
uncovered and it affects most popular browsers. Here’s how Weakdh.org describes it:
The Logjam attack allows a man-in-the-middle attacker to downgrade vulnerable TLS connections to 512-bit export-grade cryptography. This allows the attacker to read and modify any data passed over the connection. The attack is reminiscent of the FREAK attack, but is due to a flaw in the TLS protocol rather than an implementation vulnerability, and attacks a Diffie-Hellman key exchange rather than an RSA key exchange. The attack affects any server that supports DHE_EXPORT ciphers, and affects all modern web browsers.
Browser developers are supposedly in the process of preparing updates but, at the time of writing this article, I checked the three major browsers I have installed and both Firefox (38.0.1) and Chrome (43.0.2357.81 m) were both reported as vulnerable. Somewhat surprisingly, Internet Explorer (11.0.9600.17801) was the only one of the three given a clean bill of health.How to Check Your Browser for the Logjam Vulnerability
There are currently two sites you can visit to automatically check your browser for the Logjam vulnerability:
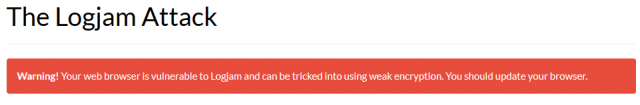
- https://weakdh.org/ – if you visit this site and receive the following message, then your browser is vulnerable:
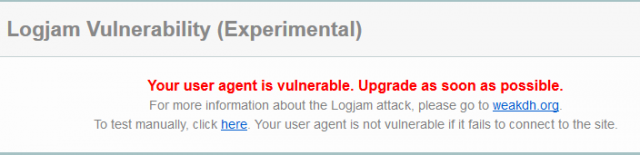
- https://www.ssllabs.com/ssltest/viewMyClient.html – similarly, this site will display the following message if your browser is vulnerable:
How to Fix the Logjam Vulnerability in Firefox
According to reports, the Logjam vulnerability won’t be patched in Firefox until the release of version 39. However, a temporary fix has been published on the Mozilla forum for Firefox users which involves accessing “about:config” and disabling the ssl3 protocol:
- In a new tab, type or paste about:config in the address bar and press Enter. Click the button promising to be careful.
- In the search box above the list, type or paste ssl3 and pause while the list is filtered
- Double-click the security.ssl3.dhe_rsa_aes_128_sha preference to switch it from true to false (this usually would be the first item on the list)
- Double-click the security.ssl3.dhe_rsa_aes_256_sha preference to switch it from true to false (this usually would be the second item on the list)
- Restart Firefox
For any browsers that are being reported as vulnerable, I strongly suggest users keep a close eye out for updates and apply same as soon as they become available.
More information here: The Logjam (and Another) Vulnerability against Diffie-Hellman Key Exchange – (security expert Bruce Schneier reports that the vulnerability may have been exploited by the NSA)

