- Feb 4, 2016
- 2,520
Intel published a security advisory last night detailing eight vulnerabilities that impact core CPU technologies such as the Intel Management Engine (ME), Intel Server Platform Services (SPS), and Intel Trusted Execution Engine (TXE).
The vulnerabilities are severe enough to allow attackers to install rootkits on vulnerable PCs, retrieve data processed inside CPUs, and cause PC crashes —which should be the least of someone's worries.
One of the affected products is the Intel Management Engine, a technology that is often described as a secret CPU inside the main Intel CPU. The ME component runs independently from the user's main OS, with separate processes, threads, memory manager, hardware bus driver, file system, and many other components. An attacker that exploits a flaw and gains control over the Intel ME has untethered control over the entire computer.
The CPU maker has released firmware updates to address these flaws. The updates are not available to the general public, as chipset and motherboard vendors will have to integrate the updates into their own updates. Lenovo has already issued patches for some products that are using vulnerable Intel ME, SPS, or TXE technologies.
Who's affected?
According to Intel, the following Intel ME, SPS, and TXE firmware versions are affected:
ME firmware versions 11.0/11.5/11.6/11.7/11.10/11.20
SPS Firmware version 4.0
TXE version 3.0
According to Intel, the following products incorporate vulnerable firmware versions:
6th, 7th & 8th Generation Intel® Core™ Processor Family
Intel® Xeon® Processor E3-1200 v5 & v6 Product Family
Intel® Xeon® Processor Scalable Family
Intel® Xeon® Processor W Family
Intel® Atom® C3000 Processor Family
Apollo Lake Intel® Atom Processor E3900 series
Apollo Lake Intel® Pentium™
Celeron™ N and J series Processors
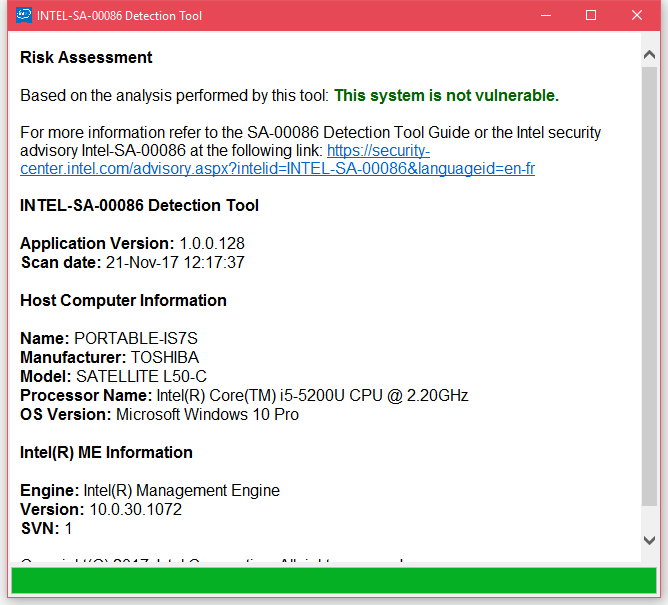
Intel has released a tool for Windows and Linux users that checks and reports if users' computers are affected. On Windows, users should run the Intel-SA-00086-GUI.exe file to view scan results (image below).