JavaScript libraries from various advertising and analytics services are siphoning user data from web pages where the "Login with Facebook" feature is being used.
Academics from Princeton University discovered that 434 of the top 1 million sites are loading JavaScript code from third-party services that are dipping into "Login with Facebook" data.
Researchers believe that most of the 434 services are likely unaware that this is happening on their sites.
Data collection scenario #1
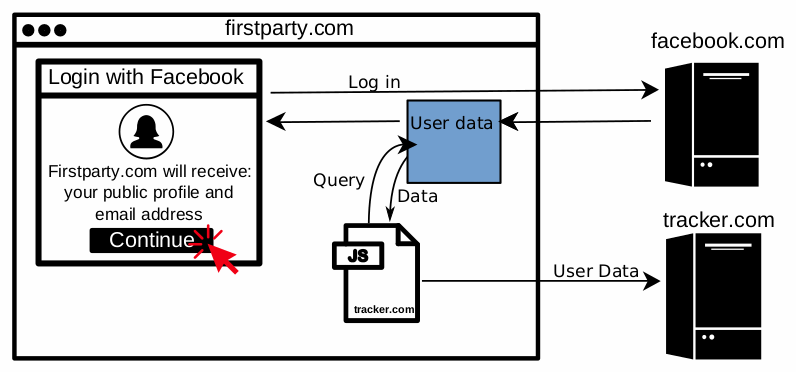
The research team says that the data collection usually occurs in two different ways. The first case is on sites that use a "Login with Facebook" feature to authenticate users.
When a user wants to log into his account, the "Login with Facebook" feature makes a request to Facebook servers, which respond back with the Facebook account data that a user has allowed that specific site to access.
Third-party JavaScript code that loads on the login page is capable of intercepting this data and extracting user details.
Princeton researchers say they've identified seven analytics/user-tracking services engaging in such practices [table below].
.... ... ....
..... ....
...