Canadian Charged With Selling Access to Stolen Logins, Earning $247,000
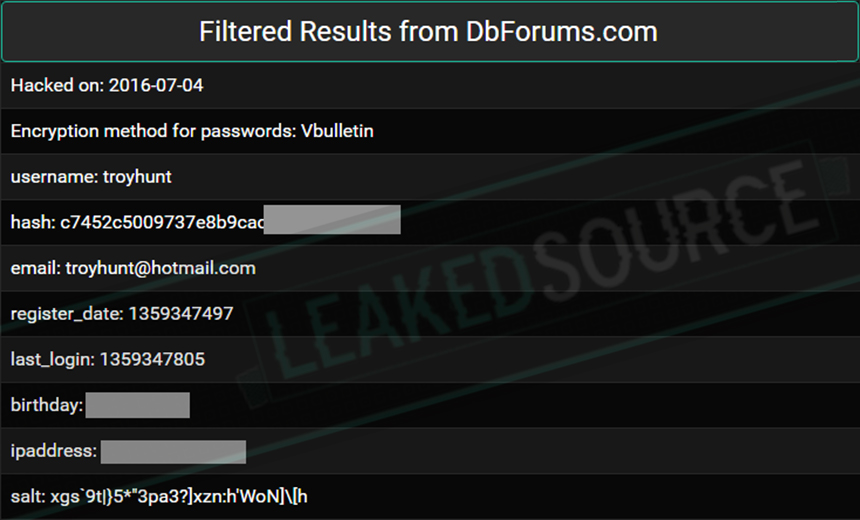
Result from a paid data search on LeakedSource.com. (Source: Troy Hunt)
Canadian authorities have charged a 27-year-old man in connection with LeakedSource, a website that raised eyebrows by selling access to 3.1 billion login credentials stolen from dozens of online services, including LinkedIn, MySpace and Dropbox.
See Also: Addressing the Identity Risk Factor in the Age of 'Need It Now'
Jordan Evan Bloom of Thornhill, Ontario, appeared in court Monday to face charges of trafficking in identity information, unauthorized use of a computer, mischief to data and possession of property obtained by crime.
Bloom allegedly made $247,000 by administering LeakedSource and selling personal data, the Royal Canadian Mounted Police say in a news release. The RCMP's investigation began in 2016, when it learned LeakedSource.com was being hosted by servers located in Quebec. The FBI and Dutch National Police both assisted the investigation, it says.

LeakedSource's masthead.
LeakedSource has been offline since January 2017. Around that time, someone posted an anonymous note on Pastebin saying the site's owner had been raided by law enforcement, which seized solid-state hard drives (see LeakedSource's Demise: Lessons Learned).
Legal Gray Area
LeakedSource operated in somewhat of a legal gray area when it debuted in late 2015.
In an apparent attempt to try and stay on the right side of the law, the site positioned itself as a breach notification service, offering subscriptions. But the site also sold full access to dumped login credentials.
The site claimed that such data wasn't collected directly through hacking but instead via research. "We've accumulated hundreds of databases, not through a miraculously successful spate of hacking attempts, but by scouring the internet and dark web for data," LeakedSource wrote in a now-archived FAQ. "Some of what we find is very new, some is fairly old. We're scavengers, not hackers - we don't get to pick and choose."
But selling people's stolen personal data features on the list of charges against Bloom.
"Some of what we find is very new, some is fairly old. We're scavengers, not hackers - we don't get to pick and choose."
—LeakedSource.com
Security researchers and even journalists often come into contact with stolen data. Such troves are also available to download in corners of the internet. Under a strict interpretation of most countries' computer securities laws, possessing such data might be illegal. But it's impossible to do security-related research or reporting without encountering such data, at least occasionally.
Data Breach Abusers
Many experts, however, had a dim view of LeakedSource, doubting the paid service's motives.
Other breach notification services, such as Troy Hunt's Have I Been Pwned, do not offer full access to stolen data. Hunt's service notifies people if their email address appears in data dumps, but does not let them know what password was used. In fact, no passwords are retrievable from his service, which is free.
But with LeakedSource, users could search for credentials using a username, IP address, phone number, email address, name or other personally identifying information. That potentially cut down the time needed to compromise an account that an attacker might be targeting. If an attacker already possessed a bit of information about a potential victim, LeakedSource would in theory be one way to try and identify a password hash of the password commonly used by the victim.
Hunt has long been a vocal critic of LeakedSource, and says the legal ramifications now facing the site's alleged operator are good news. "This may be the important precedent we need to start cleaning up the shady industry abusing data breaches," Hunt says via Twitter. "This group was selling extensive amounts of personal data (including mine), cracked passwords and other PII, often advertised on hacking forums."
Rapid Source of Leaked Data
LeakedSource obtained data from new breaches so quickly that some speculated that the site might be paying hackers for data troves, although that has never been confirmed.
For example, LeakedSource was the first website to claim to hold data from breaches at Badoo.com, Adult FriendFinder, LinkedIn, Dropbox, MySpace and the Russian web portal Rambler.
LeakedSource particularly irritated LinkedIn. The business social networking site suffered a breach in 2012 that initially appeared to have leaked 6.5 million credentials. But in 2016, LinkedIn found that the breach was far worse than that: 160 million usernames and hashed passwords had been exposed (see LinkedIn Breach: Worse Than Advertised).
Subsequently, LeakedSource added all of that breached user data to its service. In May 2016, LinkedIn responded with a cease-and-desist order. While LeakedSource censored the hashes, it charged that LinkedIn was "blowing steam out of their ass," saying its order had been meaningless, due to jurisdictional issues.
While the original LeakedSource.com is still offline, a purported clone apparently based in Russia lives on. That site offers the same number of records - 3.1 billion - and appears to be a working copy of the original LeakedSource.