Hello,
You will need to download FRST tool on clean computer and to transfer it to the USB drive.
Please download
Farbar Recovery Scan Tool x64 and save it to a flash drive.
- Plug the flashdrive into the infected PC.
- Click Start and while holding Shift key on your keyboard click Power --> Restart.
Note: It is important that you keep Shift key pressed while doing this or it won't work.
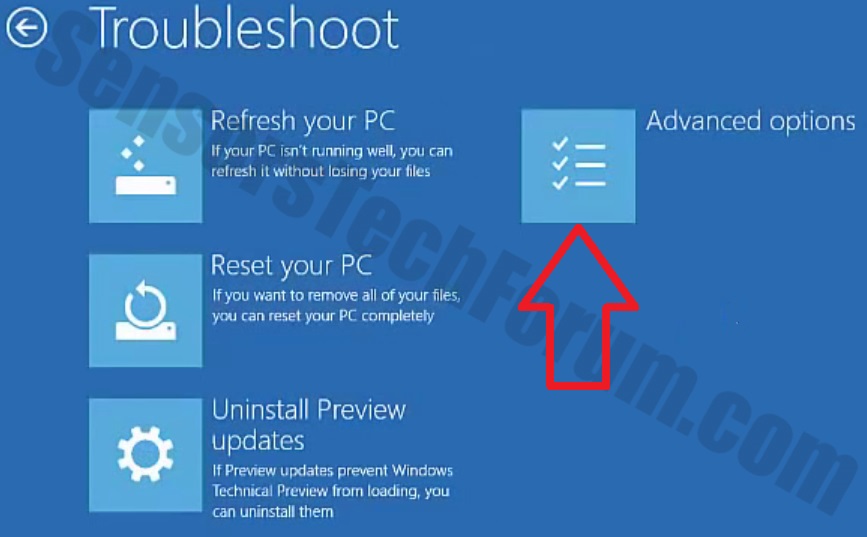
- Now you should get a window like this where you need to click Troubleshoot.
- In the next window, click Advanced options and select Command Prompt.
- Now you should log in into your account and after that Command Promptwindow.
Access the notepad and identify your USB drive
In the Command Prompt please type in:
and press
Enter.
- When the notepad opens, go to File menu.
- Select Open.
- Go to Computer and search there for your USB drive letter.
- Note down the letter and close the notepad.
Scan with Farbar Recovery Scan Tool
Once back in the command prompt window, please do the following:
- Type in e:\frst64.exe and press Enter.
You need to replace e with the letter of your USB drive taken from notepad!
- FRST will start to run. Give him a minute or so to load itself.
- Click Yes to Disclaimer.
- In the main console, please click Scan and wait.
- When finished it will produce a logfile named FRST.txt in the root of your pendrive and display it. Close that logfile.
Transfer it to your clean machine and include it in your next reply.
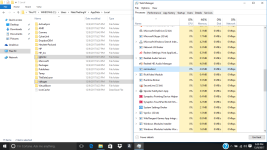
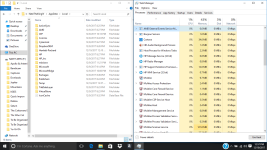
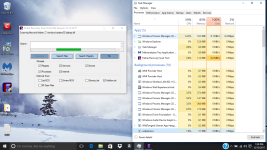
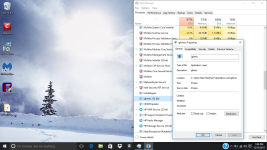
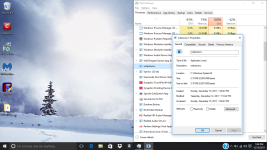
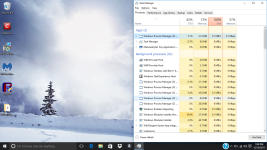
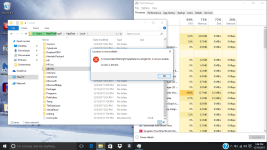
Okay, so i've done it. I feel like i should mention that holding shift and pressing power then restart didn't get me that menu probably because of the virus, i had to turn off my computer and on start up press shift and F8 at the same time repeatedly to get to that menu. I should also mention that i've done a few reinstallations of windows and factory restoring to try to fix the problem myself, but i won't do that again now that i have your attention. The virus is still here, nothing has changed except for the name of the virus that starts it. ticnkwlsvc's name has been changed to remiswbsvc. The name of the task, and folder of igfxmtc has remained the same. The folder where the Windows Process Manager thing is located has had a name changed which changed from wdrlzei, to vdkxges (remember, these changes were only because of resetting). properties of these things have remained the same.
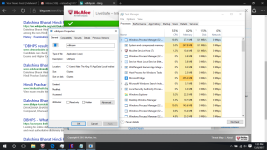
During these reinstallations and factory restoring, i was able to learn a few things about this virus; idk if this info will be helpful. When everything is reset, the virus whose name changes every time doesn't show up right away; it shows up in task manager and in the system32 folder after an hour or two, but after resetting multiple times, idk if this is a coincidence, it seemed to get faster and faster at showing up in task manager and in the folder. When remiswbsvc showed up today, I wanted to take note of a few things (again, idk if this'll help). When remiswbsvc showed up after about a few seconds today after resetting, I was only protected by McAfee, the anti-virus that comes with the computer after resetting. I took note that remiswbsvc stood at a stable 2.5MB memory usage, 0% CPU usage, 0MB/s disk usage, and 0Mbps networking usage while having McAfee's Lockdown setting on, which blocks EVERYTHING from obtaining internet access. After disabling the firewall and real-time scanning in McAfee, remiswbsvc's memory usage went up to 2.9MB memory usage and started using a tiny amount of CPU usage, like, between 1.3%-3.5% and after about a minute after that, igfxmtc showed up in the task manager with it's folder also appearing in the Appdata/Local folder. In task manager, igfxmtc stood at a stable 0.7MB memory usage while everything else at 0. The igfxmtc didn't react to the turning on and off of the firewall and real-time scanning, but remiswbsvc seems like the only one that does. After seeing that, I waited to see when the Windows Process Manager (32-bit) would show up in task manager, but it didn't. I was a little confused by this because the folder that it is suppose to located in was there (vdkxges); still unable to access it (I should mention that the vdkxges folder wasn't there until I disabled the McAfee firewall and real-scan earlier as i said with remiswbsvc). I decided restart my computer (Still with McAfee's Lockdown setting enabled) to see if that would somehow start Windows Process Manger. It didn't... But what did happen was that McAfee's firewall got automatically turned off, even though I turned it on before the restart, I'm pretty sure the viruses did that. After disabling McAfee's lockdown setting and restarting again, I checked the task manager, and remiswbsvc was using CPU, Memory, Network, and a lot of disk usage; and then i witnessed the appearance of multiple Windows Process Manager (32-bit) clients.
Anyways, hopefully that doesn't annoy you, and again, now that i have your attention, i won't reset my computer again unless I get a say so from you. So here's the new FRST.txt from EXACTLY what you told me to do with downloading FRST on a clean computer and transferring it onto a flashdrive and using cmd in the advanced menu, and again, the virus prevented me from accessing it while doing the 'holding shift and restart way'. I had to tap shift + F8 during startup. (The picture i sent was taken before Windows Process Manager showed up in task manager(also with a new description of imnsvri instead of vdbhpsm), but the FRST.txt file uploaded was after Windows Process Manager showed up)