's trying to disguise itself as the more dangerous Locky, but is, in fact, a cheap knock-off, which based on available evidence, might be the work of a Hungarian malware author.
The name of this ransomware strain is Hucky, as in Hungarian Locky, nicknamed so by Jakub Kroustek, the Avast malware analyst that came across it.
Kroustek says he was tipped off that something might have been amiss when he discovered that this new strain, which initially he thought to be Locky, appended the .locky extension to all encrypted files.
Locky hadn't used the .locky file extension for months, switching to .zepto, .odin, .#####, and more recently to .thor.
Hucky is a cheap Locky clone
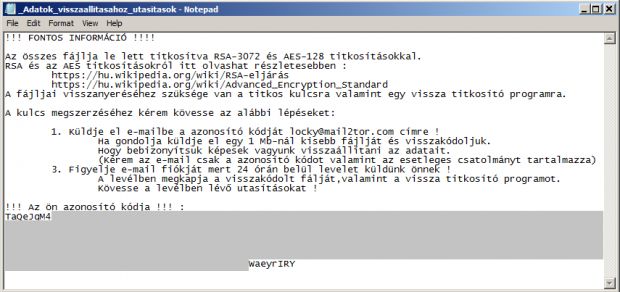
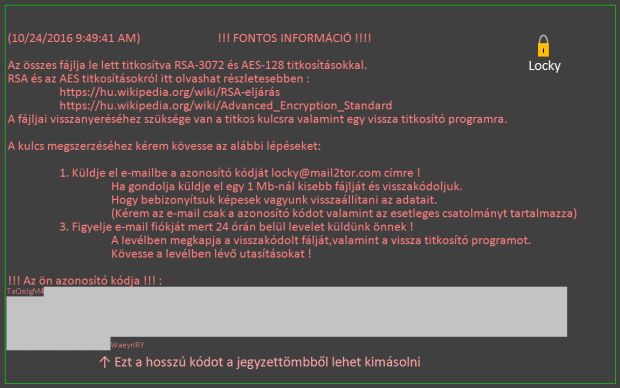
At a closer inspection, Kroustek also discovered that the image which the ransomware used to change the user's desktop wallpaper had also been tampered with, showing a small lock icon in the top upper right corner, something that the original Locky ransomware doesn't show.
Another sign that this wasn't Locky but a cheap clone was the fact that Hucky asked users to email the ransomware author for each infection. Locky uses an automated website hosted on the Dark Web, so there's never a direct connection between the Locky gang and the victims.
The name of this ransomware strain is Hucky, as in Hungarian Locky, nicknamed so by Jakub Kroustek, the Avast malware analyst that came across it.
Kroustek says he was tipped off that something might have been amiss when he discovered that this new strain, which initially he thought to be Locky, appended the .locky extension to all encrypted files.
Locky hadn't used the .locky file extension for months, switching to .zepto, .odin, .#####, and more recently to .thor.
Hucky is a cheap Locky clone
At a closer inspection, Kroustek also discovered that the image which the ransomware used to change the user's desktop wallpaper had also been tampered with, showing a small lock icon in the top upper right corner, something that the original Locky ransomware doesn't show.
Another sign that this wasn't Locky but a cheap clone was the fact that Hucky asked users to email the ransomware author for each infection. Locky uses an automated website hosted on the Dark Web, so there's never a direct connection between the Locky gang and the victims.
Hucky wallpaper image
Additionally, Hucky targeted only half the files Locky targets for encryption, but also went after gaming-related files connected to Minecraft, StarCraft2, and World of Tanks.
Kroustek also found that Hucky was coded in Microsoft VisualBasic, while the original Locky was built with Microsoft Visual C++.
Furthermore, Hucky forcibly restarts the victim's PC after the ransomware finishes encrypting his files, something which Locky never does.
The Hungarian connection
The first clues that this was the work of a Hungarian developer appeared in the image and text-based ransom notes left around the computer, which were only available in Hungarian, and not English.
Analyzing Hucky's source code, Kroustek says he found a large number of Hungarian words. Because most of these were combined with l33t speak, they didn't appear to be false flags, planted by the malware author to throw security researchers off tracks.
Furthermore, PDB debug strings also contained the malware author's potential name, and other Hungarian words.
"[T]he Hungarian texts don’t seem to be machine translated (although they contain some spelling errors)," Kroustek says.
The files used to spread the ransomware were named turul.exe and semmi.exe, Turul being a type of hawk, Hungary's national symbol, and semmi being the Hungarian word for "nothing."
"We can conclude that Hucky is a new ransomware strain currently targeting Hungarian users only. Based on the aforementioned leads, there is a fair chance that its author is a native Hungarian speaker," Kroustek says. "The Hungarian orientation is probably also the reason why Hucky’s prevalence is low at the moment."