- Apr 25, 2013
- 5,356
If you are a regular here you know that you can modify quite a few Google Chrome settings on the chrome://flags/ page.
The majority of settings that you find there are not yet ready for prime time. Some technologies may still be in active development, other features are tested by Google and made available to a wider audience through flags.
Since you find more than a hundred flags on the page at any time, it can be quite time consuming to go through all them regularly to find out what is new.
Since the flags don't appear to be in any kind of chronological order, it is difficult to make the distinction between old and new.
This article looks at several flags that are interesting from a user point of view. Each experiment is listed with its title and internal link at the top. You need to copy and paste the link into the address bar manually to get right to the preference on the flags' page.
Experimental Chrome flags
Mark non-secure origins as non-secure
Google considers marking all http websites that you visit in Chrome as insecure at one point in time. The flag allows you to enable this feature right now in the browser. You can set them to neutral, non-secure or dubious currently using the flag.
Enable extension toolbar redesign
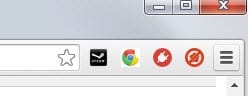
Google is working on a redesign of the extension toolbar currently. It is displayed to the right of the address bar.
If you enable the flag, extension icons are displayed for all installed extensions there.
Remember decisions to proceed through SSL errors for a specified length of time
Enable fast tab/window close
Save Page as MHTML
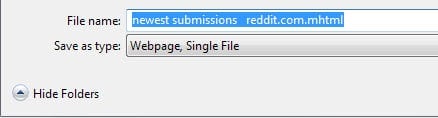
Instead of saving most web pages as multiple files that depend on each other, the web page is saved as a single file.
Enable Automatic Spelling Correction
Enable Download Resumption
Only Auto-Reload Visible Tabs
If you enable this feature, Chrome will only load visible tabs and not all of them.
Enable Developer Tools experiments
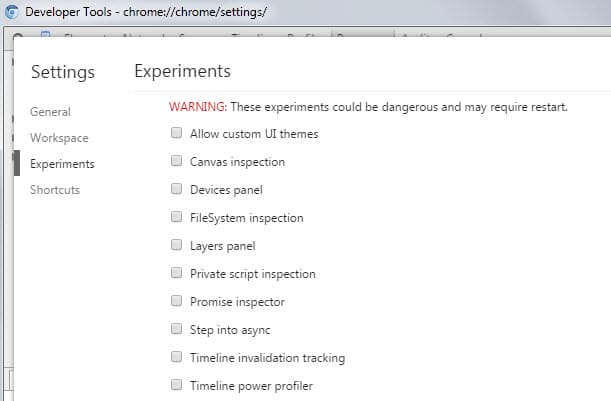
This enables a new option in the Chrome Developer Tool settings that you can use to enable experimental features there.
Source
The majority of settings that you find there are not yet ready for prime time. Some technologies may still be in active development, other features are tested by Google and made available to a wider audience through flags.
Since you find more than a hundred flags on the page at any time, it can be quite time consuming to go through all them regularly to find out what is new.
Since the flags don't appear to be in any kind of chronological order, it is difficult to make the distinction between old and new.
This article looks at several flags that are interesting from a user point of view. Each experiment is listed with its title and internal link at the top. You need to copy and paste the link into the address bar manually to get right to the preference on the flags' page.
Experimental Chrome flags
Mark non-secure origins as non-secure
- chrome://flags/#mark-non-secure-as

Google considers marking all http websites that you visit in Chrome as insecure at one point in time. The flag allows you to enable this feature right now in the browser. You can set them to neutral, non-secure or dubious currently using the flag.
Enable extension toolbar redesign
- chrome://flags/#enable-extension-action-redesign

Google is working on a redesign of the extension toolbar currently. It is displayed to the right of the address bar.
If you enable the flag, extension icons are displayed for all installed extensions there.
Remember decisions to proceed through SSL errors for a specified length of time
- chrome://flags/#remember-cert-error-decisions
Enable fast tab/window close
- chrome://flags/#enable-fast-unload
Save Page as MHTML
- chrome://flags/#save-page-as-mhtml

Instead of saving most web pages as multiple files that depend on each other, the web page is saved as a single file.
Enable Automatic Spelling Correction
- chrome://flags/#spellcheck-autocorrect
Enable Download Resumption
- chrome://flags/#enable-download-resumption
Only Auto-Reload Visible Tabs
- chrome://flags/#enable-offline-auto-reload-visible-only
If you enable this feature, Chrome will only load visible tabs and not all of them.
Enable Developer Tools experiments
- chrome://flags/#enable-devtools-experiments

This enables a new option in the Chrome Developer Tool settings that you can use to enable experimental features there.
Source