- Jul 27, 2015
- 5,458
Since April 2021, Cisco Talos has observed updated infrastructure and new components associated with the Lemon Duck cryptocurrency mining botnet that target unpatched Microsoft Exchange Servers and attempt to download and execute payloads for Cobalt Strike DNS beacons. This activity reflects updated tactics, techniques, and procedures (TTPs) associated with this threat actor. After several zero-day Microsoft Exchange Server vulnerabilities were made public on March 2, Cisco Talos and several other security researchers began observing various threat actors, including Lemon Duck, leveraging these vulnerabilities for initial exploitation before security patches were made available.
Looking more closely at the geographic distribution of the domain resolution requests related to this activity, we observed that the majority of them originated from North America, followed by Europe, South East Asia, with a few others from South America and Africa. This is in contrast to the query distribution observed in October 2020, as described in our previous publication where the majority of the queries originated from Asia.
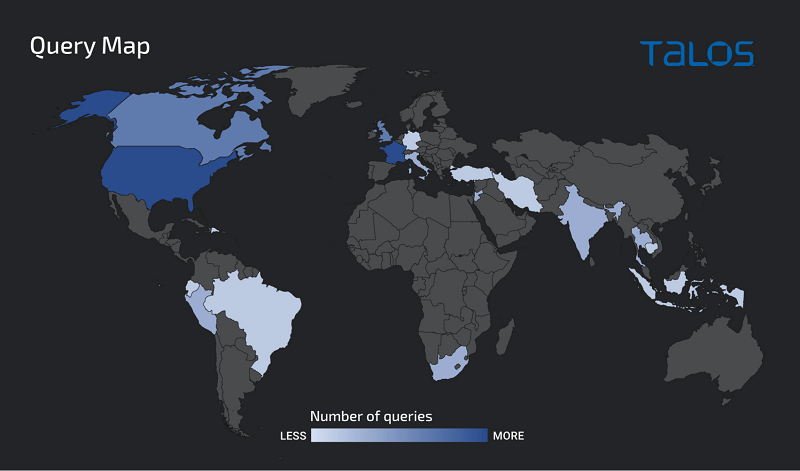
Notably, for one of these domains, d[.]hwqloan[.]com, over sixty percent of the DNS queries originated from India. We determined this activity was associated with infected systems attempting to communicate with Lemon Duck infrastructure. Since the communication with these domains typically occurs during the Lemon Duck infection process, this activity may be indicative of the geographic distribution of the victims of these campaigns.
In Talos' original coverage of Lemon Duck, we described multiple overlaps between Lemon Duck and another cryptocurrency-mining malware, Beapy (aka Pcastle), which had previously been observed targeting East Asia. At the time, Lemon Duck infections reported by other security researchers were being observed in much higher concentrations in China. While Lemon Duck's currently observed victimology and methods of propagation are largely indiscriminate, the seemingly exclusive use of country code TLDs (ccTLDs) for China, Japan and South Korea in the fake domains written to the Windows hosts file is notable, as described in the section "Command and control (C2)" below. Considering these ccTLDs are most commonly used for websites in their respective countries and languages, it is also interesting that they were used, rather than more generic and globally used TLDs such as ".com" or ".net." This may allow the threat actor to more effectively hide C2 communications among other web traffic present in victim environments. Due to the prevalence of domains using these ccTLDs, web traffic to the domains using the ccTLDs may be more easily attributed as noise to victims within these countries.

Lemon Duck spreads its wings: Actors target Microsoft Exchange servers, incorporate new TTPs
By Caitlin Huey and Andrew Windsor with contributions from Edmund Brumaghin. * Lemon Duck continues to refine and improve upon their tactics, techniques and procedures as they attempt to maximize the effectiveness of their campaigns. * Lemon Duck remains relevant as the operators begin to...
 blog.talosintelligence.com
blog.talosintelligence.com
