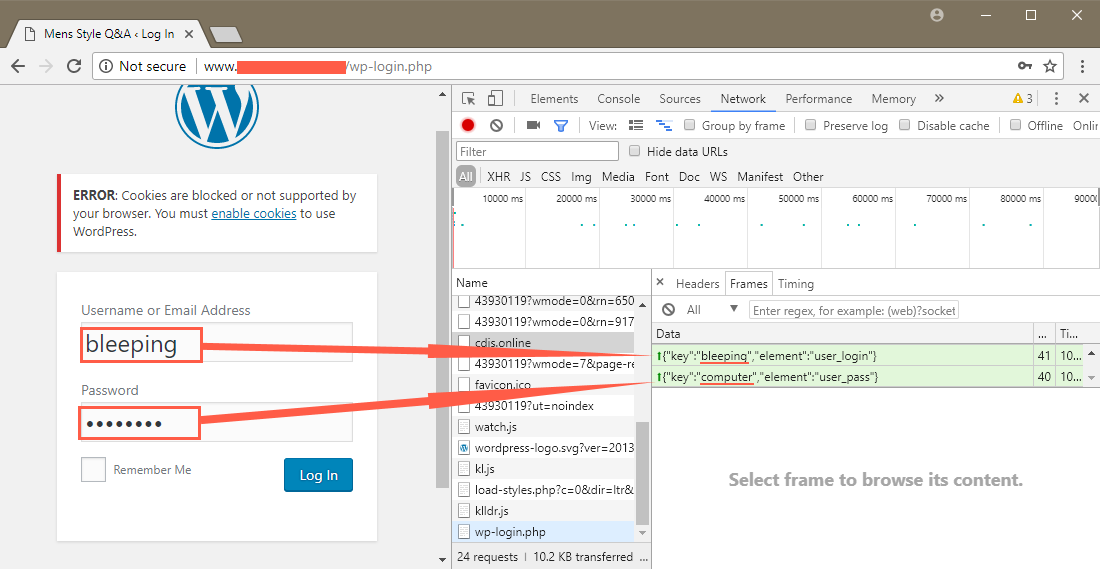
Security researchers have discovered over 2,000 WordPress sites —possibly more— infected with a keylogger that's being loaded on the WordPress backend login page and a cryptojacking script (in-browser cryptocurrency miner) on their frontends.
Researchers have tied these newly discovered infected sites to a
similar operation that took place in early December 2017.
The attack is quite simple. Miscreants find unsecured WordPress sites —usually running older WordPress versions or older themes and plugins— and use exploits for those sites to inject malicious code into the CMS' source code.
The malicious code includes two parts. For the admin login page, the code loads a keylogger hosted on a third-party domain. For the site's frontend, crooks load the Coinhive in-browser miner and mine Monero using the CPUs of people visiting the site.