MADRID—As the investigation continues into the backdoor planted inside CCleaner, two members of parent company Avast’s threat intelligence team said today the desktop and cloud versions of the popular software contained different payloads.
The revelation was made during a talk at Virus Bulletin 2017 during which Jakub Kroustek and Jiri Bracek shared technical details on the attack, primarily about the command and control infrastructure used for communication, as well as some insight on the targets and hinted that there may be other stages of this attack that have yet to be uncovered.
Kroustek and Bracek said there are likely more than the three stages of this attack that have been discussed so far; each stage to date has been a downloader grabbing the next phase of the operation. IP addresses housing these stages are hidden, either encrypted with custom cryptographic algorithms or tucked away on phishing sites or purpose-built Github or WordPress pages that are scanned by the malware in order to piece together clues as to the IP addresses holding the next stage.
The revelation was made during a talk at Virus Bulletin 2017 during which Jakub Kroustek and Jiri Bracek shared technical details on the attack, primarily about the command and control infrastructure used for communication, as well as some insight on the targets and hinted that there may be other stages of this attack that have yet to be uncovered.
Kroustek and Bracek said there are likely more than the three stages of this attack that have been discussed so far; each stage to date has been a downloader grabbing the next phase of the operation. IP addresses housing these stages are hidden, either encrypted with custom cryptographic algorithms or tucked away on phishing sites or purpose-built Github or WordPress pages that are scanned by the malware in order to piece together clues as to the IP addresses holding the next stage.
More evidence seems to point toward this being a targeted attack with only 40 installations of the second stage payload reported to Avast out of more than 2.27 million customers who received a compromised version of the PC maintenance software.
“This suggests it was very targeted and used only against a specific group of users,” Bracek said.
The researchers shared a list of domains from the malware suggesting that if a compromised machine from one of those domains connected it would receive the second stage payload. Those domains include Samsung, Microsoft, Sony, Akamai and others indicating that espionage could be the goal of this attack.
Meanwhile, it appears that the attackers behind this campaign were fairly agile in updating their code as the campaign progressed. For example, CCleaner version 5.33 and CCleaner Cloud 1.7.0 contained different payloads.
“There were slight, but important modifications,” Kroustek said. “The payload in CCleaner 5.33 contains a condition that if the user is not an admin, the shellcode exits. That was removed in the cloud version and CCleaner contacted the IPs for the second stage regardless.”
Kroustek and Bracek said the investigation with law enforcement continues, and not all findings could be shared. The researchers recapped the attack, which started with a compromise of a build server owned by Piriform, CCleaner’s original developer which was acquired by Avast in July.
According to a timeline shared by the researchers, Piriform was breached in April with attackers gaining access to build servers inside the organization. A self-signed digital certificate used to sign the first stage of the attack was created on July 4, two weeks before the Avast acquisition. On Aug. 2, the first build of CCleaner containing a malicious payload was released, followed on Aug. 11 by the first malicious version of CCleaner Cloud.
For some unknown, or undisclosed reason, versions of CCleaner without a malicious payload were built starting Aug. 25, 18 days before Avast was privately notified by Morphisec that CCleaner may be compromised. On Sept. 15, the first stage command and control infrastructure was taken down in conjunction with law enforcement, and three days later, the breach was publicly disclosed.
The researchers said the first stage of the attack was self-signed by the attackers with a Piriform certificate. The payload was found in only the 32-bit versions of the product and had likely been injected during the build process during compilation. The attackers intended on making life difficult for analysts, including many anti-debugging features in their code, as well as custom crypto throughout. The payload, meanwhile, was a downloader ordered to grab the second stage of the attack. It also sent some system data from clients, the most valuable of which being the computer name and domain on which the PC is running, along with a list of running processes. Contact was made through a fixed IP address in the code; there was also a Domain Generation Algorithm present, but that was sinkholed by Cisco’s Talos research team, which also discovered and disclosed the breach simultaneous to Morphisec.
Avast would not definitively attribute the source of the compromise, but conceded there are code similarities between the CCleaner attack and code belonging to APT17, also known as Axiom or Deputy Dog. APT 17 is believed to be tied to the Chinese government and has been implicated in the Aurora attacks. Costin Raiu of Kaspersky Lab shared tweets shortly after the CCleaner disclosure indicating that there was shared code between the two.
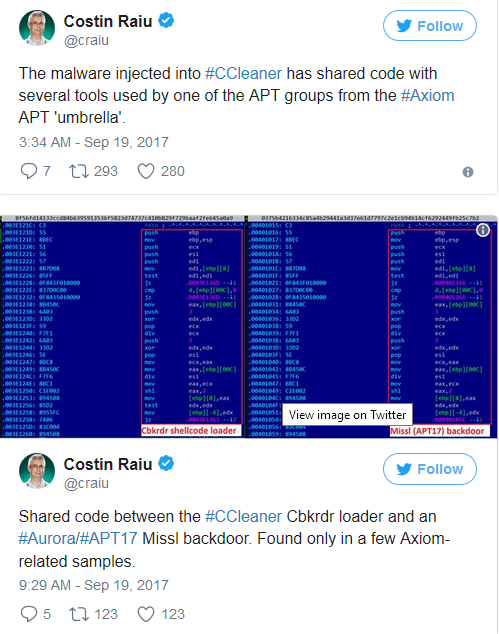
Kroustek said that a small buffer was found in the CCleaner attack that is similar to one found in an APT17 backdoor.
“There are some significant similarities between the codes,” he said. “I’m not saying it’s the same code, but I’m saying the two binaries are show more and more similar code.”
Command and control activity logs also seem to line up with the work day in China (UTC+8). The first-stage payload database also revealed 1.6 million unique MAC addresses and 5.6 million overall records. There were, however, only 45 records indicating second-stage attacks, and those were sent to 40 unique PCs, they said.
Bracek said that this demonstrates the risk of whitelisting signed apps such as CCleaner, in particular if a supply chain attack is involved.
“A secure build infrastructure must be a top priority,” he said.