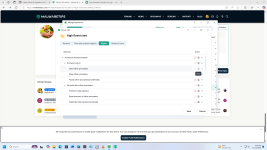
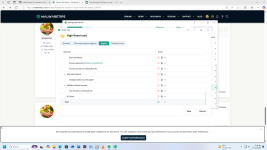
I changed my Kaspersky intrusion prevention settings to untrusted/untrusted after reading that that option provides the best possible protection.
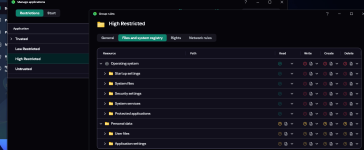
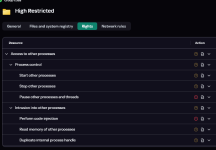
My question is what would happen if I put a trusted application (trusted by KSN) into high restricted group manually.
Also, let's just assume that something like VLC Player decided to go rogue and plant malware on users with a new update. Will Kaspersky be able to stop that if we added it into high restricted category before the update?
I'm just curious how high restricted differs from trusted and how it works.
Thank you for any assistance.
My question is what would happen if I put a trusted application (trusted by KSN) into high restricted group manually.
Also, let's just assume that something like VLC Player decided to go rogue and plant malware on users with a new update. Will Kaspersky be able to stop that if we added it into high restricted category before the update?
I'm just curious how high restricted differs from trusted and how it works.
Thank you for any assistance.