A new ransomware variant dubbed Karmen has made an appearance on the Dark Web. Interestingly, the strain automatically deletes the decryptor if a sandbox environment or analysis software is detected on the victim’s computer.
According to Record Future, the malware is a ransomware as a service (RaaS) offering derived from Hidden Tear, an open-source ransomware project. It encrypts files on the infected machine using the strong AES-256 encryption protocol. And because it automatically deletes the decryptor if a sandbox environment or analysis software is detected on the victim’s computer, these machines won’t get their files back, even if their owners pay the ransom.
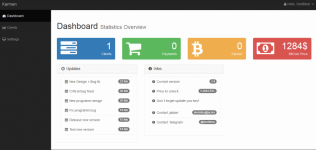
Also of interest is Karmen’s user-friendly interface, geared to those with limited technical knowledge. It offers a dashboard with a graphical overview of relevant information, including the number of clients they have, how much money they’ve earned and updates to the Karmen software (updates are free). It also allows users to change the malware’s settings using a control panel, while a “Clients” page tracks computers infected with the virus, with a separate Bitcoin wallet for each victim. The whole package goes for just $175.
Recorded future said that so far, 20 copies of Karmen malware have been sold, while only five copies remain available to potential buyers.
Read More. Karmen Ransomware: User-friendly, Sandbox-averse
According to Record Future, the malware is a ransomware as a service (RaaS) offering derived from Hidden Tear, an open-source ransomware project. It encrypts files on the infected machine using the strong AES-256 encryption protocol. And because it automatically deletes the decryptor if a sandbox environment or analysis software is detected on the victim’s computer, these machines won’t get their files back, even if their owners pay the ransom.
Also of interest is Karmen’s user-friendly interface, geared to those with limited technical knowledge. It offers a dashboard with a graphical overview of relevant information, including the number of clients they have, how much money they’ve earned and updates to the Karmen software (updates are free). It also allows users to change the malware’s settings using a control panel, while a “Clients” page tracks computers infected with the virus, with a separate Bitcoin wallet for each victim. The whole package goes for just $175.
Recorded future said that so far, 20 copies of Karmen malware have been sold, while only five copies remain available to potential buyers.
Read More. Karmen Ransomware: User-friendly, Sandbox-averse