- Jun 9, 2013
- 6,720
Good news from the world of cyber-crime as the owner of the KeyBase keylogger has announced that he decided to call it quits and close down the project after receiving numerous complaints that his "legitimate" product has been used for illegal activities.
Bearing a similar name to the KeyBase(.io) public key store, the KeyBase.in service was launched in early 2015 and for more than a year advertised and sold a keylogging application called KeyBase.
From keylogger to infostealer, KeyBase takes the path to the Dark Side
While initially, the project was only a keylogger, allowing users to record the keys pushed on a computer, it soon evolved into more than that, gaining the capabilities of a full-blown infostealer.
Across time, KeyBase received updates that allowed it to take screenshots of the computer it was installed on, capture clipboard data, and even extract logins from various applications.
The full list of supported applications includes Web browsers (Mozilla Firefox, Google Chrome, Internet Explorer, Safari for Windows, Opera for PC) email clients (Microsoft Outlook, Mozilla Thunderbird, Netscape
Eudora, Incredimail), and miscellaneous applications (Internet Download Manager, IMVU, Paltalk, Filezilla, JDownloader).
All this time, KeyBase's author publicly stated that he did not want his tool associated with cyber-crime operations, yet he added features only specific to this type of activity.
KeyBase uses as payload to spy on small companies
In a report for Virus Bulletin, Sophos researcher Gabor Szappanos, reveals several cyber-crime operations that have packaged KeyBase inside Office exploit kits or spam emails that infected computers across the world.
Szappanos says that crooks used KeyBase to infect the computers of small businesses in countries such as India, Indonesia, Bangladesh, and Djibouti.
Because KeyBase relied on a server-side component to receive stolen data, by inspecting some of these servers, the researcher found several campaigns, some holding data, but other empty (possible ended or preparing to start).
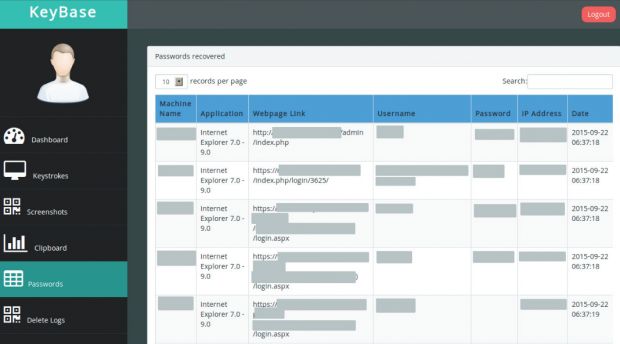
KeyBase server-side administration panel
KeyBase shuts down with a promise to do good
Sometimes last winter, KeyBase's author decided that he had enough, and posted the following message on the app's website.
“ Sorry! Your are late. This project has been discontinued due to increasing number of complaints regarding abuse and sales are stopped. Hi everyone! I am extremely disappointed about how some of the users have used KeyBase and I am sorry to announce that this is the end of the project. I am not taking new sales anymore and I have closed licenses for all abusers. Please be notified that if you have done something malicious and have any officials searching for you, I will give the details of concerned suspect to proper authorities. Thanks for reading! ”
While we salute the author's decision to collaborate with authorities, it might have been a better idea not to add offensive hacking features to KeyBase, to begin with. Of course, the fact that the keylogger's source code was leaked online last summer didn't help his business either.
A few months after he shut down the KeyBase website, the URL now hosts the homepage of a mineral processing company.
Read More. KeyBase Keylogger Shuts Down, Author Says He'll Help Police Investigations
Bearing a similar name to the KeyBase(.io) public key store, the KeyBase.in service was launched in early 2015 and for more than a year advertised and sold a keylogging application called KeyBase.
From keylogger to infostealer, KeyBase takes the path to the Dark Side
While initially, the project was only a keylogger, allowing users to record the keys pushed on a computer, it soon evolved into more than that, gaining the capabilities of a full-blown infostealer.
Across time, KeyBase received updates that allowed it to take screenshots of the computer it was installed on, capture clipboard data, and even extract logins from various applications.
The full list of supported applications includes Web browsers (Mozilla Firefox, Google Chrome, Internet Explorer, Safari for Windows, Opera for PC) email clients (Microsoft Outlook, Mozilla Thunderbird, Netscape
Eudora, Incredimail), and miscellaneous applications (Internet Download Manager, IMVU, Paltalk, Filezilla, JDownloader).
All this time, KeyBase's author publicly stated that he did not want his tool associated with cyber-crime operations, yet he added features only specific to this type of activity.
KeyBase uses as payload to spy on small companies
In a report for Virus Bulletin, Sophos researcher Gabor Szappanos, reveals several cyber-crime operations that have packaged KeyBase inside Office exploit kits or spam emails that infected computers across the world.
Szappanos says that crooks used KeyBase to infect the computers of small businesses in countries such as India, Indonesia, Bangladesh, and Djibouti.
Because KeyBase relied on a server-side component to receive stolen data, by inspecting some of these servers, the researcher found several campaigns, some holding data, but other empty (possible ended or preparing to start).

KeyBase server-side administration panel
KeyBase shuts down with a promise to do good
Sometimes last winter, KeyBase's author decided that he had enough, and posted the following message on the app's website.
“ Sorry! Your are late. This project has been discontinued due to increasing number of complaints regarding abuse and sales are stopped. Hi everyone! I am extremely disappointed about how some of the users have used KeyBase and I am sorry to announce that this is the end of the project. I am not taking new sales anymore and I have closed licenses for all abusers. Please be notified that if you have done something malicious and have any officials searching for you, I will give the details of concerned suspect to proper authorities. Thanks for reading! ”
While we salute the author's decision to collaborate with authorities, it might have been a better idea not to add offensive hacking features to KeyBase, to begin with. Of course, the fact that the keylogger's source code was leaked online last summer didn't help his business either.
A few months after he shut down the KeyBase website, the URL now hosts the homepage of a mineral processing company.
Read More. KeyBase Keylogger Shuts Down, Author Says He'll Help Police Investigations

