Struggles With Firmware Fixes for Meltdown and Spectre

Source: Intel
The usual advice for major security flaws is to patch as quickly as possible. Now Intel is calling for a full stop due to imperfect patches for a trio of chip security vulnerabilities known as Meltdown and Spectre.
See Also: Effective Cyber Threat Hunting Requires an Actor and Incident Centric Approach
Intel on Monday advised all users to not apply firmware patches while it works out kinks in patches that caused systems to unexpectedly reboot. The issue, acknowledged by Intel on Jan. 11, affects chip platforms that include Ivy Bridge, Sandy Bridge, Skylake, Kaby Lake, Broadwell and Haswell (see Intel Confirms Fresh Spectre, Meltdown Patch Problems).
The advice is the latest twist in a saga that began last year, when research groups discovered variations of the same problem. Hardware flaws could allow attackers to peek into the memory of other applications, taking advantage of a design that allows chips to perform better, called speculative execution (see Serious Meltdown and Spectre Flaws Make CPUs Exploitable).
Although attacks exploiting the flaws are not simple, a successful one could divulge passwords, encryption keys and other data in memory. The flaws are present in billions of devices made over the past 20 years and also affected chips made by AMD and ARM.
Pause Some Patching
Intel has isolated the cause of the reboot problem for Haswell and Broadwell, Navin Shenoy, executive vice president and general manager of Intel's Data Center Group, wrote on Monday.
"Over the weekend, we began rolling out an early version of the updated solution to industry partners for testing, and we will make a final release available once that testing has been completed," Shenoy wrote in a blog post.
But for other chip lines, it appears that users will have to wait.
"We recommend that OEMs, cloud service providers, system manufacturers, software vendors and end users stop deployment of current versions, as they may introduce higher than expected reboots and other unpredictable system behavior," Shenoy wrote.
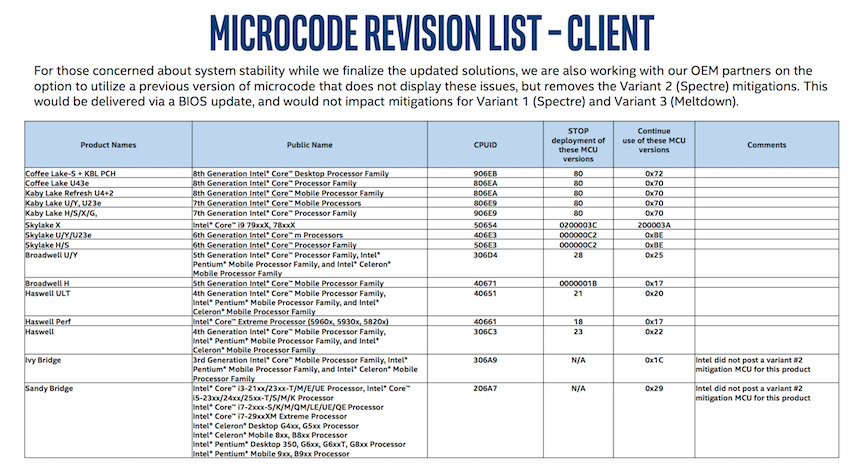
Intel has released a list of processors (partial list above) listing their working/non-working firmware updates.
Last week, Shenoy wrote that Intel had issued patches for 90 percent of its CPUs made over the last five years.
Along with Sheny's blog post, Intel also published a five-page guide that gives more detail into how it plans to solve the issues. In order to get the patches out, it may release firmware that doesn't have a fix for the second variant of Spectre.
"For those concerned about system stability while we finalize the updated solutions, we are also working with our OEM partners on the option to utilize a previous version of microcode that does not display these issues, but removes the Variant 2 (Spectre) mitigations," Intel's guidance reads.
Spectre variant 2 is a branch target injection issue (CVE-2017-5715). Intel says that its fix would be delivered through a BIOS update and would not affect Meltdown or Spectre's first variant.
A Spectre attack can be executed locally or over the web with malicious JavaScript. Web browser makers have either issued fixes with mitigations or are working on them.
Between Meltdown and Spectre, "Spectre is worse," writes renowned cryptographer and security expert Bruce Schneier in The Atlantic. "It's a flaw in the very concept of speculative execution. There's no way to patch that vulnerability; the chips need to be redesigned in such a way as to eliminate it."
Tricky Fixes
Pending some semiconductor design magic, future chips should not be vulnerable to the flaws. But replacing microchips in billions of devices now isn't an option. And continuing patch problems demonstrate just how difficult it can be to try and fix fundamental flaws in hardware.
Chipmakers and software vendors had six months to prep patches before Meltdown and Spectre became public. The details of Meltdown and Spectre were held in strict confidence while a coordinated effort worked on fixes. Eventually, however, the flaws leaked in early January, slightly ahead of the agreed Jan. 9 embargo date.
"As it is, the patches are complete and utter garbage. They are literally insane."
—Linus Torvalds, Linux kernel creator
Luckily, the fact that the three vulnerabilities are fairly difficult to exploit has left a bit of breathing room amidst the ongoing patch problems. But Schneier warns there may not be that much lead time the next time around.
"Even when manufacturers like Intel and AMD can write a patch for a vulnerability, computer makers and application vendors still have to customize and push the patch out to the users," he writes. "This makes it much harder to keep vulnerabilities secret while patches are being written."
Intel also isn't the only vendor to have problems patching Meltdown and Spectre.
Microsoft pulled patches for some AMD chipsets after the update froze users' computers. The company also required that anti-virus makers set a registry key in order for the patch, or any future security updates, to be delivered to system (see Warning: Microsoft Fix Freezes Some PCs With AMD Chips).
Some anti-virus makers resisted altering users' systems, but Microsoft maintained it was necessary to prevent systems from crashing. The issue was traced to some security programs making unsupported calls to the Windows kernel memory.
Linus Torvalds, creator of the Linux kernel, has also taken issue with the quality of Intel's patches for the operating system.
"As it is, the patches are complete and utter garbage," Torvalds wrote to the Linux kernel mailing list on Sunday. "They do literally insane things. They do things that do not make sense."