Happened to saw this email.
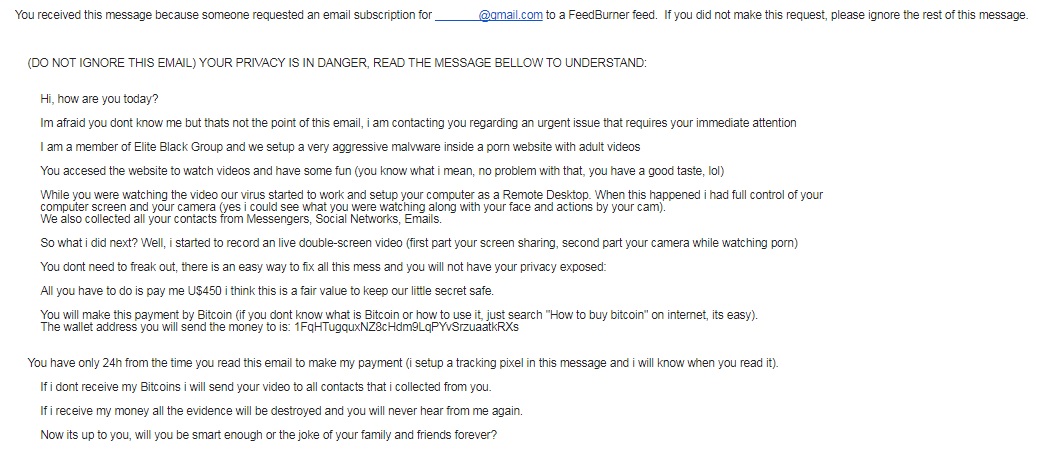
From the looks of it, it's a ransom scam.
But really curious, on this tech part.
" While you were watching the video our virus started to work and setup your computer as a Remote Desktop. When this happened i had full control of your computer screen and your camera (yes i could see what you were watching along with your face and actions by your cam). We also collected all your contacts from Messengers, Social Networks, Emails. So what i did next? Well, i started to record an live double-screen video (first part your screen sharing, second part your camera while watching porn)"
Is this possible without noticing?
Just out of curiosity and for sharing knowledge purposes.
From the looks of it, it's a ransom scam.
But really curious, on this tech part.
" While you were watching the video our virus started to work and setup your computer as a Remote Desktop. When this happened i had full control of your computer screen and your camera (yes i could see what you were watching along with your face and actions by your cam). We also collected all your contacts from Messengers, Social Networks, Emails. So what i did next? Well, i started to record an live double-screen video (first part your screen sharing, second part your camera while watching porn)"
Is this possible without noticing?
Just out of curiosity and for sharing knowledge purposes.